Top Related Projects
E-mails, subdomains and names Harvester - OSINT
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
WPScan WordPress security scanner. Written for security professionals and blog maintainers to test the security of their WordPress websites. Contact us via contact@wpscan.com
Nikto web server scanner
Directory/File, DNS and VHost busting tool written in Go
Nuclei is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Quick Overview
Sn1per is an automated reconnaissance and vulnerability scanning tool designed for penetration testers and security professionals. It combines various security tools and techniques to perform comprehensive scans on target systems, identifying potential vulnerabilities and providing detailed reports.
Pros
- Automates multiple scanning and enumeration processes, saving time and effort
- Integrates numerous popular security tools into a single platform
- Provides detailed reports and output for easy analysis
- Supports various scanning modes for different use cases (e.g., discovery, stealth, normal)
Cons
- May generate false positives, requiring manual verification
- Can be resource-intensive, especially for large-scale scans
- Requires careful use to avoid unintended impact on target systems
- Some features are only available in the paid professional version
Getting Started
To get started with Sn1per, follow these steps:
-
Clone the repository:
git clone https://github.com/1N3/Sn1per -
Navigate to the Sn1per directory:
cd Sn1per -
Install Sn1per:
bash install.sh -
Run a basic scan:
sniper -t <target>
Replace <target> with the IP address or domain name of the system you want to scan. Always ensure you have proper authorization before scanning any systems you don't own.
Note: Sn1per should be used responsibly and in compliance with all applicable laws and regulations. Unauthorized scanning or testing of systems is illegal and unethical.
Competitor Comparisons
E-mails, subdomains and names Harvester - OSINT
Pros of theHarvester
- Focused specifically on gathering open-source intelligence (OSINT)
- Lightweight and easy to use with minimal setup
- Supports a wide range of data sources for information gathering
Cons of theHarvester
- Limited in scope compared to Sn1per's comprehensive scanning capabilities
- Lacks advanced vulnerability assessment features
- May require additional tools for a complete security assessment
Code Comparison
theHarvester:
from theHarvester.discovery import *
from theHarvester.discovery.constants import *
search = googlesearch.search_google(word, limit, start)
search.process()
Sn1per:
sniper -t $TARGET -m $MODE -w $WORKSPACE
nmap -sV -p- -O --script=vulners $TARGET
theHarvester focuses on OSINT gathering using Python modules, while Sn1per provides a more comprehensive bash-based scanning approach that includes vulnerability assessment. theHarvester's code is more modular and easier to extend for specific OSINT tasks, whereas Sn1per offers a broader range of built-in scanning and enumeration capabilities.
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Pros of Social-Engineer-Toolkit
- Focused specifically on social engineering attacks, providing a comprehensive suite of tools for this purpose
- Regularly updated with new features and improvements
- Well-documented with extensive community support
Cons of Social-Engineer-Toolkit
- Limited in scope compared to Sn1per's broader range of security testing capabilities
- Requires more manual configuration and setup for certain attacks
- May have a steeper learning curve for beginners due to its specialized nature
Code Comparison
Social-Engineer-Toolkit:
# Example of a phishing attack setup
choice = input("Select attack vector: ")
if choice == "1":
site = input("Enter site to clone: ")
clone_site(site)
Sn1per:
# Example of running a full scan
sniper -t example.com -m fullportonly
The code snippets demonstrate the different focus areas of each tool. Social-Engineer-Toolkit emphasizes user interaction for social engineering attacks, while Sn1per provides a more automated approach to comprehensive security scanning.
WPScan WordPress security scanner. Written for security professionals and blog maintainers to test the security of their WordPress websites. Contact us via contact@wpscan.com
Pros of WPScan
- Specialized for WordPress security scanning, offering in-depth vulnerability detection
- Regularly updated with the latest WordPress vulnerabilities
- Lightweight and easy to use, focusing on a single purpose
Cons of WPScan
- Limited to WordPress sites, lacking versatility for other platforms
- Requires manual interpretation of results, less automated than Sn1per
- May miss broader infrastructure vulnerabilities outside of WordPress
Code Comparison
WPScan (Ruby):
def scan_wordpress_version
response = Browser.get(url)
if response.body =~ /meta name="generator" content="WordPress #{wp_version}"/i
puts "[+] WordPress version #{wp_version} detected"
end
end
Sn1per (Bash):
sniper(){
case "$MODE" in
normal)
discover
port_scan
web_scan
;;
stealth)
discover
port_scan
;;
esac
}
WPScan focuses specifically on WordPress version detection and vulnerability scanning, while Sn1per offers a broader range of reconnaissance and scanning capabilities for various targets and technologies.
Nikto web server scanner
Pros of Nikto
- Lightweight and easy to use, with a focus on web server scanning
- Extensive plugin system for customization and extensibility
- Well-established and widely used in the security community
Cons of Nikto
- Limited scope compared to Sn1per's comprehensive scanning capabilities
- Less frequent updates and potentially slower development cycle
- May require additional tools for a complete security assessment
Code Comparison
Nikto (Perl):
sub nikto_headers {
my ($mark) = @_;
my %headers;
foreach my $header (split(/\n/, $mark->{'headers'})) {
my ($key, $value) = split(/:\s*/, $header, 2);
$headers{lc($key)} = $value;
}
return %headers;
}
Sn1per (Bash):
sniper(){
if [[ "$REPORT" = "1" ]]; then
args="$args -o"
fi
if [[ "$OSINT" = "1" ]]; then
args="$args -re"
fi
sniper $args $TARGET
}
The code snippets demonstrate the different approaches: Nikto uses Perl for header parsing, while Sn1per employs Bash for argument handling and command execution.
Directory/File, DNS and VHost busting tool written in Go
Pros of gobuster
- Focused tool for directory/file enumeration and DNS subdomain discovery
- Written in Go, offering cross-platform compatibility and easy installation
- Lightweight and fast execution
Cons of gobuster
- Limited scope compared to Sn1per's comprehensive scanning capabilities
- Lacks advanced reporting and visualization features
- Does not include automated exploitation or post-exploitation modules
Code Comparison
gobuster (main.go):
func main() {
globalopts, err := parseGlobalOpts()
if err != nil {
fmt.Fprintf(os.Stderr, "%v\n", err)
os.Exit(1)
}
if globalopts.NoColor {
nocolorizer.SetupNoColor()
}
// ... (additional code)
}
Sn1per (sniper):
#!/bin/bash
# Install script for Sn1per
# Created by @xer0dayz - https://sn1persecurity.com
OKBLUE='\033[94m'
OKRED='\033[91m'
OKGREEN='\033[92m'
OKORANGE='\033[93m'
RESET='\e[0m'
echo -e "$OKRED ____ $RESET"
# ... (additional ASCII art and installation code)
The code comparison shows that gobuster is written in Go, focusing on efficient directory enumeration, while Sn1per is a Bash script that orchestrates various tools for comprehensive scanning and exploitation.
Nuclei is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Pros of Nuclei
- Highly extensible with a large community-contributed template library
- Fast and efficient scanning with multi-threading support
- Easy-to-write YAML-based templates for custom vulnerability checks
Cons of Nuclei
- Requires more manual configuration and template selection
- Less comprehensive out-of-the-box scanning compared to Sn1per
- Steeper learning curve for creating custom templates
Code Comparison
Sn1per (Bash script):
sniper -t $TARGET -m $MODE -w $WORKSPACE
Nuclei (CLI command):
nuclei -t nuclei-templates -u https://example.com
Both tools offer command-line interfaces, but Nuclei's approach is more modular, allowing users to specify template directories and target URLs separately. Sn1per's single command encompasses multiple scanning modes and workspace management.
Nuclei's template-based approach provides greater flexibility for customization:
id: example-vulnerability
info:
name: Example Vulnerability Check
severity: medium
requests:
- method: GET
path:
- "{{BaseURL}}/vulnerable-endpoint"
matchers:
- type: word
words:
- "vulnerable response"
This YAML structure allows for easy creation and sharing of vulnerability checks within the community.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
[Website] [Blog] [Shop] [Documentation] [Demo] [Find Out More]
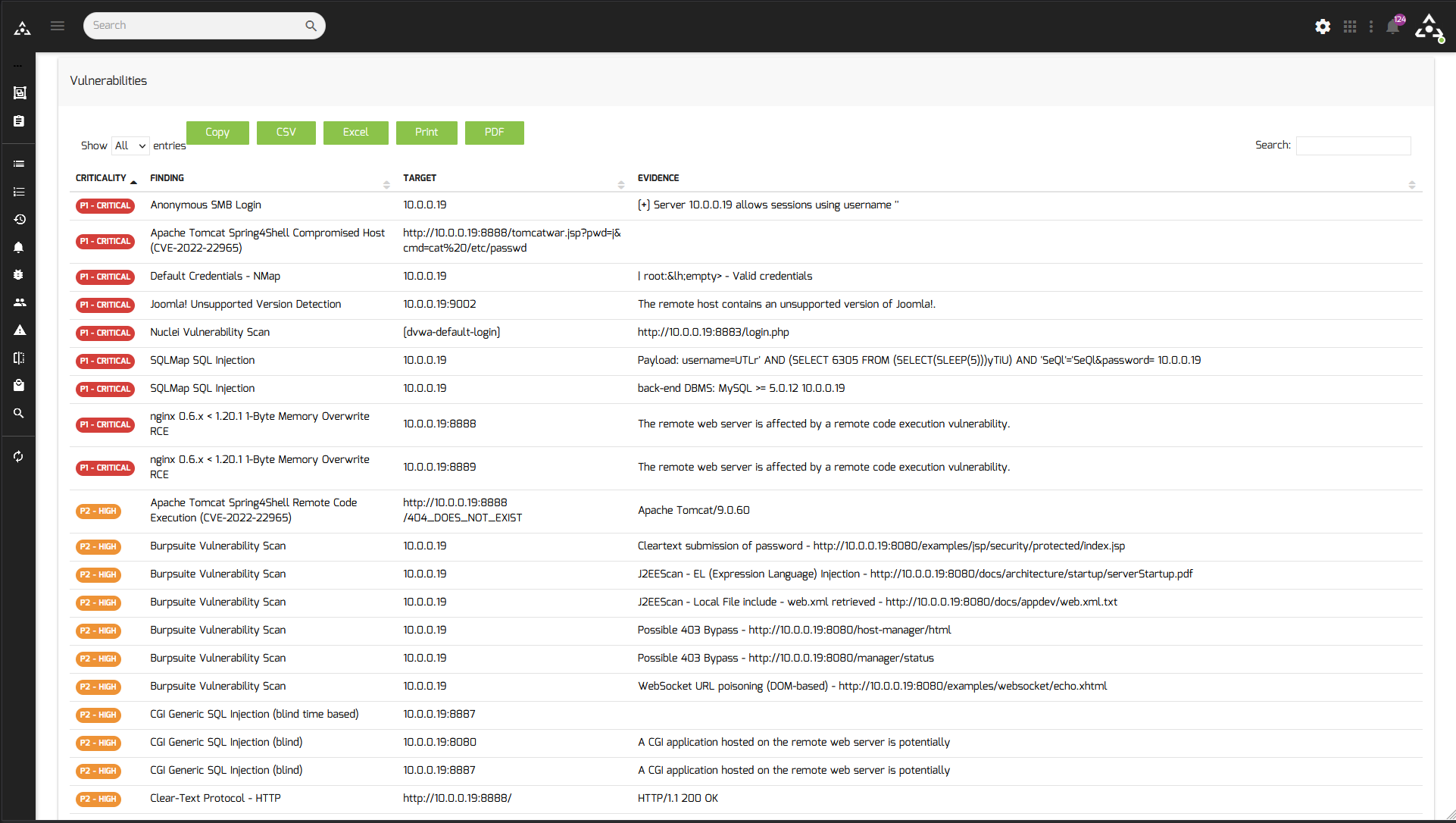
Attack Surface Management Platform
Discover hidden assets and vulnerabilities in your environment
[Find out more]
The ultimate pentesting toolkit
Integrate with the leading commercial and open source vulnerability scanners to scan for the latest CVEs and vulnerabilities.
Automate the most powerful tools
Security tools are expensive and time-consuming, but with Sn1per, you can save time by automating the execution of these open source and commercial tools to discover vulnerabilities across your entire attack surface.
Find what you can't see
Hacking is a problem that's only getting worse. But, with Sn1per, you can find what you canât seeâhidden assets and vulnerabilities in your environment.
Discover and prioritize risks in your organization
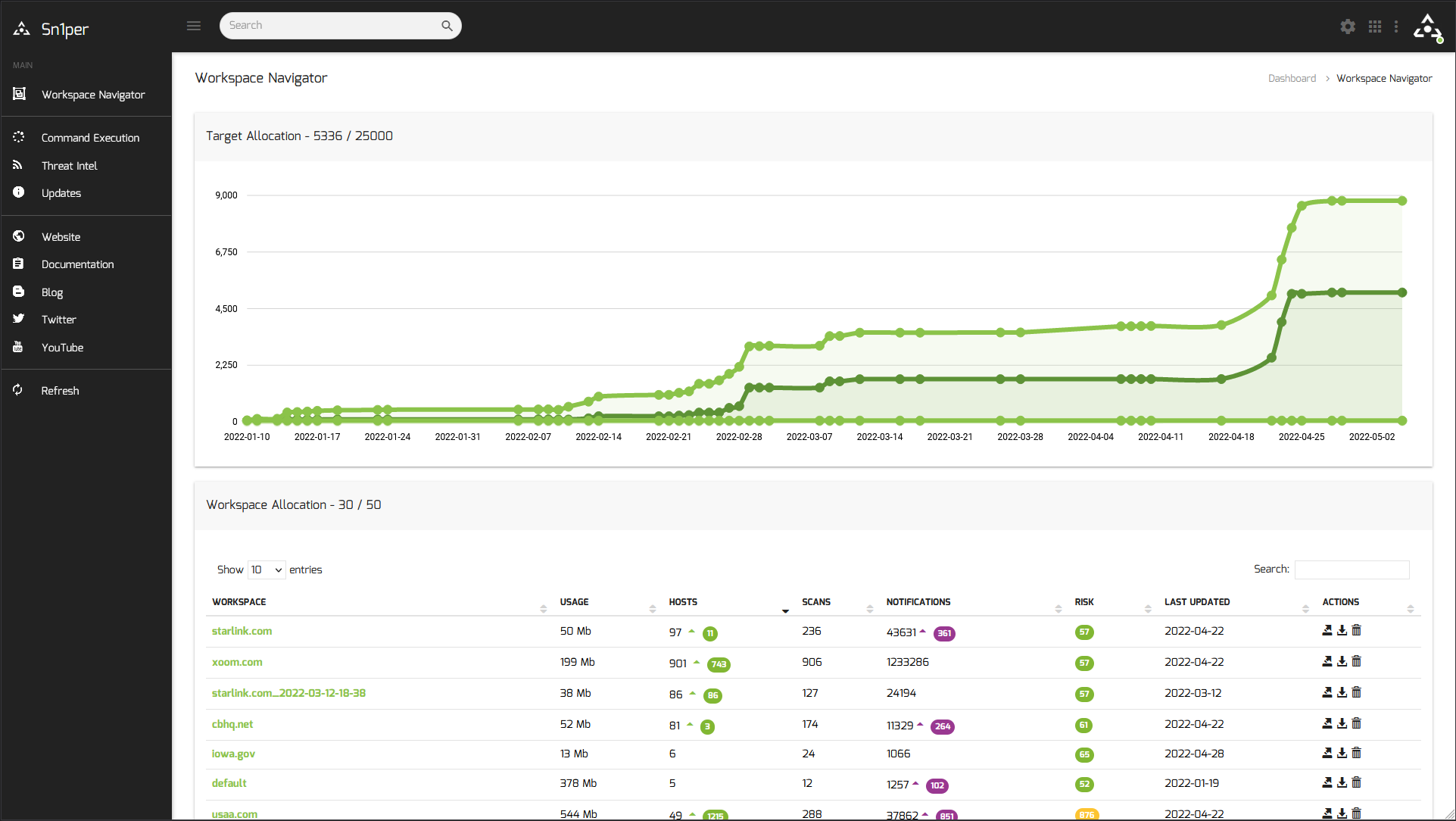
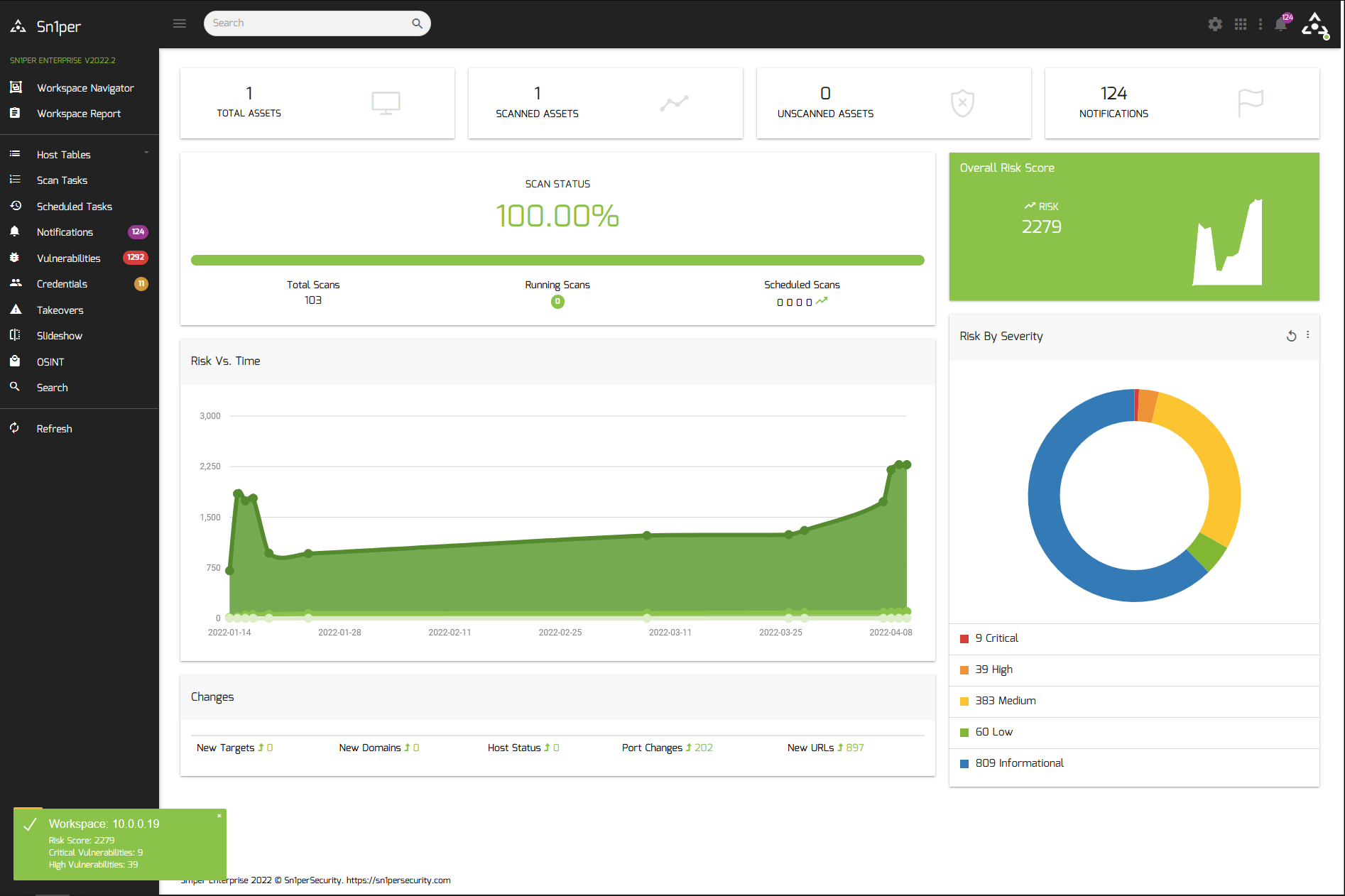
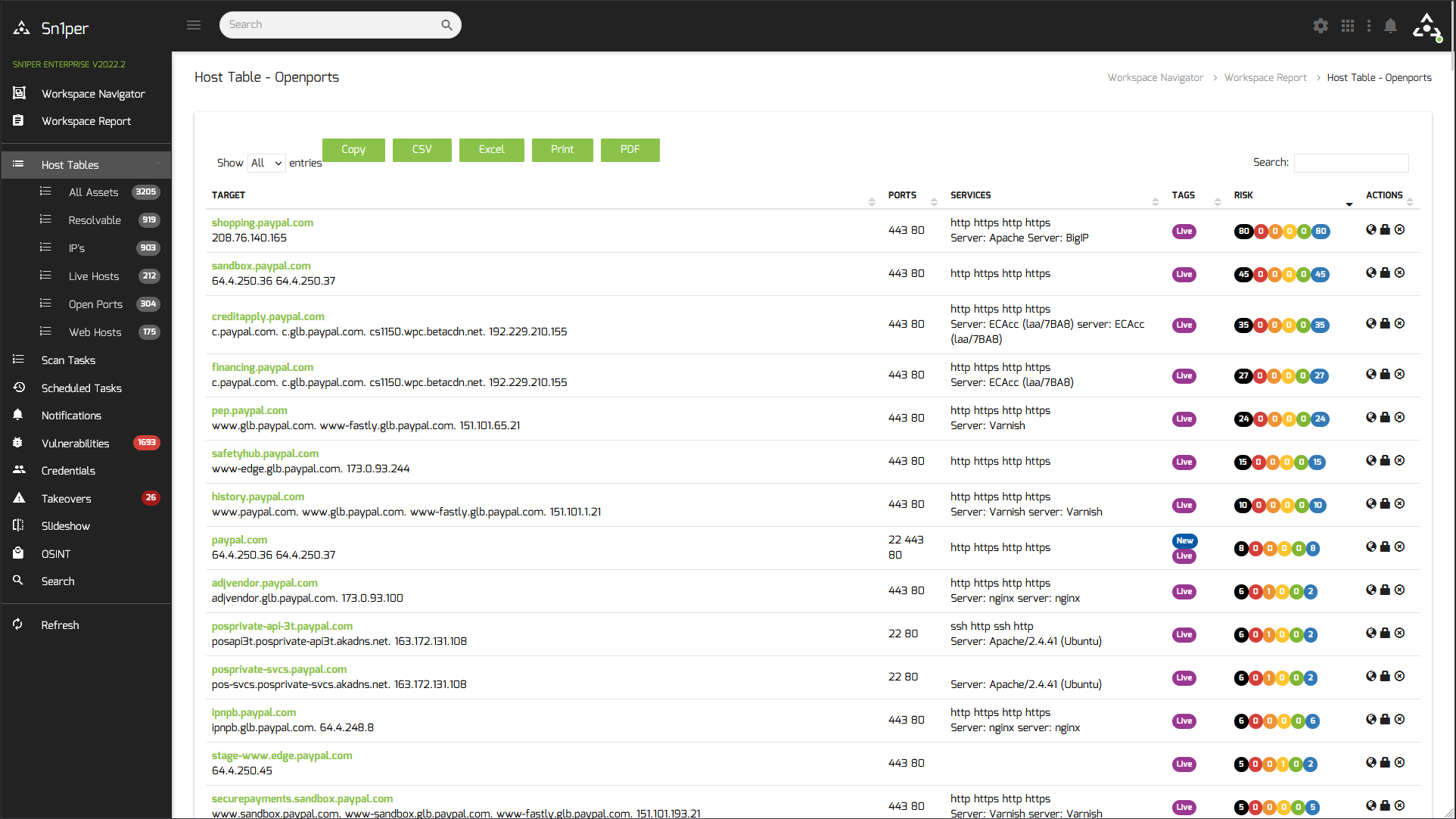
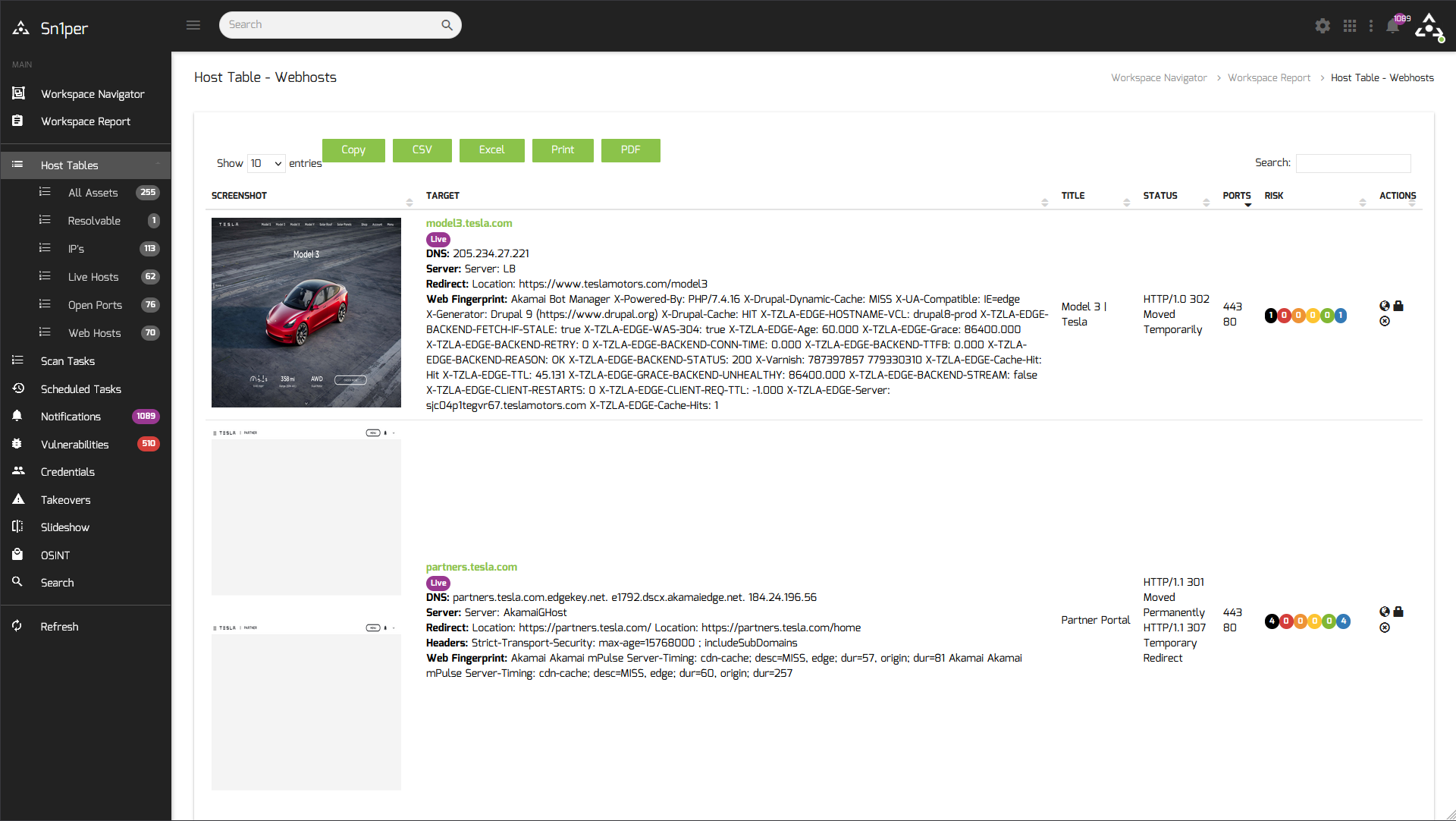
Sn1per is a next-generation information gathering tool that provides automated, deep, and continuous security for organizations of all sizes.
See Sn1per in action
News
-
ð Sn1per Enterprise v20250522 Released â Next-Level Offensive Security & Vulnerability Scanning
-
Sn1per SE v10.8 Now Available â New Features, Tools & Enhancements!
-
Sn1per Enterprise Released!
-
Sn1per Professional v10.0 Released!
Kali/Ubuntu/Debian/Parrot Linux Install
git clone https://github.com/1N3/Sn1per
cd Sn1per
bash install.sh
AWS AMI (Free Tier) VPS Install
To install Sn1per using an AWS EC2 instance:
- Go to https://aws.amazon.com/marketplace/pp/prodview-rmloab6wnymno and click the âContinue to Subscribeâ button
- Click the âContinue to Configurationâ button
- Click the âContinue to Launchâ button
- Login via SSH using the public IP of the new EC2 instance
Docker Install
Kali Linux-based Sn1per
-
Run the Docker Compose file
sudo docker compose up -
Run the container
sudo docker run --privileged -it sn1per-kali-linux /bin/bash
BlackArch-based Sn1per
-
Run the Docker Compose file
sudo docker compose -f docker-compose-blackarch.yml up -
Run the container
sudo docker run --privileged -it sn1per-blackarch /bin/bash
Usage
[*] NORMAL MODE
sniper -t <TARGET>
[*] NORMAL MODE + OSINT + RECON
sniper -t <TARGET> -o -re
[*] STEALTH MODE + OSINT + RECON
sniper -t <TARGET> -m stealth -o -re
[*] DISCOVER MODE
sniper -t <CIDR> -m discover -w <WORSPACE_ALIAS>
[*] SCAN ONLY SPECIFIC PORT
sniper -t <TARGET> -m port -p <portnum>
[*] FULLPORTONLY SCAN MODE
sniper -t <TARGET> -fp
[*] WEB MODE - PORT 80 + 443 ONLY!
sniper -t <TARGET> -m web
[*] HTTP WEB PORT MODE
sniper -t <TARGET> -m webporthttp -p <port>
[*] HTTPS WEB PORT MODE
sniper -t <TARGET> -m webporthttps -p <port>
[*] HTTP WEBSCAN MODE
sniper -t <TARGET> -m webscan
[*] ENABLE BRUTEFORCE
sniper -t <TARGET> -b
[*] AIRSTRIKE MODE
sniper -f targets.txt -m airstrike
[*] NUKE MODE WITH TARGET LIST, BRUTEFORCE ENABLED, FULLPORTSCAN ENABLED, OSINT ENABLED, RECON ENABLED, WORKSPACE & LOOT ENABLED
sniper -f targets.txt -m nuke -w <WORKSPACE_ALIAS>
[*] MASS PORT SCAN MODE
sniper -f targets.txt -m massportscan
[*] MASS WEB SCAN MODE
sniper -f targets.txt -m massweb
[*] MASS WEBSCAN SCAN MODE
sniper -f targets.txt -m masswebscan
[*] MASS VULN SCAN MODE
sniper -f targets.txt -m massvulnscan
[*] PORT SCAN MODE
sniper -t <TARGET> -m port -p <PORT_NUM>
[*] LIST WORKSPACES
sniper --list
[*] DELETE WORKSPACE
sniper -w <WORKSPACE_ALIAS> -d
[*] DELETE HOST FROM WORKSPACE
sniper -w <WORKSPACE_ALIAS> -t <TARGET> -dh
[*] GET SNIPER SCAN STATUS
sniper --status
[*] LOOT REIMPORT FUNCTION
sniper -w <WORKSPACE_ALIAS> --reimport
[*] LOOT REIMPORTALL FUNCTION
sniper -w <WORKSPACE_ALIAS> --reimportall
[*] LOOT REIMPORT FUNCTION
sniper -w <WORKSPACE_ALIAS> --reload
[*] LOOT EXPORT FUNCTION
sniper -w <WORKSPACE_ALIAS> --export
[*] SCHEDULED SCANS
sniper -w <WORKSPACE_ALIAS> -s daily|weekly|monthly
[*] USE A CUSTOM CONFIG
sniper -c /path/to/sniper.conf -t <TARGET> -w <WORKSPACE_ALIAS>
[*] UPDATE SNIPER
sniper -u|--update
Modes
-
NORMAL: Performs basic scan of targets and open ports using both active and passive checks for optimal performance.
-
STEALTH: Quickly enumerate single targets using mostly non-intrusive scans to avoid WAF/IPS blocking.
-
FLYOVER: Fast multi-threaded high level scans of multiple targets (useful for collecting high level data on many hosts quickly).
-
AIRSTRIKE: Quickly enumerates open ports/services on multiple hosts and performs basic fingerprinting. To use, specify the full location of the file which contains all hosts, IPs that need to be scanned and run ./sn1per /full/path/to/targets.txt airstrike to begin scanning.
-
NUKE: Launch full audit of multiple hosts specified in text file of choice. Usage example: ./sniper /pentest/loot/targets.txt nuke.
-
DISCOVER: Parses all hosts on a subnet/CIDR (ie. 192.168.0.0/16) and initiates a sniper scan against each host. Useful for internal network scans.
-
PORT: Scans a specific port for vulnerabilities. Reporting is not currently available in this mode.
-
FULLPORTONLY: Performs a full detailed port scan and saves results to XML.
-
MASSPORTSCAN: Runs a "fullportonly" scan on multiple targets specified via the "-f" switch.
-
WEB: Adds full automatic web application scans to the results (port 80/tcp & 443/tcp only). Ideal for web applications but may increase scan time significantly.
-
MASSWEB: Runs "web" mode scans on multiple targets specified via the "-f" switch.
-
WEBPORTHTTP: Launches a full HTTP web application scan against a specific host and port.
-
WEBPORTHTTPS: Launches a full HTTPS web application scan against a specific host and port.
-
WEBSCAN: Launches a full HTTP & HTTPS web application scan against via Burpsuite and Arachni.
-
MASSWEBSCAN: Runs "webscan" mode scans of multiple targets specified via the "-f" switch.
-
VULNSCAN: Launches a OpenVAS vulnerability scan.
-
MASSVULNSCAN: Launches a "vulnscan" mode scans on multiple targets specified via the "-f" switch.
Help Topics
- Plugins & Tools
- Scheduled Scans
- Sn1per Configuration Options
- Sn1per Configuration Templates
- Sc0pe Templates
Integration Guides
- Github API integration
- Burpsuite Professional 2.x integration
- OWASP ZAP integration
- Shodan API integration
- Censys API integration
- Hunter.io API integration
- Metasploit integration
- Nessus integration
- OpenVAS API integration
- GVM 21.x integration
- Slack API integration
- WPScan API integration
License & Legal Agreement
For license and legal information, refer to the LICENSE.md file in this repository.
Purchase Sn1per Professional
To obtain a Sn1per Professional license, go to https://sn1persecurity.com.
External attack surface management, Attack surface monitoring, Attack Surface Management Platform, Attack Surface Management Solutions, Vulnerability management, Threat intelligence, Cybersecurity risk assessment, Security posture assessment, Digital footprint analysis, Attack surface mapping, Web application security, Network security, Infrastructure security, Cloud security, Third-party risk management, Incident response, Penetration testing, Asset discovery, Patch management, Security scanning, Firewall configuration, Intrusion detection system, Security awareness training, Data breach prevention, Web server security, Endpoint security, Phishing protection, Vulnerability assessment, Network security, Web application testing, Ethical hacking, Security assessment, Information security, Red teaming, Cybersecurity testing, Pen testing tools, Exploitation techniques, Wireless network testing, Social engineering, Security auditing, Incident response, Intrusion detection, Firewall testing, Security assessment methodology, Risk assessment, Security controls, Web vulnerability scanning, Password cracking, Security testing services, Security architecture, System hardening, Network reconnaissance, Red teaming, Penetration testing, Cybersecurity, Vulnerability assessment, Attack simulation, Threat intelligence, Risk assessment, Security testing, Adversarial tactics, Incident response, Security assessment, Network security, Defensive measures, Security controls, Social engineering, Exploitation techniques, Security awareness, Defensive strategies, Risk mitigation, Blue teaming, Security operations, Intrusion detection, Security frameworks, Cyber defense, Information security
Top Related Projects
E-mails, subdomains and names Harvester - OSINT
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
WPScan WordPress security scanner. Written for security professionals and blog maintainers to test the security of their WordPress websites. Contact us via contact@wpscan.com
Nikto web server scanner
Directory/File, DNS and VHost busting tool written in Go
Nuclei is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot