 Mobile-Security-Framework-MobSF
Mobile-Security-Framework-MobSF
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
Top Related Projects
The OWASP Mobile Application Security Testing Guide (MASTG) is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the OWASP Mobile Security Weakness Enumeration (MASWE) weaknesses, which are in alignment with the OWASP MASVS.
Tool to look for several security related Android application vulnerabilities
Runtime Mobile Security (RMS) 📱🔥 - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime
Quick Overview
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis. It supports both binary and source code scanning, making it a versatile tool for mobile app security testing.
Pros
- Comprehensive analysis: Covers static and dynamic analysis for Android, iOS, and Windows mobile applications
- Easy to use: Provides a user-friendly web interface for performing security assessments
- Extensive reporting: Generates detailed PDF and JSON reports with security findings
- Active development: Regularly updated with new features and security checks
Cons
- Resource-intensive: Can be demanding on system resources, especially for large applications
- Limited scalability: Not designed for high-volume or enterprise-level scanning
- Learning curve: Advanced features may require some technical expertise to fully utilize
- False positives: Like many automated tools, it may occasionally report false positives
Getting Started
To get started with MobSF:
- Install Docker on your system
- Run the following command to pull and start MobSF:
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
- Open your web browser and navigate to
http://localhost:8000 - Upload your mobile application (APK, IPA, or APPX file) for analysis
- Review the generated report for security findings and recommendations
For more detailed instructions and advanced usage, refer to the official documentation on the GitHub repository.
Competitor Comparisons
The OWASP Mobile Application Security Testing Guide (MASTG) is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the OWASP Mobile Security Weakness Enumeration (MASWE) weaknesses, which are in alignment with the OWASP MASVS.
Pros of MASTG
- Comprehensive guide covering mobile app security testing and reverse engineering
- Regularly updated with community contributions and industry best practices
- Provides detailed explanations and step-by-step instructions for various security testing techniques
Cons of MASTG
- Primarily a documentation project, lacking built-in automated tools
- Steeper learning curve for beginners due to its extensive content
- Requires manual implementation of described techniques
Code Comparison
While MASTG is primarily a documentation project, it does include code snippets for various security testing techniques. MobSF, on the other hand, is a complete automated testing framework. Here's a brief comparison:
MASTG (example of a code snippet for iOS jailbreak detection):
#include <sys/stat.h>
BOOL isJailbroken() {
struct stat statbuf;
return (stat("/Applications/Cydia.app", &statbuf) == 0);
}
MobSF (example of how to run a static analysis):
from mobsf.StaticAnalyzer.views.ios import static_analyzer as ios_sa
ios_sa.static_analyzer(file_path, file_type, rescan)
The MASTG provides code examples for manual implementation, while MobSF offers a ready-to-use framework for automated security testing.
Tool to look for several security related Android application vulnerabilities
Pros of QARK
- Focused specifically on Android app security analysis
- Provides detailed explanations of identified vulnerabilities
- Offers suggestions for fixing security issues
Cons of QARK
- Less actively maintained compared to MobSF
- Limited to Android platform only
- Fewer features and less comprehensive analysis than MobSF
Code Comparison
QARK example (Python):
def find_manifest(self):
manifest = None
for (dir_path, dir_names, file_names) in os.walk(self.apk_directory):
for file_name in file_names:
if file_name == 'AndroidManifest.xml':
manifest = os.path.join(dir_path, file_name)
return manifest
MobSF example (Python):
def get_manifest(app_dir, app_path, tools_dir, typ):
"""Get AndroidManifest.xml."""
try:
manifest = None
if typ == 'apk':
manifest = get_apk_manifest(app_path, app_dir, tools_dir)
elif typ == 'studio':
manifest = get_studio_manifest(app_dir)
return manifest
except Exception:
logger.exception('Getting Manifest file')
Both projects aim to analyze mobile app security, but QARK focuses solely on Android while MobSF supports multiple platforms. MobSF offers a more comprehensive set of features and is more actively maintained. QARK provides more detailed explanations of vulnerabilities and suggestions for fixes, which can be beneficial for developers. The code examples show similar approaches to finding the AndroidManifest.xml file, with MobSF's implementation being more modular and handling different app types.
Runtime Mobile Security (RMS) 📱🔥 - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime
Pros of RMS-Runtime-Mobile-Security
- Focuses on runtime analysis, allowing real-time inspection of app behavior
- Provides a web interface for easy interaction and monitoring
- Supports both Android and iOS platforms
Cons of RMS-Runtime-Mobile-Security
- Less comprehensive static analysis capabilities compared to MobSF
- Smaller community and fewer updates
- Limited documentation and support resources
Code Comparison
MobSF (Python):
def scan_file(self, file_path):
# Perform static analysis
results = self.static_analyzer.analyze(file_path)
# Generate report
return self.report_generator.create(results)
RMS-Runtime-Mobile-Security (JavaScript):
function hookMethod(className, methodName) {
Java.perform(() => {
const targetClass = Java.use(className);
targetClass[methodName].implementation = function() {
// Log method call and arguments
console.log(`${className}.${methodName} called`);
return this[methodName](...arguments);
};
});
}
The code snippets highlight the different approaches:
- MobSF focuses on static analysis and report generation
- RMS-Runtime-Mobile-Security emphasizes runtime method hooking and monitoring
Both tools serve different purposes in mobile app security testing, with MobSF offering a more comprehensive static analysis solution and RMS-Runtime-Mobile-Security providing real-time runtime analysis capabilities.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
Mobile Security Framework (MobSF)

Mobile Security Framework (MobSF) is a security research platform for mobile applications in Android, iOS and Windows Mobile. MobSF can be used for a variety of use cases such as mobile application security, penetration testing, malware analysis, and privacy analysis. The Static Analyzer supports popular mobile app binaries like APK, IPA, APPX and source code. Meanwhile, the Dynamic Analyzer supports both Android and iOS applications and offers a platform for interactive instrumented testing, runtime data and network traffic analysis. MobSF seamlessly integrates with your DevSecOps or CI/CD pipeline, facilitated by REST APIs and CLI tools, enhancing your security workflow with ease.
Made with  in India
in India
MobSF is also bundled with Android Tamer, BlackArch and Pentoo.
Support MobSF
Has MobSF made a difference for you? Show your support and help us innovate with a donation. It's easy to build open source, maintaining one is a different story.
Long live open source!
Documentation
Quick setup with docker
docker pull opensecurity/mobile-security-framework-mobsf:latest
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
# Default username and password: mobsf/mobsf
- Try MobSF Static Analyzer Online: mobsf.live
- MobSF in CI/CD: mobsfscan
- Conference Presentations: Slides & Videos
- MobSF Online Course: OpSecX MAS
- What's New: See Changelog
Collaborators
Ajin Abraham  | Magaofei
| Magaofei  | Matan Dobrushin
| Matan Dobrushin  | Vincent Nadal
| Vincent Nadal 
e-Learning Courses & Certifications
 Automated Mobile Application Security Assessment with MobSF -MAS
Automated Mobile Application Security Assessment with MobSF -MAS
 Android Security Tools Expert -ATX
Android Security Tools Expert -ATX
MobSF Support
- Free Support: Free limited support, questions, help and discussions, join our Slack channel
- Enterprise Support: Priority feature requests, live support & onsite training, see
Contribution, Feature Requests & Bugs
- Read CONTRIBUTING.md before opening bugs, feature requests and pull request.
- For Project updates and announcements, follow @ajinabraham or @OpenSecurity_IN.
- Github Issues are only for tracking bugs and feature requests. Do not post support or help queries there. We have a slack channel for that.
Static Analysis - Android

Static Analysis - iOS

Dynamic Analysis - Android APK

Web API Viewer
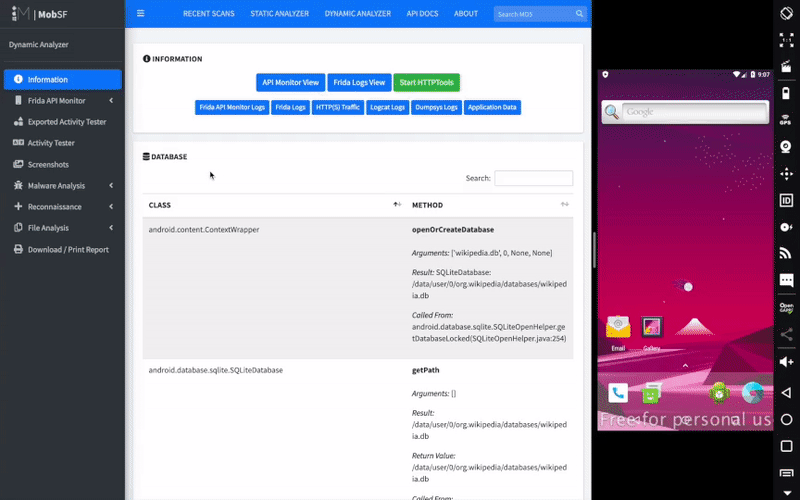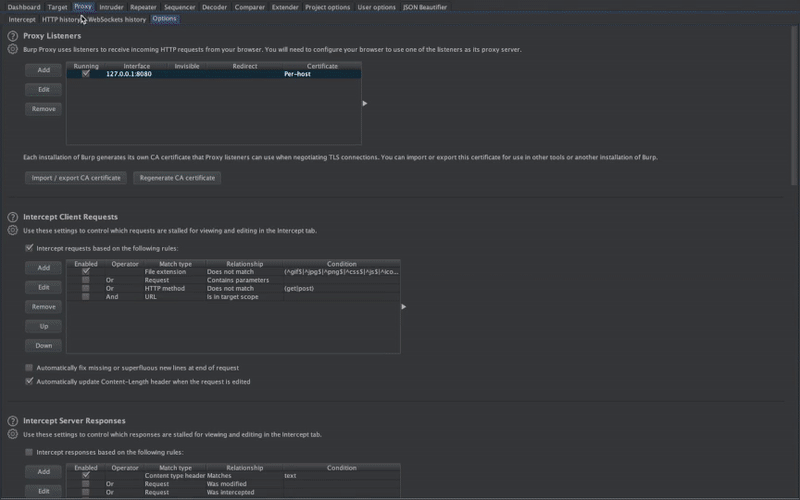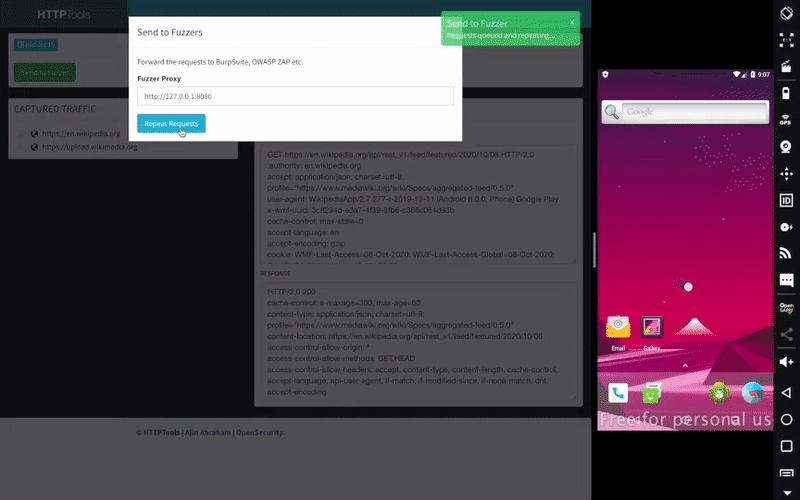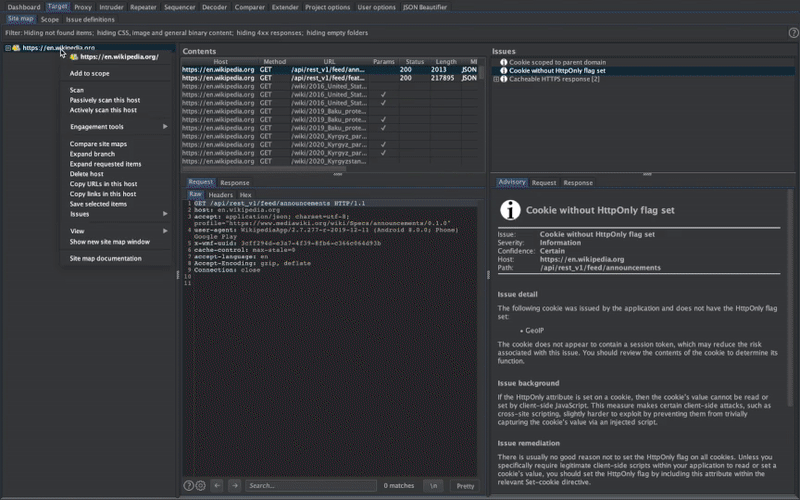
Dynamic Analysis - iOS IPA
Past Collaborators
Honorable Contributors & Shoutouts
- Amrutha VC - For the new MobSF logo
- Dominik Schlecht - For the awesome work on adding Windows Phone App Static Analysis to MobSF
- Esteban - Better Android Manifest Analysis and Static Analysis Improvement.
- Matan Dobrushin - For adding Android ARM Emulator support to MobSF - Special thanks goes for cuckoo-droid
- Shuxin - Android Binary Analysis
- Abhinav Saxena - (@xandfury) - For Travis CI and Logging integration
 Netguru (@karolpiateknet, @mtbrzeski) - For iOS Swift support, Rule contributions and SAST refactoring.
Netguru (@karolpiateknet, @mtbrzeski) - For iOS Swift support, Rule contributions and SAST refactoring.- Maxime Fawe - (@Arenash13) - For Matching Strategy implementation of SAST pattern matching algorithms.
- Abhinav Sejpal (@Abhinav_Sejpal) - For poking me with bugs, feature requests, and UI & UX suggestions
- Anant Srivastava (@anantshri) - For Activity Tester Idea
- Anto Joseph (@antojoseph) - For the help with SuperSU
- Bharadwaj Machiraju (@tunnelshade) - For writing pyWebProxy from scratch
- Rahul (@c0dist) - Kali Support
- MindMac - For writing Android Blue Pill
- Oscar Alfonso Diaz - (@OscarAkaElvis) - For Dockerfile contributions
- Thomas Abraham - For JS Hacks on UI
- Tim Brown (@timb_machine) - For the iOS Binary Analysis Ruleset
- Shanil Prasad (@Rajuraju14) - For improving iOS ATS Analysis
- Jovan Petrovic (@JovanPetrovic) - For sponsoring a server to host mobsf.live
Top Related Projects
The OWASP Mobile Application Security Testing Guide (MASTG) is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the OWASP Mobile Security Weakness Enumeration (MASWE) weaknesses, which are in alignment with the OWASP MASVS.
Tool to look for several security related Android application vulnerabilities
Runtime Mobile Security (RMS) 📱🔥 - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot













