 ROPgadget
ROPgadget
This tool lets you search your gadgets on your binaries to facilitate your ROP exploitation. ROPgadget supports ELF, PE and Mach-O format on x86, x64, ARM, ARM64, PowerPC, SPARC, MIPS, RISC-V 64, and RISC-V Compressed architectures.
Top Related Projects
Display information about files in different file formats and find gadgets to build rop chains for different architectures (x86/x86_64, ARM/ARM64, MIPS, PowerPC, SPARC64). For disassembly ropper uses the awesome Capstone Framework.
rp++ is a fast C++ ROP gadget finder for PE/ELF/Mach-O x86/x64/ARM/ARM64 binaries.
PEDA - Python Exploit Development Assistance for GDB
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging capabilities for exploit devs & reverse engineers on Linux
Quick Overview
ROPgadget is a tool designed to search for gadgets in binary files to facilitate Return-Oriented Programming (ROP) exploits. It supports various architectures and file formats, making it a versatile tool for security researchers and penetration testers. ROPgadget can also generate ROP chains for common operations like executing shell commands.
Pros
- Supports multiple architectures (x86, x86-64, ARM, ARM64, MIPS, PowerPC, and SPARC)
- Can handle various file formats (ELF, PE, Mach-O, Raw)
- Provides options for customizing gadget search and output
- Capable of generating ROP chains automatically for common operations
Cons
- May produce a large number of gadgets, requiring manual filtering for specific exploits
- Limited to static analysis, which may miss some runtime-dependent gadgets
- Requires a good understanding of assembly and ROP techniques to use effectively
- Performance can be slow on large binaries or when searching for complex gadgets
Getting Started
To get started with ROPgadget:
- Install ROPgadget:
pip install ropgadget
- Basic usage to find gadgets in a binary:
ROPgadget --binary /path/to/binary
- Generate a ROP chain to execute /bin/sh:
ROPgadget --binary /path/to/binary --ropchain
- Search for specific gadgets:
ROPgadget --binary /path/to/binary --string "pop rdi"
For more advanced usage and options, refer to the project's documentation on GitHub.
Competitor Comparisons
Display information about files in different file formats and find gadgets to build rop chains for different architectures (x86/x86_64, ARM/ARM64, MIPS, PowerPC, SPARC64). For disassembly ropper uses the awesome Capstone Framework.
Pros of Ropper
- Supports more file formats, including raw binary files
- Offers a semantic search feature for finding gadgets based on their functionality
- Provides a command-line interface and a Python API for better integration
Cons of Ropper
- May have a steeper learning curve due to more advanced features
- Can be slower when processing large binaries compared to ROPgadget
- Less frequent updates and potentially fewer contributors
Code Comparison
ROPgadget:
from ROPGadget.args import Args
from ROPGadget.core import Core
args = Args().getArgs()
Core(args).analyze()
Ropper:
from ropper import RopperService
rs = RopperService()
rs.addFile('binary')
rs.loadGadgets()
gadgets = rs.search(search='pop rdi')
Both tools provide Python APIs for integration into custom scripts. ROPgadget offers a simpler interface, while Ropper provides more granular control over the gadget search process. Ropper's API allows for more specific searches and better integration with other tools or workflows.
rp++ is a fast C++ ROP gadget finder for PE/ELF/Mach-O x86/x64/ARM/ARM64 binaries.
Pros of rp
- Written in Rust, offering better performance and memory safety
- Supports a wider range of architectures, including ARM64
- More actively maintained with frequent updates
Cons of rp
- Less comprehensive documentation compared to ROPgadget
- Fewer built-in features for ROP chain generation
- Steeper learning curve for users new to Rust-based tools
Code Comparison
ROPgadget:
def searchOpcode(self, opcodes):
for gadget in self.gadgets:
opcode = gadget["bytes"]
if opcode.startswith(opcodes):
print(gadget["gadget"])
rp:
pub fn find_gadgets(&self, binary: &Binary) -> Vec<Gadget> {
let mut gadgets = Vec::new();
for section in binary.sections() {
if section.is_executable() {
self.find_gadgets_in_section(§ion, &mut gadgets);
}
}
gadgets
}
The code snippets show different approaches to gadget searching. ROPgadget uses Python and focuses on opcode matching, while rp utilizes Rust's performance benefits and implements a more structured approach by iterating through executable sections.
Both tools serve similar purposes but cater to different user preferences and requirements. ROPgadget offers simplicity and ease of use, while rp provides enhanced performance and broader architecture support at the cost of a steeper learning curve.
PEDA - Python Exploit Development Assistance for GDB
Pros of PEDA
- Provides a more comprehensive debugging environment with enhanced GDB features
- Offers colorized and user-friendly output for easier analysis
- Includes built-in commands for common exploit development tasks
Cons of PEDA
- Limited to GDB and not as portable as ROPgadget
- May have a steeper learning curve for users unfamiliar with GDB
- Focuses more on general debugging rather than specific ROP chain creation
Code Comparison
PEDA (Python Exploit Development Assistance for GDB):
def ropgadget(start, end, keyword):
result = []
for addr in range(start, end):
insn = disassemble(addr, 1)
if keyword in insn:
result.append(insn)
return result
ROPgadget:
def searchOpcode(binary, opcode):
sections = binary.getExecSections()
for section in sections:
data = section.getData()
offset = data.find(opcode)
while offset != -1:
yield section.getOffset() + offset
offset = data.find(opcode, offset + 1)
Both tools aim to assist in exploit development, but PEDA is more focused on enhancing the GDB experience, while ROPgadget specializes in finding ROP gadgets across various architectures and file formats.
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging capabilities for exploit devs & reverse engineers on Linux
Pros of GEF
- More comprehensive debugging features, including memory analysis and exploit development tools
- Integrates seamlessly with GDB, providing an enhanced debugging experience
- Supports multiple architectures and file formats
Cons of GEF
- Steeper learning curve due to its extensive feature set
- Requires GDB to function, limiting its portability
- May be overkill for simple ROP chain analysis tasks
Code Comparison
GEF example:
gef➤ ropper --search "pop rdi"
0x00000000004011fb : pop rdi ; ret
ROPgadget example:
$ ROPgadget --binary ./binary --ropchain
[+] ROP chain generation
pop rdi ; ret = 0x4011fb
Summary
GEF offers a more comprehensive debugging environment with extensive features, while ROPgadget focuses specifically on ROP chain generation and analysis. GEF integrates with GDB, providing a powerful toolset for exploit development, but may be more complex for simple tasks. ROPgadget, on the other hand, is more lightweight and portable, making it ideal for quick ROP chain analysis. The choice between the two depends on the specific needs of the user and the complexity of the task at hand.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
ROPgadget Tool
This tool lets you search your gadgets on your binaries to facilitate your ROP exploitation. ROPgadget supports ELF/PE/Mach-O/Raw formats on x86, x64, ARM, ARM64, PowerPC, SPARC, MIPS, RISC-V 64, and RISC-V Compressed architectures.
Install
The easiest way is installing ROPgadget from PyPi:
$ sudo apt install python3-pip
$ sudo -H python3 -m pip install ROPgadget
$ ROPgadget --help
Alternatively you can install ROPgadget from source. You have to install Capstone first.
For the Capstone's installation on nix machine:
$ sudo apt install python3-pip
$ sudo -H python3 -m pip install capstone
Capstone supports multi-platforms (windows, ios, android, cygwin...). For the cross-compilation, please refer to the https://github.com/capstone-engine/capstone/blob/master/COMPILE.TXT file.
After Capstone is installed, ROPgadget can be used as a standalone tool:
$ python3 ROPgadget.py --help
Or installed into the Python site-packages library, and executed from $PATH.
$ sudo -H python3 setup.py install
$ ROPgadget --help
Usage
usage: ROPgadget.py [-h] [-v] [-c] [--binary <binary>] [--opcode <opcodes>]
[--string <string>] [--memstr <string>] [--depth <nbyte>]
[--only <key>] [--filter <key>] [--range <start-end>]
[--badbytes <byte>] [--rawArch <arch>] [--rawMode <mode>]
[--rawEndian <endian>] [--re <re>] [--offset <hexaddr>]
[--ropchain] [--thumb] [--console] [--norop] [--nojop]
[--callPreceded] [--nosys] [--multibr] [--all] [--noinstr]
[--dump] [--silent] [--align ALIGN] [--mipsrop <rtype>]
description:
ROPgadget lets you search your gadgets on a binary. It supports several
file formats and architectures and uses the Capstone disassembler for
the search engine.
formats supported:
- ELF
- PE
- Mach-O
- Raw
architectures supported:
- x86
- x86-64
- ARM
- ARM64
- MIPS
- PowerPC
- Sparc
- RISC-V 64
- RISC-V Compressed
optional arguments:
-h, --help show this help message and exit
-v, --version Display the ROPgadget's version
-c, --checkUpdate Checks if a new version is available
--binary <binary> Specify a binary filename to analyze
--opcode <opcodes> Search opcode in executable segment
--string <string> Search string in readable segment
--memstr <string> Search each byte in all readable segment
--depth <nbyte> Depth for search engine (default 10)
--only <key> Only show specific instructions
--filter <key> Suppress specific mnemonics
--range <start-end> Search between two addresses (0x...-0x...)
--badbytes <byte> Rejects specific bytes in the gadget's address
--rawArch <arch> Specify an arch for a raw file
x86|arm|arm64|sparc|mips|ppc|riscv
--rawMode <mode> Specify a mode for a raw file 32|64|arm|thumb
--rawEndian <endian> Specify an endianness for a raw file little|big
--re <re> Regular expression
--offset <hexaddr> Specify an offset for gadget addresses
--ropchain Enable the ROP chain generation
--thumb Use the thumb mode for the search engine (ARM only)
--console Use an interactive console for search engine
--norop Disable ROP search engine
--nojop Disable JOP search engine
--callPreceded Only show gadgets which are call-preceded
--nosys Disable SYS search engine
--multibr Enable multiple branch gadgets
--all Disables the removal of duplicate gadgets
--noinstr Disable the gadget instructions console printing
--dump Outputs the gadget bytes
--silent Disables printing of gadgets during analysis
--align ALIGN Align gadgets addresses (in bytes)
--mipsrop <rtype> MIPS useful gadgets finder
stackfinder|system|tails|lia0|registers
examples:
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --ropchain
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --depth 3
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --string "main"
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --string "m..n"
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --opcode c9c3
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --only "mov|ret"
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --only "mov|pop|xor|ret"
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --filter "xchg|add|sub|cmov.*"
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --norop --nosys
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --range 0x08041000-0x08042000
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --string main --range 0x080c9aaa-0x080c9aba
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --memstr "/bin/sh"
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --console
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-x86 --badbytes "00|01-1f|7f|42"
ROPgadget.py --binary ./test-suite-binaries/Linux_lib64.so --offset 0xdeadbeef00000000
ROPgadget.py --binary ./test-suite-binaries/elf-ARMv7-ls --depth 5
ROPgadget.py --binary ./test-suite-binaries/elf-ARM64-bash --depth 5
ROPgadget.py --binary ./test-suite-binaries/raw-x86.raw --rawArch=x86 --rawMode=32
ROPgadget.py --binary ./test-suite-binaries/elf-Linux-RISCV_64 --depth 8
How can I contribute ?
- Add system gadgets for PPC, Sparc, ARM64 (Gadgets.addSYSGadgets()).
- Support RISC-V 32-bit.
- Handle bad bytes in data during ROP chain generation.
- Manage big endian in Mach-O format like the ELF class.
- Everything you think is cool :)
Bugs/Patches/Contact
Please, report bugs, submit pull requests, etc. on GitHub at https://github.com/JonathanSalwan/ROPgadget
License
See LICENSE_BSD.txt and the license header on all source files.
Screenshots
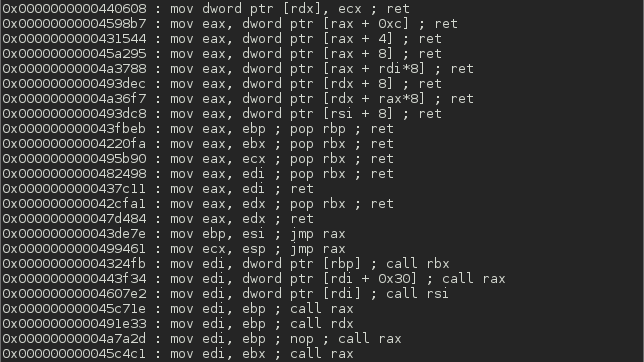
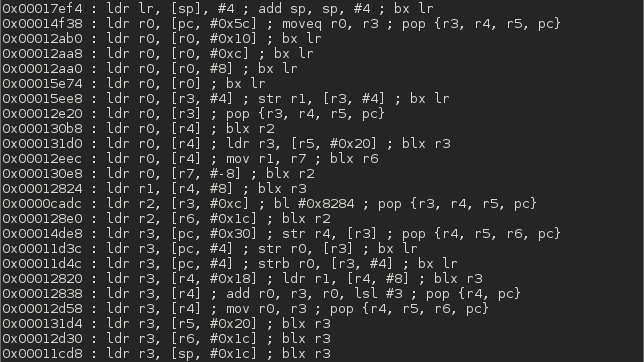
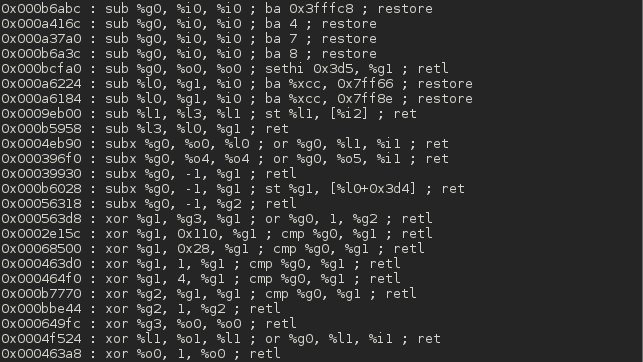
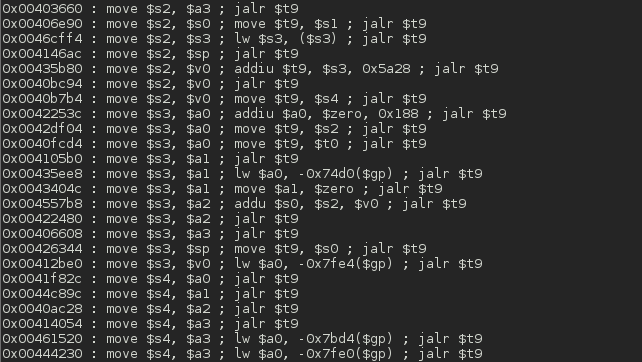
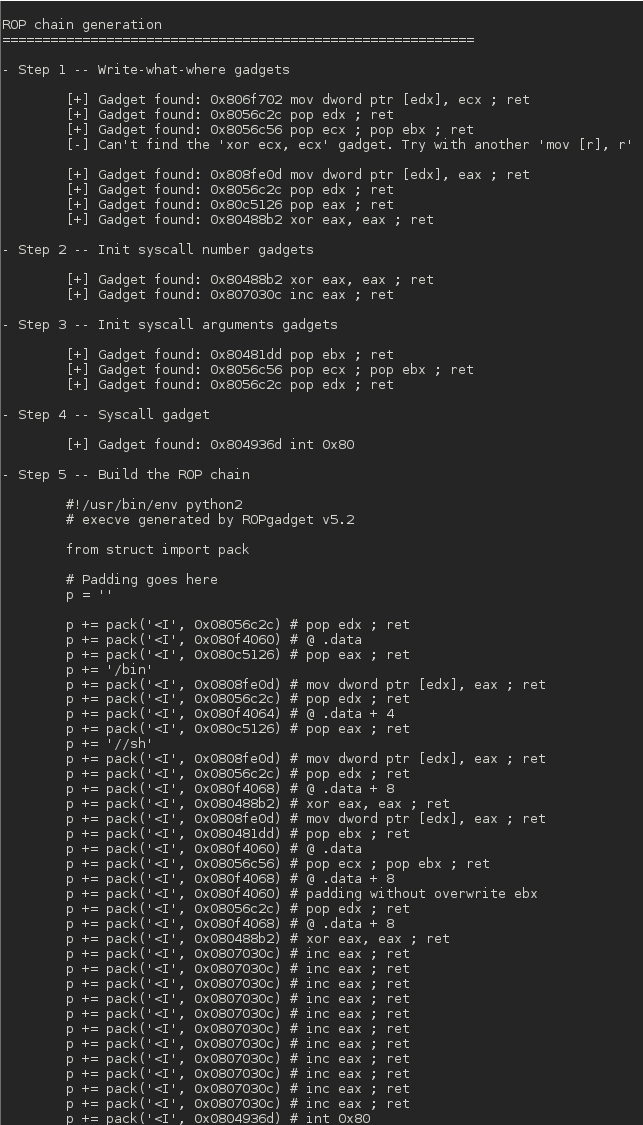
Top Related Projects
Display information about files in different file formats and find gadgets to build rop chains for different architectures (x86/x86_64, ARM/ARM64, MIPS, PowerPC, SPARC64). For disassembly ropper uses the awesome Capstone Framework.
rp++ is a fast C++ ROP gadget finder for PE/ELF/Mach-O x86/x64/ARM/ARM64 binaries.
PEDA - Python Exploit Development Assistance for GDB
GEF (GDB Enhanced Features) - a modern experience for GDB with advanced debugging capabilities for exploit devs & reverse engineers on Linux
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot