Top Related Projects
The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics.
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
articles
A collection of awesome penetration testing resources, tools and other shiny things
This repository contains cutting-edge open-source security tools (OST) for a red teamer and threat hunter.
A collection of hacking / penetration testing resources to make you better!
Quick Overview
The coreb1t/awesome-pentest-cheat-sheets repository is a curated collection of penetration testing and security-related cheat sheets. It serves as a comprehensive resource for cybersecurity professionals, ethical hackers, and enthusiasts, providing quick reference guides on various tools, techniques, and methodologies used in penetration testing and security assessments.
Pros
- Extensive collection of cheat sheets covering a wide range of security topics
- Regularly updated with new content and contributions from the community
- Well-organized and categorized for easy navigation and quick reference
- Free and open-source, accessible to anyone interested in cybersecurity
Cons
- Some cheat sheets may become outdated if not regularly maintained
- Quality and depth of information may vary between different cheat sheets
- Lack of standardized format across all cheat sheets
- May overwhelm beginners due to the vast amount of information
As this is not a code library, we'll skip the code examples and getting started instructions sections.
Competitor Comparisons
The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics.
Pros of CheatSheetSeries
- Comprehensive coverage of web application security topics
- Regularly updated and maintained by OWASP, a trusted authority in security
- Well-structured with consistent formatting across cheat sheets
Cons of CheatSheetSeries
- Focused primarily on web application security, less coverage of general pentesting topics
- More text-heavy, with fewer quick-reference style lists or tables
Code Comparison
CheatSheetSeries (XML Security):
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<foo>&xxe;</foo>
awesome-pentest-cheat-sheets (SQL Injection):
' OR '1'='1
' UNION SELECT null, username, password FROM users--
While both repositories provide valuable security information, CheatSheetSeries offers more in-depth explanations and best practices for web application security. awesome-pentest-cheat-sheets, on the other hand, provides a broader range of pentesting topics with more concise, quick-reference style content. The code examples reflect this difference, with CheatSheetSeries focusing on specific vulnerabilities and awesome-pentest-cheat-sheets offering more general attack techniques.
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
Pros of PayloadsAllTheThings
- More comprehensive coverage of various attack vectors and techniques
- Regularly updated with new payloads and methodologies
- Includes practical examples and code snippets for each technique
Cons of PayloadsAllTheThings
- Less organized structure compared to awesome-pentest-cheat-sheets
- May be overwhelming for beginners due to the sheer amount of information
- Lacks a curated list of external resources and tools
Code Comparison
PayloadsAllTheThings (SQL Injection):
' OR '1'='1
' UNION SELECT NULL, NULL, NULL--
UNION ALL SELECT NULL, NULL, NULL, NULL, NULL, NULL, NULL, CONCAT(0x7176767a71,IFNULL(CAST(CURRENT_USER() AS CHAR),0x20),0x7176767a71)#
awesome-pentest-cheat-sheets (SQL Injection):
' OR 1=1--
UNION SELECT username, password FROM users
PayloadsAllTheThings provides more diverse and complex payload examples, while awesome-pentest-cheat-sheets offers simpler, more straightforward examples. The former is better suited for advanced users, while the latter is more accessible for beginners.
Both repositories serve as valuable resources for penetration testers and security professionals, with PayloadsAllTheThings offering a wider range of techniques and awesome-pentest-cheat-sheets providing a more curated and organized approach to pentesting information.
articles
Pros of PENTESTING-BIBLE
- More comprehensive coverage of pentesting topics, including detailed guides and tutorials
- Regularly updated with new content and resources
- Includes a wider range of tools and techniques for various pentesting scenarios
Cons of PENTESTING-BIBLE
- Less organized structure compared to awesome-pentest-cheat-sheets
- May be overwhelming for beginners due to the sheer volume of information
- Some links may be outdated or broken due to the large number of resources
Code Comparison
While both repositories primarily focus on curating resources rather than providing code, PENTESTING-BIBLE does include some code snippets and examples. Here's a brief comparison:
PENTESTING-BIBLE:
nmap -sV -sC -O -p- -T4 -oN nmap_full_tcp_scan 192.168.1.100
awesome-pentest-cheat-sheets:
No direct code examples provided in the main README.
The PENTESTING-BIBLE repository includes more practical examples and commands, while awesome-pentest-cheat-sheets focuses on linking to external cheat sheets and resources.
Both repositories serve as valuable resources for penetration testers and security professionals, with PENTESTING-BIBLE offering a more extensive collection of tools and techniques, while awesome-pentest-cheat-sheets provides a more concise and organized list of cheat sheets for quick reference.
A collection of awesome penetration testing resources, tools and other shiny things
Pros of awesome-pentest
- More comprehensive coverage of penetration testing tools and resources
- Better organization with clear categories and subcategories
- Regularly updated with new tools and resources
Cons of awesome-pentest
- May be overwhelming for beginners due to the extensive list of tools
- Less focus on specific cheat sheets and quick reference guides
Code comparison
While both repositories primarily consist of curated lists rather than code, here's a comparison of their README structures:
awesome-pentest:
# Awesome Penetration Testing
- [Online Resources](#online-resources)
- [Penetration Testing Resources](#penetration-testing-resources)
- [Exploit Development](#exploit-development)
- [Social Engineering Resources](#social-engineering-resources)
awesome-pentest-cheat-sheets:
# Awesome Pentest Cheat Sheets
## Table of Contents
- [Discovery & Scanning](#discovery--scanning)
- [Exploitation](#exploitation)
- [Privilege Escalation](#privilege-escalation)
The awesome-pentest repository has a more detailed and extensive structure, while awesome-pentest-cheat-sheets focuses specifically on cheat sheets and quick reference guides.
This repository contains cutting-edge open-source security tools (OST) for a red teamer and threat hunter.
Pros of Red-Teaming-Toolkit
- More comprehensive coverage of red teaming tools and techniques
- Includes sections on cloud security and social engineering
- Regularly updated with new tools and resources
Cons of Red-Teaming-Toolkit
- Less focus on specific cheat sheets and quick reference guides
- May be overwhelming for beginners due to the extensive list of tools
- Lacks detailed explanations for each tool or technique
Code Comparison
While both repositories primarily consist of curated lists rather than code, here's a comparison of their README structures:
Red-Teaming-Toolkit:
# Red-Teaming-Toolkit
A collection of open source and commercial tools that aid in red team operations.
## Contents
- [Reconnaissance](#reconnaissance)
- [Initial Access](#initial-access)
- [Post Exploitation](#post-exploitation)
awesome-pentest-cheat-sheets:
# Awesome Pentest Cheat Sheets
A collection of awesome penetration testing cheat sheets.
## Table of Contents
- [SQL Injection](#sql-injection)
- [XSS](#xss)
- [Linux Commands](#linux-commands)
Both repositories use a similar structure for organizing their content, but Red-Teaming-Toolkit focuses on categorizing tools by attack phases, while awesome-pentest-cheat-sheets organizes content by specific techniques or topics.
A collection of hacking / penetration testing resources to make you better!
Pros of Awesome-Hacking-Resources
- More comprehensive coverage of hacking topics, including reverse engineering, malware analysis, and CTF resources
- Better organization with clear categories and subcategories
- Includes links to online courses and learning platforms
Cons of Awesome-Hacking-Resources
- Less focused on specific pentesting tools and techniques
- May be overwhelming for beginners due to the sheer volume of resources
- Lacks direct cheat sheets for quick reference during pentesting engagements
Code Comparison
While both repositories primarily consist of curated lists rather than code, here's a comparison of their README structures:
Awesome-Pentest-Cheat-Sheets:
# Awesome Pentest Cheat Sheets
- [Penetration Testing/Security Cheatsheets](#penetration-testingsecurity-cheatsheets)
- [SQL Injection Cheatsheets](#sql-injection-cheatsheets)
- [Reverse Shell Cheatsheets](#reverse-shell-cheatsheets)
Awesome-Hacking-Resources:
# Awesome Hacking Resources
## Table of Contents
* [Learning the Skills](#learning-the-skills)
* [Tools](#tools)
* [Vulnerable Environments](#vulnerable-environments)
* [Courses](#courses)
Both repositories use markdown for organization, but Awesome-Hacking-Resources has a more detailed table of contents and better overall structure.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
THIS REPOSITORY IS DEPRECATED.
ALL OF ITS CONTENT HAS BEEN UPDATED AND MOVED TO awesome-pentest-cheat-sheets
Awesome Pentest Cheat Sheets 
Collection of cheat sheets useful for pentesting
Contribution
Your contributions and suggestions are heartily welcome. Please check the Contributing Guidelines for more details.
Security Talks and Videos
General
- Docker Cheat Sheet
- Mobile App Pentest Cheat Sheet
- OSX Command Line Cheat Sheet
- PowerShell Cheat Sheet - SANS PowerShell Cheat Sheet from SEC560 Course (PDF version)
- Rawsec's CyberSecurity Inventory - An open-source inventory of tools, resources, CTF platforms and Operating Systems about CyberSecurity. (Source)
- Regexp Security Cheat Sheet
- Security Cheat Sheets - A collection of security cheat sheets
- Unix / Linux Cheat Sheet
Discovery
- Google Dorks - Google Dorks Hacking Database (Exploit-DB)
- Shodan - Shodan is a search engine for finding specific devices, and device types, that exist online
- ZoomEye - Zoomeye is a Cyberspace Search Engine recording information of devices, websites, services and components etc.
- Amass - OWASP Network mapping of attack surfaces and external asset discovery using open source information
Enumeration
- enum4linux-ng - Python tool for enumerating information from Windows/Samba systems
Exploitation
- Empire Cheat Sheet - Empire is a PowerShell and Python post-exploitation framework
- Exploit Development Cheat Sheet - @ovid's exploit development in one picture
- Java Deserialization Cheat Sheet - A cheat sheet for pentesters about Java Native Binary Deserialization vulnerabilities
- Local File Inclusion (LFI) Cheat Sheet #1 - Arr0way's LFI Cheat Sheet
- Local File Inclusion (LFI) Cheat Sheet #2 - Aptive's LFI Cheat Sheet
- Metasploit Unleashed - The ultimate guide to the Metasploit Framework
- Metasploit Cheat Sheet - A quick reference guide (PNG version)(PDF version)
- PowerSploit Cheat Sheet - PowerSploit is a powershell post-exploitation framework
- PowerView 2.0 Tricks
- PowerView 3.0 Tricks
- PHP htaccess Injection Cheat Sheet - htaccess Injection Cheat Sheet by PHP Secure Configuration Checker
- Reverse Shell Cheat Sheet #1 - Pentestmonkey Reverse Shell Cheat Sheet
- Reverse Shell Cheat Sheet #2 - Arr0way's Reverse Shell Cheat Sheet
- SQL Injection Cheat Sheet - Netsparker's SQL Injection Cheat Sheet
- SQLite3 Injection Cheat Sheet
Privilege Escalation
Learn Privilege Escalation
- Windows / Linux Local Privilege Escalation Workshop - The Privilege Escalation Workshop covers all known (at the time) attack vectors of local user privilege escalation on both Linux and Windows operating systems and includes slides, videos, test VMs.
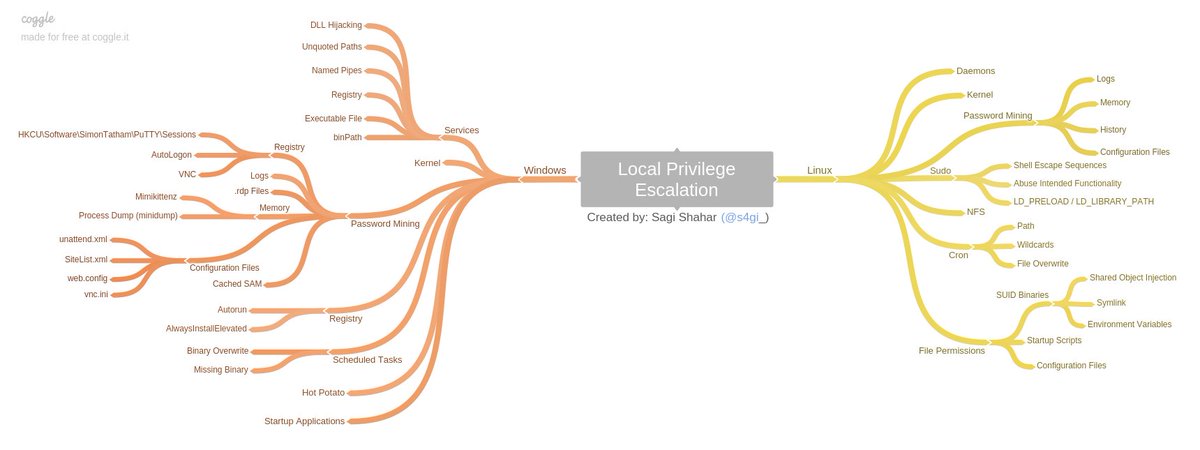
Linux Privilege Escalation
- Basic Linux Privilege Escalation - Linux Privilege Escalation by @g0tmi1k
- linux-exploit-suggester.sh - Linux privilege escalation auditing tool written in bash (updated)
- Linux_Exploit_Suggester.pl - Linux Exploit Suggester written in Perl (last update 3 years ago)
- Linux_Exploit_Suggester.pl v2 - Next-generation exploit suggester based on Linux_Exploit_Suggester (updated)
- Linux Soft Exploit Suggester - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities
- checksec.sh - bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source)
- linuxprivchecker.py - This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits (@SecuritySift)
- LinEnum - This tool is great at running through a heap of things you should check on a Linux system in the post exploit process. This include file permissions, cron jobs if visible, weak credentials etc.(@Rebootuser)
- linPEAS - LinPEAS - Linux Privilege Escalation Awesome Script. Check the Local Linux Privilege Escalation checklist from book.hacktricks.xyz
- MimiPenguin - A tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz.
Windows Privilege Escalation
- PowerUp - Excellent powershell script for checking of common Windows privilege escalation vectors. Written by harmj0y (direct link)
- PowerUp Cheat Sheet
- Windows Exploit Suggester - Tool for detection of missing security patches on the windows operating system and mapping with the public available exploits
- Sherlock - PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities
- Watson - Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
- Precompiled Windows Exploits - Collection of precompiled Windows exploits
- Metasploit Modules
- post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
- post/windows/gather/enum_patches - helps to identify any missing patches
Tools
- Nmap Cheat Sheet
- SQLmap Cheat Sheet
- SQLmap Tamper Scripts - SQLmap Tamper Scripts General/MSSQL/MySQL
- VIM Cheatsheet
- Wireshark Display Filters - Filters for the best sniffing tool
Tools Online
- XSS'OR Encoder/Decoder - Online Decoder/Encoder for testing purposes (@evilcos)
- WebGun - WebGun, XSS Payload Creator (@brutelogic)
- Hackvertor - Tool to convert various encodings and generate attack vectors (@garethheyes)
- JSFiddle - Test and share XSS payloads, Example PoC
Payloads
Genaral
- Fuzzdb - Dictionary of attack patterns and primitives for black-box application testing Polyglot Challenge with submitted solutions
- SecList - A collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more
XSS
- XSS Polyglot Payloads #1 - Unleashing an Ultimate XSS Polyglot list by 0xsobky
- XSS Polyglot Payloads #2 - @filedescriptor's XSS
- Browser's-XSS-Filter-Bypass-Cheat-Sheet- Excellent List of working XSS bypasses running on the latest version of Chrome / Safari, IE 11 / Edge created by Masato Kinugawa
Write-Ups
- Bug Bounty Reference - huge list of bug bounty write-up that is categorized by the bug type (SQLi, XSS, IDOR, etc.)
- Write-Ups for CTF challenges
- Facebook Bug Bounties - Categorized Facebook Bug Bounties write-ups
Learning Platforms
Online
- Hack The Box :: Penetration Testing Labs
- OWASP Vulnerable Web Applications Directory Project (Online) - List of online available vulnerable applications for learning purposes
- Pentestit labs - Hands-on Pentesting Labs (OSCP style)
- Root-me.org - Hundreds of challenges are available to train yourself in different and not simulated environments
- Vulnhub.com - Vulnerable By Design VMs for practical 'hands-on' experience in digital security
Off-Line
- Damn Vulnerable Xebia Training Environment - Docker Container including several vurnerable web applications (DVWA,DVWServices, DVWSockets, WebGoat, Juiceshop, Railsgoat, django.NV, Buggy Bank, Mutilidae II and more)
- OWASP Vulnerable Web Applications Directory Project (Offline) - List of offline available vulnerable applications for learning purposes
- Vulnerable SOAP Web Service - a vulnerable SOAP web service lab environment
- Vulnerable Flask Web App - vulnerable Flask Web App lab environment
Wireless Hacking
Tools
- wifite2 - Full automated WiFi security testing script
Defence Topics
- Docker Security Cheat Sheet - The following tips should help you to secure a container based system (PDF version)
- Windows Domain Hardening - A curated list of awesome Security Hardening techniques for Windows
Programming
- JavaScript Cheat Sheet - Learn javascript in one picture (Online version) (PNG version)
- Python Cheat Sheet #1 - Learn python3 in one picture (PNG version)
- Python Cheat Sheet #2 - Learn python3 in one picture (Online version) (PNG version)
- Python Snippets Cheat Sheet - List of helpful re-usable code snippets in Python
Top Related Projects
The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics.
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
articles
A collection of awesome penetration testing resources, tools and other shiny things
This repository contains cutting-edge open-source security tools (OST) for a red teamer and threat hunter.
A collection of hacking / penetration testing resources to make you better!
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot