crowdsec
crowdsec
CrowdSec - the open-source and participative security solution offering crowdsourced protection against malicious IPs and access to the most advanced real-world CTI.
Top Related Projects
Daemon to ban hosts that cause multiple authentication errors
OSSEC is an Open Source Host-based Intrusion Detection System that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response.
ModSecurity is an open source, cross platform web application firewall (WAF) engine for Apache, IIS and Nginx. It has a robust event-based programming language which provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analysis.
Suricata is a network Intrusion Detection System, Intrusion Prevention System and Network Security Monitoring engine developed by the OISF and the Suricata community.
Quick Overview
CrowdSec is an open-source and collaborative security engine designed to protect servers, services, containers, and applications from malicious activities. It analyzes logs and generates security decisions using a behavior-based IP reputation engine, leveraging the power of the crowd to create a real-time global IP reputation database.
Pros
- Community-driven approach for better threat detection and mitigation
- Lightweight and easy to deploy across various environments
- Supports multiple services and platforms out of the box
- Extensible through scenarios, parsers, and bouncers
Cons
- Requires log sources to function effectively
- May generate false positives in certain scenarios
- Learning curve for creating custom scenarios and parsers
- Limited effectiveness against sophisticated attacks that don't rely on IP-based patterns
Getting Started
To get started with CrowdSec, follow these steps:
- Install CrowdSec:
curl -s https://packagecloud.io/install/repositories/crowdsec/crowdsec/script.deb.sh | sudo bash
sudo apt-get install crowdsec
- Enable and start the CrowdSec service:
sudo systemctl enable crowdsec
sudo systemctl start crowdsec
- Check the status and logs:
sudo cscli metrics
sudo cscli decisions list
sudo tail -f /var/log/crowdsec.log
- Install a bouncer (e.g., firewall-bouncer):
sudo apt-get install crowdsec-firewall-bouncer-iptables
- Configure the bouncer and restart services:
sudo systemctl enable crowdsec-firewall-bouncer
sudo systemctl start crowdsec-firewall-bouncer
sudo systemctl restart crowdsec
For more detailed instructions and advanced configurations, refer to the official CrowdSec documentation.
Competitor Comparisons
Daemon to ban hosts that cause multiple authentication errors
Pros of Fail2ban
- Lightweight and easy to set up
- Extensive configuration options for custom rules
- Well-established with a large user base and community support
Cons of Fail2ban
- Limited to log-based detection
- Lacks centralized management for multiple servers
- No built-in threat intelligence sharing
Code Comparison
Fail2ban (Python):
class Jail(JailThread):
def __init__(self, name, backend):
super(Jail, self).__init__(name)
self.__db = None
self.__filter = None
self.__actions = []
CrowdSec (Go):
type Acquisition struct {
Filename string `yaml:"filename"`
Labels []string `yaml:"labels"`
Mode string `yaml:"mode"`
Format string `yaml:"format"`
}
CrowdSec offers a more modern approach to intrusion prevention, focusing on collaborative security and centralized management. It provides real-time threat intelligence sharing and a wider range of detection methods beyond log analysis. However, Fail2ban remains a solid choice for simpler setups and users who prefer fine-grained control over rules and actions. CrowdSec's code structure reflects its modular design and support for various data sources, while Fail2ban's code emphasizes its flexibility in defining jails and actions.
OSSEC is an Open Source Host-based Intrusion Detection System that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response.
Pros of OSSEC-HIDS
- More mature project with a longer history and larger user base
- Offers file integrity monitoring and rootkit detection
- Supports a wider range of operating systems, including legacy systems
Cons of OSSEC-HIDS
- Less frequent updates and slower development cycle
- More complex setup and configuration process
- Steeper learning curve for new users
Code Comparison
OSSEC-HIDS (C):
void OS_CleanMSG(char *msg)
{
char *tmp_str;
char *valid_str;
int size;
tmp_str = msg;
valid_str = msg;
size = strlen(msg);
CrowdSec (Go):
func (c *APIClient) GetDecisions(filter *Decision) ([]Decision, error) {
decisions := []Decision{}
params := url.Values{}
if filter != nil {
params = filter.ToURLParams()
}
Both projects use different programming languages, with OSSEC-HIDS primarily written in C and CrowdSec in Go. This affects performance, maintainability, and ease of contribution. OSSEC-HIDS's C codebase may offer better performance but can be more challenging to maintain, while CrowdSec's Go code is more modern and potentially easier to work with for many developers.
ModSecurity is an open source, cross platform web application firewall (WAF) engine for Apache, IIS and Nginx. It has a robust event-based programming language which provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analysis.
Pros of ModSecurity
- Mature and widely adopted Web Application Firewall (WAF)
- Extensive rule set with OWASP Core Rule Set (CRS)
- Integrates well with popular web servers like Apache and Nginx
Cons of ModSecurity
- Can be complex to configure and maintain
- May introduce performance overhead, especially with large rule sets
- Requires manual rule updates and tuning
Code Comparison
ModSecurity (example rule):
SecRule REQUEST_HEADERS:User-Agent "@contains bad-bot" \
"id:1000,\
phase:1,\
deny,\
status:403,\
msg:'Bad bot detected'"
CrowdSec (example scenario):
type: leaky
name: bad-bot-detection
description: Detect and block bad bots
filter: evt.Meta.log_type == 'access-log' && evt.Parsed.user_agent contains 'bad-bot'
leakspeed: 10s
capacity: 5
blackhole: 1m
labels:
service: http
CrowdSec focuses on collaborative security and uses a different approach to detect and mitigate threats. It's designed to be more user-friendly and community-driven, with automatic updates and a simpler configuration process. However, ModSecurity offers more granular control and a broader set of pre-existing rules, making it suitable for organizations with specific security requirements and the resources to manage a complex WAF setup.
Suricata is a network Intrusion Detection System, Intrusion Prevention System and Network Security Monitoring engine developed by the OISF and the Suricata community.
Pros of Suricata
- More mature and established project with a larger community
- Extensive rule set and support for complex detection scenarios
- High-performance packet processing and multi-threaded architecture
Cons of Suricata
- Steeper learning curve and more complex configuration
- Higher resource consumption, especially for high-speed networks
- Requires more manual tuning and optimization for optimal performance
Code Comparison
Suricata rule example:
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"Potential SQL Injection"; content:"SELECT"; nocase; http_uri; sid:1000001; rev:1;)
CrowdSec scenario example:
type: leaky
name: sql_injection
description: Detect SQL injection attempts
filter: evt.ParsedLine.program == 'nginx'
leakspeed: 10s
capacity: 5
groupby: evt.Meta.source_ip
blackhole: 1m
Both projects offer powerful security capabilities, but Suricata focuses on deep packet inspection and intrusion detection, while CrowdSec emphasizes collaborative threat intelligence and easier deployment. Suricata provides more granular control over detection rules, while CrowdSec offers a more user-friendly approach to threat mitigation.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

CrowdSec is an open-source and participative security solution offering crowdsourced server detection and protection against malicious IPs. Detect and block with our Security Engine, contribute to the network, and enjoy our real-time community blocklist.

Features & Advantages
Versatile Security Engine
CrowdSec Security Engine is an all-in-one IDS/IPS and WAF.
It detects bad behaviors by analyzing log sources and HTTP requests, and allows active remedation thanks to the Remediation Components.
Detection rules are available on our hub under MIT license.
CrowdSec Community Blocklist
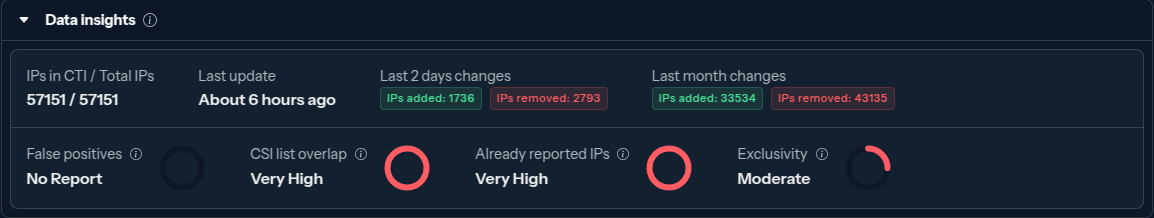
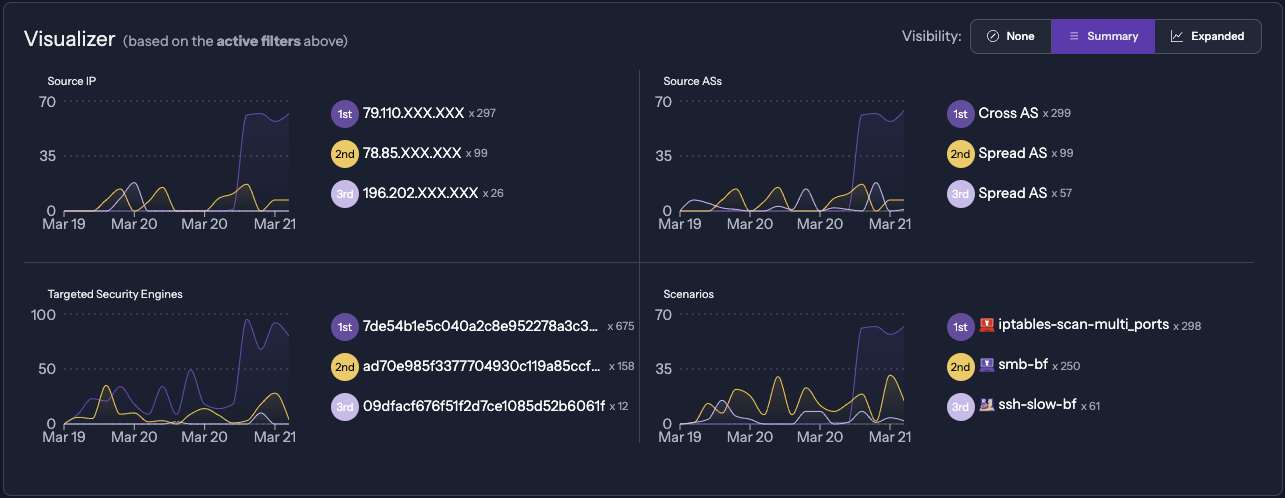
The "Community Blocklist" is a curated list of IP addresses identified as malicious by CrowdSec. The Security Engine proactively block the IP addresses of this blocklist, preventing malevolent IPs from reaching your systems.
Console - Monitoring & Automation of your security stack
Multiple Platforms support
Outnumbering hackers all together
By sharing the threat they faced, all users are protecting each-others (hence the name Crowd-Security). Crowdsec is designed for modern infrastructures, with its "Detect Here, Remedy There" approach, letting you analyze logs coming from several sources in one place and block threats at various levels (applicative, system, infrastructural) of your stack.
CrowdSec ships by default with scenarios (brute force, port scan, web scan, etc.) adapted for most contexts, but you can easily extend it by picking more of them from the HUB. It is also easy to adapt an existing one or create one yourself.
Installation
Resources
- Console: Supercharge your CrowdSec setup with visualization, management capabilities, extra blocklists and premium features.
- Documentation: Learn how to exploit your CrowdSec setup to deter more attacks.
- Discord: A question or a suggestion? This is the place.
- Hub: Improve your stack protection, find the relevant remediation components for your infrastructure.
- CrowdSec Academy: Learn and grow with our courses.
- Corporate Website: For everything else.
Top Related Projects
Daemon to ban hosts that cause multiple authentication errors
OSSEC is an Open Source Host-based Intrusion Detection System that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response.
ModSecurity is an open source, cross platform web application firewall (WAF) engine for Apache, IIS and Nginx. It has a robust event-based programming language which provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analysis.
Suricata is a network Intrusion Detection System, Intrusion Prevention System and Network Security Monitoring engine developed by the OISF and the Suricata community.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot