Top Related Projects
AFWall+ (Android Firewall +) - iptables based firewall for Android
Using system APIs directly with adb/root privileges from normal apps through a Java process started with app_process.
Gnirehtet provides reverse tethering for Android
The Github home of Orbot: Tor on Android (Also available on gitlab!)
Quick Overview
NetGuard is an open-source Android application that provides a firewall and VPN service to control network access on Android devices. It allows users to block or allow specific apps from accessing the internet, and can also be used to create a VPN tunnel to route all network traffic through a secure connection.
Pros
- Granular Control: NetGuard offers fine-grained control over network access, allowing users to block or allow specific apps and services.
- Secure VPN: The built-in VPN feature provides a secure tunnel for all network traffic, protecting user data from potential eavesdropping.
- Open-Source: As an open-source project, NetGuard benefits from community contributions and transparency.
- Actively Maintained: The project is actively maintained, with regular updates and bug fixes.
Cons
- Android-Only: NetGuard is designed specifically for Android devices and does not have support for other platforms.
- Complexity: The app's extensive features and customization options may be overwhelming for some users, especially those who are less tech-savvy.
- Battery Drain: The VPN feature can potentially increase battery consumption on the device, which may be a concern for some users.
- Limited Compatibility: Some users have reported compatibility issues with certain Android devices or versions.
Code Examples
N/A (This is not a code library)
Getting Started
To get started with NetGuard, follow these steps:
- Download the NetGuard app from the Google Play Store or the project's GitHub releases page.
- Open the app and grant the necessary permissions, such as allowing the app to create a VPN connection.
- Customize the app's settings to your preferences, such as selecting which apps to block or allow, and configuring the VPN settings.
- Enable the firewall or VPN feature to start controlling network access on your device.
For more detailed instructions and advanced configuration options, please refer to the project's documentation on the GitHub repository.
Competitor Comparisons
AFWall+ (Android Firewall +) - iptables based firewall for Android
Pros of AFWall+
- Offers more granular control over app-specific firewall rules
- Supports both WiFi and mobile data separately
- Includes profiles for different network configurations
Cons of AFWall+
- Requires root access, limiting its accessibility
- May have a steeper learning curve for non-technical users
- Can potentially impact battery life due to constant monitoring
Code Comparison
NetGuard uses a VPN-based approach:
private void startVpn() {
Intent intent = VpnService.prepare(this);
if (intent != null)
startActivityForResult(intent, REQUEST_VPN);
else
onActivityResult(REQUEST_VPN, RESULT_OK, null);
}
AFWall+ utilizes iptables for firewall rules:
private void applyIptablesRules() {
List<String> cmds = new ArrayList<String>();
cmds.add(IPTABLES_PATH + " -F " + CHAIN_NAME);
cmds.add(IPTABLES_PATH + " -A " + CHAIN_NAME + " -m owner --uid-owner " + uid + " -j " + targetRule);
executeCommands(cmds);
}
Both projects aim to provide network traffic control on Android devices, but they differ in their implementation approaches and target user bases. NetGuard focuses on a user-friendly, non-root solution, while AFWall+ offers more advanced features for rooted devices.
Using system APIs directly with adb/root privileges from normal apps through a Java process started with app_process.
Pros of Shizuku
- Provides a more flexible and powerful approach to system-level operations
- Supports a wider range of device management and customization features
- Offers better compatibility with newer Android versions and security models
Cons of Shizuku
- Requires more complex setup and configuration
- May have a steeper learning curve for users and developers
- Limited to devices with root access or ADB capabilities
Code Comparison
NetGuard (Java):
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
// Initialize network monitoring
}
Shizuku (Kotlin):
override fun onCreate(savedInstanceState: Bundle?) {
super.onCreate(savedInstanceState)
setContentView(R.layout.activity_main)
// Initialize Shizuku service connection
}
Both projects use similar Android lifecycle methods, but Shizuku's implementation in Kotlin offers more concise syntax. NetGuard focuses on network-level operations, while Shizuku provides a broader range of system-level functionalities. The code structures reflect their different purposes, with NetGuard likely containing more network-specific logic and Shizuku emphasizing service connections and system interactions.
Gnirehtet provides reverse tethering for Android
Pros of gnirehtet
- Provides reverse tethering functionality, allowing internet sharing from PC to Android
- Cross-platform support (Windows, macOS, Linux)
- Doesn't require root access on the Android device
Cons of gnirehtet
- Requires ADB (Android Debug Bridge) to be set up and enabled
- More complex setup process compared to NetGuard
- Limited to reverse tethering, while NetGuard offers broader network control features
Code Comparison
gnirehtet (Rust):
fn relay(tcp_client: TcpStream, selector: &mut Selector) -> io::Result<()> {
let stream = Arc::new(TcpStream::from_stream(tcp_client)?);
stream.set_nonblocking(true)?;
// ... (additional code)
}
NetGuard (Java):
private void handlePacket(Packet packet) {
try {
if (packet.udp) {
handleUdp(packet);
} else {
handleTcp(packet);
}
} catch (Exception e) {
Log.e(TAG, "Handle packet error");
}
}
The code snippets showcase different approaches: gnirehtet focuses on relay functionality using Rust, while NetGuard handles packet processing in Java, reflecting their distinct purposes and implementations.
The Github home of Orbot: Tor on Android (Also available on gitlab!)
Pros of Orbot
- Provides Tor anonymity for all internet traffic on Android devices
- Offers a wider range of privacy features, including bridges and pluggable transports
- Integrates with other apps to route their traffic through Tor
Cons of Orbot
- More complex setup and configuration process
- May slow down internet speeds due to Tor routing
- Requires root access for some features
Code Comparison
NetGuard uses a VpnService to filter traffic:
@Override
public int onStartCommand(Intent intent, int flags, int startId) {
Log.i(TAG, "Received " + intent);
VpnService.Builder builder = new VpnService.Builder();
builder.setSession(getString(R.string.app_name));
// ... (additional configuration)
mInterface = builder.establish();
}
Orbot uses the Tor library to create a SOCKS proxy:
public void initTor() throws IOException {
torConfig = new TorConfig.Builder()
.updateTorConfigCustom(customTorrc)
.useBridges(useBridges)
.build();
torInstance = TorInstance.create(context, torConfig);
torInstance.start();
}
Both projects aim to enhance privacy and security on Android devices, but they take different approaches. NetGuard focuses on network-level filtering and blocking, while Orbot provides comprehensive Tor anonymity for all internet traffic.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
NetGuard
NetGuard provides simple and advanced ways to block access to the internet - no root required. Applications and addresses can individually be allowed or denied access to your Wi-Fi and/or mobile connection.
WARNING: there is an app in the Samsung Galaxy app store "Play Music - MP3 Music player" with the same package name as NetGuard, which will be installed as update without your confirmation. This app is probably malicious and was reported to Samsung on December 8, 2021.
Blocking access to the internet can help:
- reduce your data usage
- save your battery
- increase your privacy
NetGuard is the first free and open source no-root firewall for Android.
Features:
- Simple to use
- No root required
- 100% open source
- No calling home
- No tracking or analytics
- Actively developed and supported
- Android 5.1 and later supported
- IPv4/IPv6 TCP/UDP supported
- Tethering supported
- Optionally allow when screen on
- Optionally block when roaming
- Optionally block system applications
- Optionally forward ports, also to external addresses (not available if installed from the Play store)
- Optionally notify when an application accesses the internet
- Optionally record network usage per application per address
- Optionally block ads using a hosts file (not available if installed from the Play store)
- Material design theme with light and dark theme
PRO features:
- Log all outgoing traffic; search and filter access attempts; export PCAP files to analyze traffic
- Allow/block individual addresses per application
- New application notifications; configure NetGuard directly from the notification
- Display network speed graph in a status bar notification
- Select from five additional themes in both light and dark version
There is no other no-root firewall offering all these features.
Requirements:
- Android 5.1 or later
- A compatible device
Downloads:
Certificate fingerprints:
- MD5: B6:4A:E8:08:1C:3C:9C:19:D6:9E:29:00:46:89:DA:73
- SHA1: EF:46:F8:13:D2:C8:A0:64:D7:2C:93:6B:9B:96:D1:CC:CC:98:93:78
- SHA256: E4:A2:60:A2:DC:E7:B7:AF:23:EE:91:9C:48:9E:15:FD:01:02:B9:3F:9E:7C:9D:82:B0:9C:0B:39:50:00:E4:D4
Usage:
- Enable the firewall using the switch in the action bar
- Allow/deny Wi-Fi/mobile internet access using the icons along the right side of the application list
You can use the settings menu to change from blacklist mode (allow all in Settings but block unwanted applications in list) to whitelist mode (block all in Settings but allow favorite applications in list).
- Red/orange/yellow/amber = internet access denied
- Teal/blue/purple/grey = internet access allowed
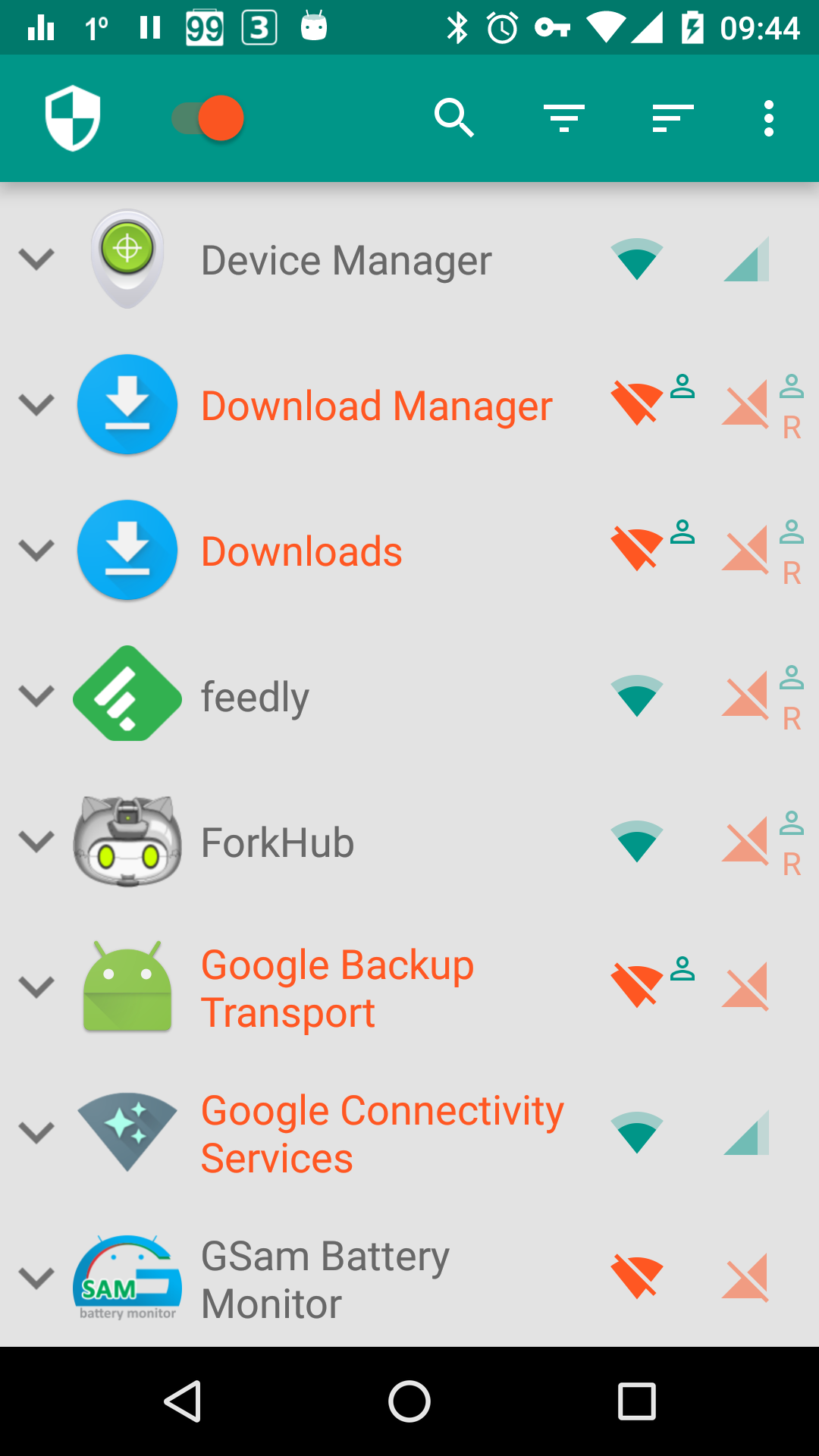
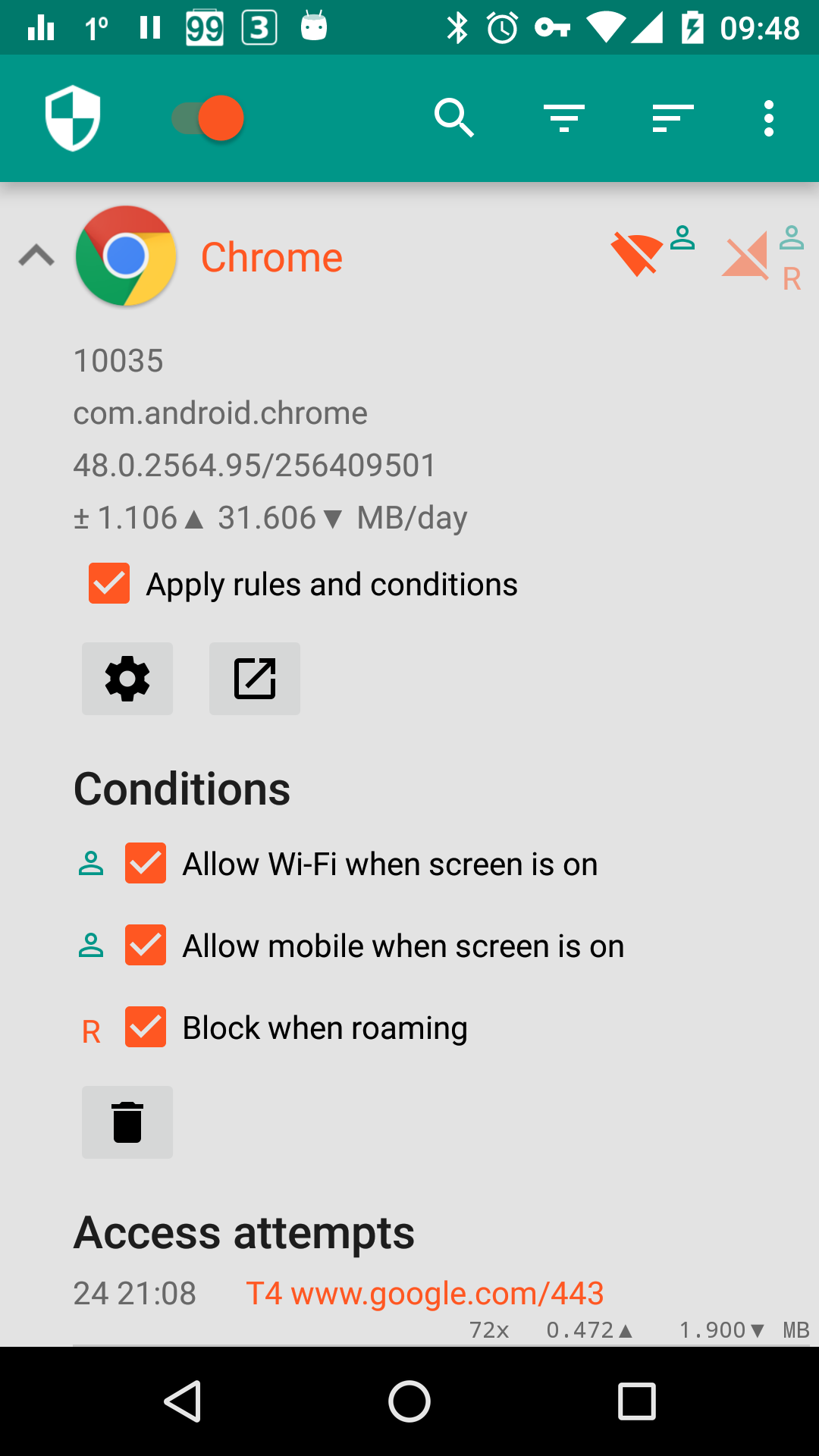
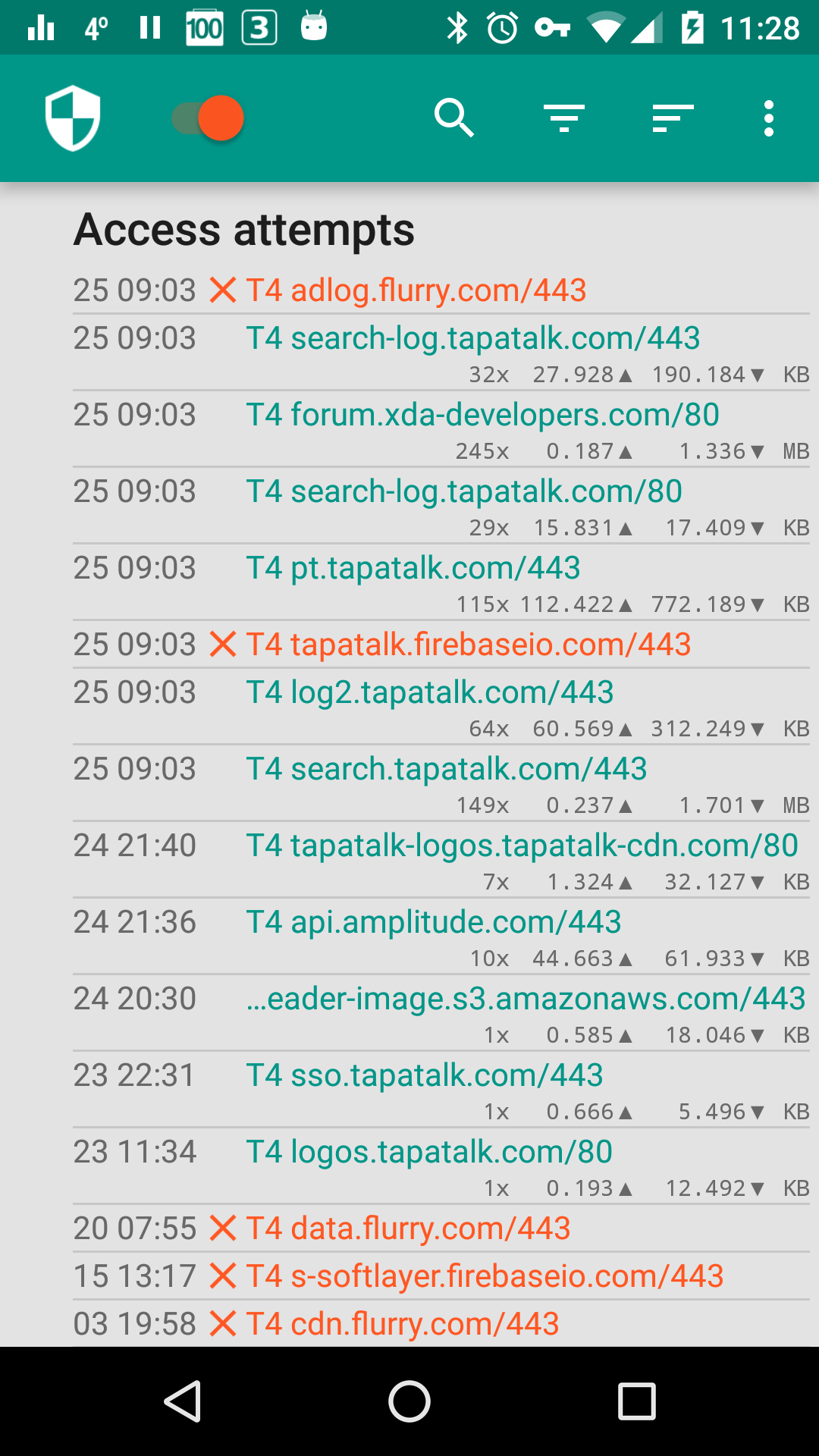
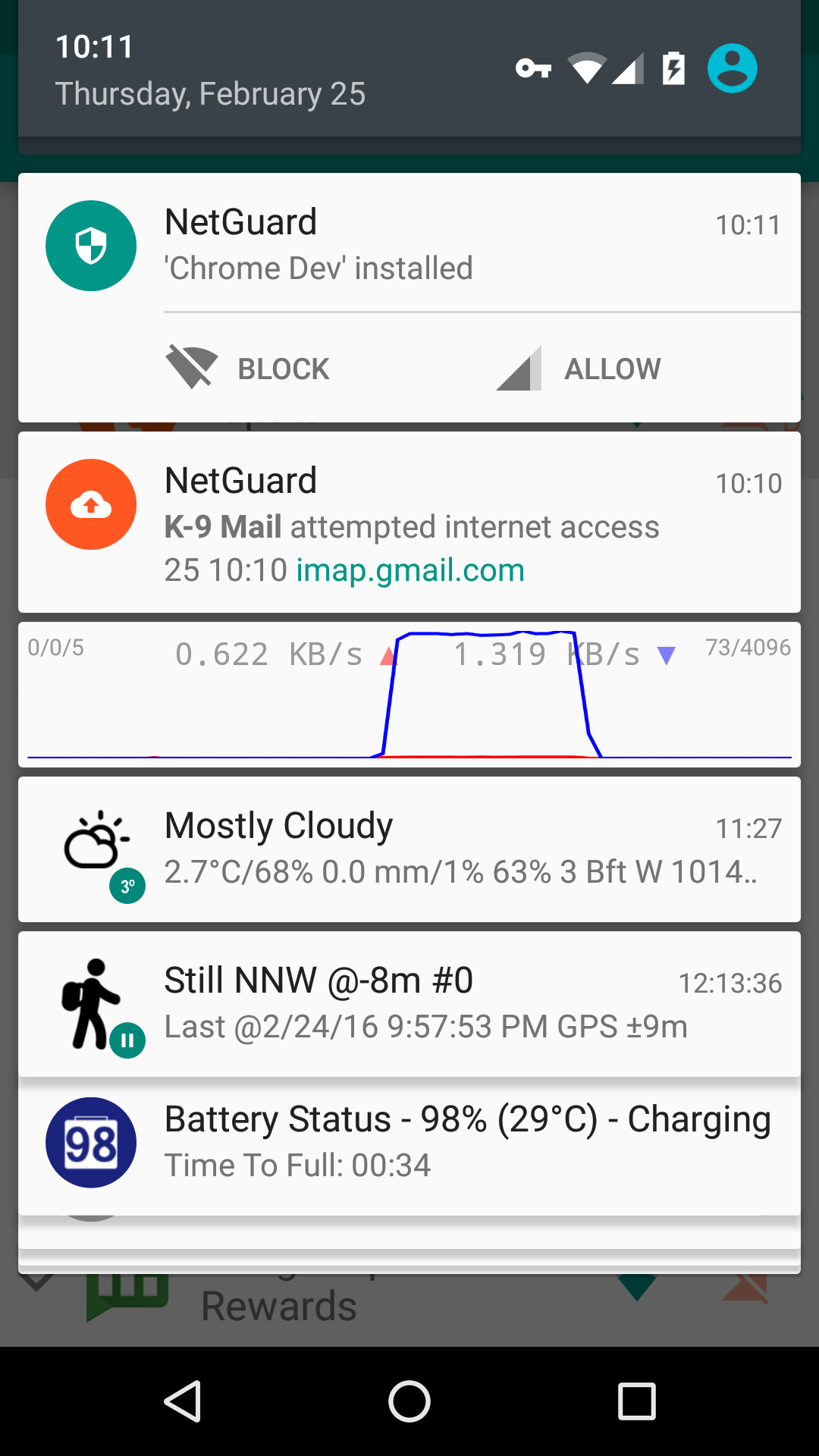
For more screenshots, see here.
Compatibility
The only way to build a no-root firewall on Android is to use the Android VPN service. Android doesn't allow chaining of VPN services, so you cannot use NetGuard together with other VPN based applications. See also this FAQ.
NetGuard can be used on rooted devices too and even offers more features than most root firewalls.
Some older Android versions, especially Samsung's Android versions, have a buggy VPN implementation, which results in Android refusing to start the VPN service in certain circumstances, like when there is no internet connectivity yet (when starting up your device) or when incorrectly requiring manual approval of the VPN service again (when starting up your device). NetGuard will try to workaround this and remove the error message when it succeeds, else you are out of luck.
Some LineageOS versions have a broken Android VPN implementation, causing all traffic to be blocked, please see this FAQ for more information.
On GrapheneOS, the Android Always-On VPN function and the sub option 'Block connections without VPN' are enabled by default. However, this sub option will result in blocking all traffic, please see this FAQ.
NetGuard is not supported for apps installed in a work profile, or in a Secure Folder (Samsung), or as second instance (MIUI), or as Parallel app (OnePlus), or as Xiaomi dual app because the Android VPN service too often does not work correctly in this situation, which can't be fixed by NetGuard.
NetGuard is not supported for internet connections via a wire, like ethernet or USB, because the Android VPN service often doesn't work properly in this situation.
Filtering mode cannot be used on CopperheadOS.
NetGuard will not work or crash when the package com.android.vpndialogs has been removed or otherwise is unavailable. Removing this package is possible with root permissions only. If you disable this package, you can enable it with this command again:
adb shell pm enable --user 0 com.android.vpndialogs
NetGuard is supported on phones and tablets with a true-color screen only, so not for other device types like on a television or in a car.
Android does not allow incoming connections (not the same as incoming traffic) and the Android VPN service has no support for this either. Therefore managing incoming connections for servers running on your device is not supported.
Wi-Fi or IP calling will not work if your provider uses IPsec to encrypt your phone calls, SMS messages and/or MMS messages, unless there was made an exception in NetGuard for your provider (currently for T-Mobile and Verizon). I am happy to add exceptions for other providers, but I need the MCC codes, MNC codes and IP address ranges your provider is using. As an alternative you can enable the option 'Disable on call', which is available since version 2.113.
Frequently Asked Questions (FAQ)
(1) Can NetGuard completely protect my privacy?
(2) Can I use another VPN application while using NetGuard?
(3) Can I use NetGuard on any Android version?
(4) Will NetGuard use extra battery power?
(6) Will NetGuard send my internet traffic to an external (VPN) server?
(7) Why are applications without internet permission shown?
(8) What do I need to enable for the Google Play⢠store app to work?
(9) Why is the VPN service being restarted?
(10) Will you provide a Tasker plug-in?
(13) How can I remove the ongoing NetGuard entry in the notification screen?
(14) Why can't I select OK to approve the VPN connection request?
(15) Are F-Droid builds supported?
(16) Why are some applications shown dimmed?
(17) Why is NetGuard using so much memory?
(18) Why can't I find NetGuard in the Google Play⢠store app?
(19) Why does application XYZ still have internet access?
(20) Can I Greenify/hibernate NetGuard?
(21) Does doze mode affect NetGuard?
(22) Can I tether (use the Android hotspot) / use Wi-Fi calling while using NetGuard?
(24) Can you remove the notification from the status bar?
(25) Can you add a 'select all'?
(27) How do I read the blocked traffic log?
(28) Why is Google connectivity services allowed internet access by default?
(29) Why do I get 'The item you requested is not available for purchase'?
(30) Can I also run AFWall+ on the same device?
(31) Why can some applications be configured as a group only?
(32) Why is the battery/network usage of NetGuard so high
(34) Can you add the condition 'when on foreground'?
(35) Why does the VPN not start?
(36) Can you add PIN or password protection?
(37) Why are the pro features so expensive?
(38) Why did NetGuard stop running?
(39) How does a VPN based firewall differ from a iptables based firewall?
(42) Why is permission ... needed?
(43) I get 'This app is causing your device to run slowly'
(44) I don't get notifications on access
(45) Does NetGuard handle incoming connections?
(47) Why are there in application advertisements?
(48) Why are some domain names blocked while they are set to be allowed?
(49) Does NetGuard encrypt my internet traffic / hide my IP address?
(50) Will NetGuard automatically start on boot?
(51) NetGuard blocks all internet traffic!
(53) The translation in my language is missing / incorrect / incomplete!
(54) How to tunnel all TCP connections through the Tor network?
(55) Why does NetGuard connect to Amazon / ipinfo.io?
(56) NetGuard allows all internet traffic!
(57) Why does NetGuard use so much data?
(58) Why does loading the application list take a long time?
(59) Can you help me restore my purchase?
(60) Why does IP (Wi-Fi) calling/SMS/MMS not work?
(62) How can I solve 'There was a problem parsing the package' ?
(63) Why is all DNS traffic allowed?
(64) Can you add DNS over TLS?
(65) Why can NetGuard not block itself?
Support
For questions, feature requests and bug reports, please use this form.
There is support on the latest version of NetGuard only.
There is no support on things that are not directly related to NetGuard.
There is no support on building and developing things by yourself.
NetGuard is supported for phones and tablets only, so not for other device types like on a television or in a car.
Contributing
Building
Building is simple, if you install the right tools:
The native code is built as part of the Android Studio project.
It is expected that you can solve build problems yourself, so there is no support on building. If you cannot build yourself, there are prebuilt versions of NetGuard available here.
Translating
- Translations to other languages are welcomed
- You can translate online here
- If your language is not listed, please send a message to marcel(plus)netguard(at)faircode(dot)eu
- You can see the status of all translations here.
Please note that by contributing you agree to the license below, including the copyright, without any additional terms or conditions.
Attribution
NetGuard uses:
License
GNU General Public License version 3
Copyright (c) 2015-2018 Marcel Bokhorst (M66B)
All rights reserved
This file is part of NetGuard.
NetGuard is free software: you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your discretion) any later version.
NetGuard is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with NetGuard. If not, see http://www.gnu.org/licenses/.
Trademarks
Android is a trademark of Google Inc. Google Play is a trademark of Google Inc
Top Related Projects
AFWall+ (Android Firewall +) - iptables based firewall for Android
Using system APIs directly with adb/root privileges from normal apps through a Java process started with app_process.
Gnirehtet provides reverse tethering for Android
The Github home of Orbot: Tor on Android (Also available on gitlab!)
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot