 WiFi-Pumpkin-deprecated
WiFi-Pumpkin-deprecated
DEPRECATED, wifipumpkin3 -> https://github.com/P0cL4bs/wifipumpkin3
Top Related Projects
The Rogue Access Point Framework
Fluxion is a remake of linset by vk496 with enhanced functionality.
This is a multi-use bash script for Linux systems to audit wireless networks.
Targeted evil twin attacks against WPA2-Enterprise networks. Indirect wireless pivots using hostile portal attacks.
*DEPRECATED* mana toolkit for wifi rogue AP attacks and MitM
Quick Overview
WiFi-Pumpkin-deprecated is a powerful framework for auditing, attacking, and creating rogue access points. It's designed for security professionals and researchers to test wireless network security. This repository is the deprecated version of the tool, which has since been updated to a new version.
Pros
- Comprehensive suite of wireless attack tools in one framework
- User-friendly graphical interface for easier operation
- Supports various attack methods and plugins
- Useful for both offensive and defensive security testing
Cons
- This version is deprecated and may lack recent security updates
- Potential for misuse if not used responsibly
- Requires advanced knowledge of wireless security to use effectively
- May not work with the latest wireless protocols or hardware
Getting Started
To get started with WiFi-Pumpkin-deprecated:
-
Clone the repository:
git clone https://github.com/P0cL4bs/WiFi-Pumpkin-deprecated.git -
Install dependencies:
cd WiFi-Pumpkin-deprecated pip install -r requirements.txt -
Run the tool:
sudo python wifi-pumpkin.py
Note: This is a deprecated version. It's recommended to use the latest version of WiFi-Pumpkin for up-to-date features and security patches. Always ensure you have proper authorization before using this tool on any network.
Competitor Comparisons
The Rogue Access Point Framework
Pros of Wifiphisher
- More actively maintained with recent updates
- Supports a wider range of attack scenarios and phishing templates
- Better documentation and community support
Cons of Wifiphisher
- Less user-friendly interface compared to WiFi-Pumpkin's GUI
- Fewer built-in tools for post-exploitation and network analysis
Code Comparison
WiFi-Pumpkin (Python 2):
def Start(self):
self.interfaces = Refactor.get_interfaces()
self.APselected = self.interfaces['activated'][0]
self.SettingsAP = {
'interface': self.APselected,
'ssid': self.EditApName.text(),
'channel': int(self.EditChannel.text()),
}
Wifiphisher (Python 3):
def start(self):
self.network_manager = NetworkManager()
self.template_manager = TemplateManager()
self.access_point = AccessPoint(self.network_manager)
self.em = ExtensionManager(self.network_manager)
self.phishinghttp = PhishingHTTPServer(self.template_manager, self.em)
Both projects aim to create rogue access points for security testing, but Wifiphisher's code structure appears more modular and follows Python 3 conventions. WiFi-Pumpkin's code is older and uses Python 2, which is no longer supported.
Fluxion is a remake of linset by vk496 with enhanced functionality.
Pros of Fluxion
- More actively maintained with recent updates
- Supports a wider range of attack vectors and techniques
- Better documentation and community support
Cons of Fluxion
- Steeper learning curve for beginners
- Requires more dependencies and setup
- May trigger more antivirus alerts due to its extensive feature set
Code Comparison
WiFi-Pumpkin-deprecated:
def start(self):
self.interfaces = Linux.get_interfaces()
self.loader = ThreadPumpkin(self.interfaces)
self.loader.start()
Fluxion:
function fluxion_header() {
clear
echo -e "${yellow}[${red}$version${yellow}] ${green}FLUXION ${yellow}$revision ${red}$OS"
echo
}
While both projects aim to test WiFi security, Fluxion appears to be more actively developed and feature-rich. WiFi-Pumpkin-deprecated uses Python for its core functionality, while Fluxion relies heavily on bash scripting. Fluxion offers a more comprehensive set of attack vectors but may be more complex for newcomers. WiFi-Pumpkin-deprecated, despite being deprecated, might still be useful for simpler testing scenarios or as a learning tool for those new to WiFi security testing.
This is a multi-use bash script for Linux systems to audit wireless networks.
Pros of airgeddon
- More actively maintained with frequent updates
- Supports a wider range of wireless attacks and tools
- Better documentation and community support
Cons of airgeddon
- Steeper learning curve for beginners
- Requires more manual configuration and setup
- Less user-friendly interface compared to WiFi-Pumpkin
Code Comparison
WiFi-Pumpkin (Python):
def getAccessPoints(self):
aps = []
for ap in self.sniffs:
if ap not in aps:
aps.append(ap)
return aps
airgeddon (Bash):
get_recon_data() {
readarray -t AIRODUMP_CSV_FILES < <(find "${tmpdir}" -name "${airgeddon_csv_file}*" 2> /dev/null)
[[ -z "${AIRODUMP_CSV_FILES[0]}" ]] && return 1
awk -F ',' '{print $14}' "${AIRODUMP_CSV_FILES[@]}" 2> /dev/null | sed '/^$/d' | sort -u
}
The code snippets show different approaches to gathering access point data. WiFi-Pumpkin uses Python to manage a list of unique access points, while airgeddon employs Bash scripting to process CSV files generated by airodump-ng.
Both tools are powerful for wireless network auditing, but airgeddon offers more features and flexibility at the cost of complexity, while WiFi-Pumpkin provides a more user-friendly experience for those new to wireless security testing.
Targeted evil twin attacks against WPA2-Enterprise networks. Indirect wireless pivots using hostile portal attacks.
Pros of eaphammer
- More focused on EAP-based attacks and Evil Twin attacks
- Actively maintained with recent updates
- Supports hostapd-wpe for advanced wireless attacks
Cons of eaphammer
- Less user-friendly interface compared to WiFi-Pumpkin's GUI
- Narrower scope of features, primarily focused on EAP attacks
- Requires more manual configuration and command-line usage
Code Comparison
eaphammer:
def hostile_portal():
configure_hostapd()
start_hostapd()
configure_dhcp()
start_dhcp()
configure_dns()
start_dns()
WiFi-Pumpkin:
class PumpkinProxy(ProxyMode):
def __init__(self, parent=None, **kwargs):
super(PumpkinProxy, self).__init__(parent)
self.setObjectName("Pumpkin-Proxy")
self.setModuleName("Pumpkin-Proxy")
Summary
eaphammer is a more specialized tool focusing on EAP-based attacks and Evil Twin scenarios, with active maintenance and support for advanced wireless attack techniques. It requires more technical expertise to use effectively.
WiFi-Pumpkin offers a broader range of features with a user-friendly GUI, making it more accessible for beginners. However, it's no longer actively maintained, which may limit its effectiveness against newer security measures.
The code comparison shows eaphammer's focus on configuring and starting specific services for attacks, while WiFi-Pumpkin's code demonstrates its modular structure for different proxy modes within its GUI framework.
*DEPRECATED* mana toolkit for wifi rogue AP attacks and MitM
Pros of mana
- More actively maintained with recent updates
- Broader range of attack vectors and tools included
- Better documentation and setup instructions
Cons of mana
- Steeper learning curve for beginners
- Requires more system resources to run effectively
- Less user-friendly interface compared to WiFi-Pumpkin
Code Comparison
mana:
#!/bin/bash
source config.rc
start_noupstream
start_noupstream_pineapple
start_nat_full
start_nat_simple
WiFi-Pumpkin:
def Start(self):
self.interfaces = Refactor.get_interfaces()
self.ConfigTwin['AP_iface'] = str(self.selectCard.currentText())
self.ConfigTwin['PortRedirect'] = str(self.redirectport.text())
The code snippets show different approaches:
- mana uses bash scripts for configuration and startup
- WiFi-Pumpkin employs Python for its interface and functionality
Both tools serve similar purposes but cater to different user preferences and skill levels. mana offers more advanced features and flexibility, while WiFi-Pumpkin provides a more accessible interface for less experienced users.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
This repository is âï¸ DEPRECATED, wifipumpkin3 is Released, checkout!

WiFi-Pumpkin - Framework for Rogue Wi-Fi Access Point Attack
Description
The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target. It comes stuffed with features, including rogue Wi-Fi access points, deauth attacks on client APs, a probe request and credentials monitor, transparent proxy, Windows update attack, phishing manager, ARP Poisoning, DNS Spoofing, Pumpkin-Proxy, and image capture on the fly. moreover, the WiFi-Pumpkin is a very complete framework for auditing Wi-Fi security check the list of features is quite broad.
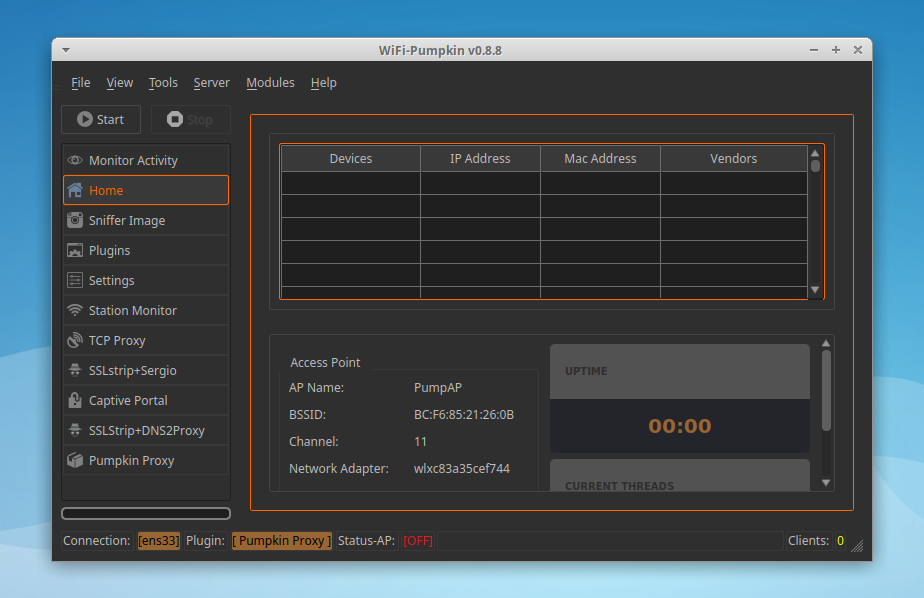
Installation
- Python 2.7
git clone https://github.com/P0cL4bs/WiFi-Pumpkin.git
cd WiFi-Pumpkin
./installer.sh --install
or download .deb file to install
sudo dpkg -i wifi-pumpkin-0.8.8-all.deb
sudo apt-get -f install # force install dependencies if not install normally
refer to the wiki for Installation
Features
- Rogue Wi-Fi Access Point
- Deauth Attack Clients AP
- Probe Request Monitor
- DHCP Starvation Attack
- Credentials Monitor
- Transparent Proxy
- Windows Update Attack
- Phishing Manager
- Partial Bypass HSTS protocol
- Support beef hook
- ARP Poison
- DNS Spoof
- Patch Binaries via MITM (BDF-Proxy)
- LLMNR, NBT-NS and MDNS poisoner (Responder)
- Pumpkin-Proxy (ProxyServer (mitmproxy API))
- Capture images on the fly
- TCP-Proxy (with scapy)
- Moduled plugins and proxys
- Wireless Mode support hostapd-mana/hostapd-karma attacks
- Capitve-portals [new]
Donation
paypal:
Via BTC:
1HBXz6XX3LcHqUnaca5HRqq6rPUmA3pf6f
Plugins
| Plugin | Description |
|---|---|
| Dns2proxy | This tools offer a different features for post-explotation once you change the DNS server to a Victim. |
| Sstrip2 | Sslstrip is a MITM tool that implements Moxie Marlinspike's SSL stripping attacks based version fork @LeonardoNve/@xtr4nge. |
| Sergio_proxy | Sergio Proxy (a Super Effective Recorder of Gathered Inputs and Outputs) is an HTTP proxy that was written in Python for the Twisted framework. |
| BDFProxy | Patch Binaries via MITM: BackdoorFactory + mitmProxy, bdfproxy-ng is a fork and review of the original BDFProxy @secretsquirrel. |
| Responder | Responder an LLMNR, NBT-NS and MDNS poisoner. Author: Laurent Gaffie |
| PumpkinProxy | Intercepting HTTP data, this proxy server that allows to intercept requests and response on the fly |
| CaptivePortals | Captive-Portal allow the Attacker block Internet access for users until they open the page login page where a password is required before being allowed to browse the web. |
Transparent Proxy
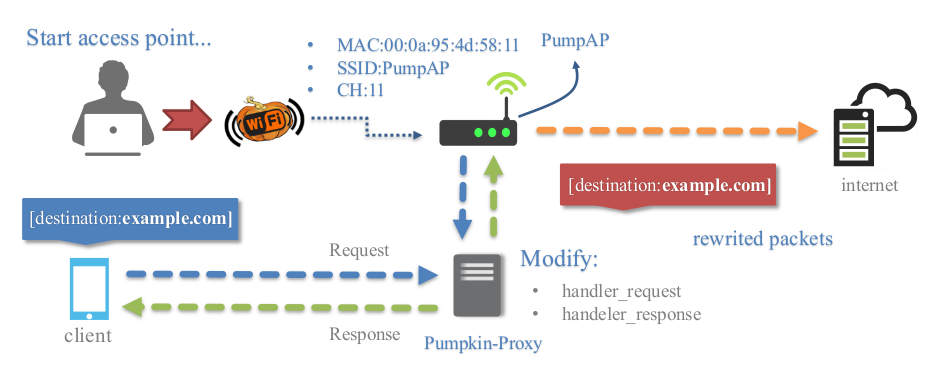
Transparent proxies(mitmproxy) that you can use to intercept and manipulate HTTP traffic modifying requests and responses, that allow to inject javascripts into the targets visited. You can easily implement a module to inject data into pages creating a python file in directory "plugins/extension/" automatically will be listed on Pumpkin-Proxy tab.
Plugins Example Dev
from mitmproxy.models import decoded # for decode content html
from plugins.extension.plugin import PluginTemplate
class Nameplugin(PluginTemplate):
meta = {
'Name' : 'Nameplugin',
'Version' : '1.0',
'Description' : 'Brief description of the new plugin',
'Author' : 'by dev'
}
def __init__(self):
for key,value in self.meta.items():
self.__dict__[key] = value
# if you want set arguments check refer wiki more info.
self.ConfigParser = False # No require arguments
def request(self, flow):
print flow.__dict__
print flow.request.__dict__
print flow.request.headers.__dict__ # request headers
host = flow.request.pretty_host # get domain on the fly requests
versionH = flow.request.http_version # get http version
# get redirect domains example
# pretty_host takes the "Host" header of the request into account,
if flow.request.pretty_host == "example.org":
flow.request.host = "mitmproxy.org"
# get all request Header example
self.send_output.emit("\n[{}][HTTP REQUEST HEADERS]".format(self.Name))
for name, valur in flow.request.headers.iteritems():
self.send_output.emit('{}: {}'.format(name,valur))
print flow.request.method # show method request
# the model printer data
self.send_output.emit('[NamePlugin]:: this is model for save data logging')
def response(self, flow):
print flow.__dict__
print flow.response.__dict__
print flow.response.headers.__dict__ #convert headers for python dict
print flow.response.headers['Content-Type'] # get content type
#every HTTP response before it is returned to the client
with decoded(flow.response):
print flow.response.content # content html
flow.response.content.replace('</body>','<h1>injected</h1></body>') # replace content tag
del flow.response.headers["X-XSS-Protection"] # remove protection Header
flow.response.headers["newheader"] = "foo" # adds a new header
#and the new header will be added to all responses passing through the proxy
About plugins
plugins on the wiki
TCP-Proxy Server
A proxy that you can place between in a TCP stream. It filters the request and response streams with (scapy module) and actively modify packets of a TCP protocol that gets intercepted by WiFi-Pumpkin. this plugin uses modules to view or modify the intercepted data that possibly easiest implementation of a module, just add your custom module on "plugins/analyzers/" automatically will be listed on TCP-Proxy tab.
from scapy.all import *
from scapy_http import http # for layer HTTP
from default import PSniffer # base plugin class
class ExamplePlugin(PSniffer):
_activated = False
_instance = None
meta = {
'Name' : 'Example',
'Version' : '1.0',
'Description' : 'Brief description of the new plugin',
'Author' : 'your name',
}
def __init__(self):
for key,value in self.meta.items():
self.__dict__[key] = value
@staticmethod
def getInstance():
if ExamplePlugin._instance is None:
ExamplePlugin._instance = ExamplePlugin()
return ExamplePlugin._instance
def filterPackets(self,pkt): # (pkt) object in order to modify the data on the fly
if pkt.haslayer(http.HTTPRequest): # filter only http request
http_layer = pkt.getlayer(http.HTTPRequest) # get http fields as dict type
ip_layer = pkt.getlayer(IP)# get ip headers fields as dict type
print http_layer.fields['Method'] # show method http request
# show all item in Header request http
for item in http_layer.fields['Headers']:
print('{} : {}'.format(item,http_layer.fields['Headers'][item]))
print ip_layer.fields['src'] # show source ip address
print ip_layer.fields['dst'] # show destiny ip address
print http_layer # show item type dict
print ip_layer # show item type dict
return self.output.emit({'name_module':'send output to tab TCP-Proxy'})
About TCP-Proxy
TCP-Proxy on the wiki
About Captive Portals
the plugin Captive-Portal allow the Attacker mount a wireless access point which is used in conjuction with a web server and iptables traffic capturing rules to create the phishing portal. Users can freely connect to these networks without a password and will often be directed to a login page where a password is required before being allowed to browse the web.
Captive-portals on the wiki
Screenshots
Screenshot on the wiki
FAQ
FAQ on the wiki
Contact Us
Whether you want to report a bug, send a patch or give some suggestions on this project, drop us or open pull requests
community
Top Related Projects
The Rogue Access Point Framework
Fluxion is a remake of linset by vk496 with enhanced functionality.
This is a multi-use bash script for Linux systems to audit wireless networks.
Targeted evil twin attacks against WPA2-Enterprise networks. Indirect wireless pivots using hostile portal attacks.
*DEPRECATED* mana toolkit for wifi rogue AP attacks and MitM
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot
