 osv-scanner
osv-scanner
Vulnerability scanner written in Go which uses the data provided by https://osv.dev
Top Related Projects
A vulnerability scanner for container images and filesystems
Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
Snyk CLI scans and monitors your projects for security vulnerabilities.
🤖 Dependabot's core logic for creating update PRs.
Quick Overview
OSV-Scanner is a vulnerability scanner that uses the Open Source Vulnerability (OSV) database to identify known vulnerabilities in open source dependencies. It supports multiple ecosystems and package formats, providing developers with a tool to check their projects for potential security issues.
Pros
- Supports multiple ecosystems (Go, npm, PyPI, Maven, etc.)
- Uses the comprehensive OSV database for vulnerability information
- Integrates easily with CI/CD pipelines
- Provides detailed vulnerability reports with remediation suggestions
Cons
- May produce false positives in some cases
- Requires regular updates to maintain an up-to-date vulnerability database
- Limited to known vulnerabilities in the OSV database
- Can be resource-intensive for large projects with many dependencies
Getting Started
To install OSV-Scanner, run:
go install github.com/google/osv-scanner/cmd/osv-scanner@v1
To scan a directory:
osv-scanner /path/to/your/project
To scan specific files:
osv-scanner --file=/path/to/requirements.txt --file=/path/to/package-lock.json
For CI/CD integration, add this to your workflow:
- name: Run OSV-Scanner
uses: google/osv-scanner-action@v1
with:
path: "."
Competitor Comparisons
A vulnerability scanner for container images and filesystems
Pros of Grype
- Supports scanning a wide range of package types and ecosystems
- Provides detailed vulnerability information, including severity and fix versions
- Offers flexible output formats (JSON, SARIF, table) for easy integration
Cons of Grype
- Limited to scanning for known vulnerabilities in packages
- May have a larger resource footprint compared to OSV-Scanner
Code Comparison
OSV-Scanner:
osv-scanner /path/to/project
Grype:
grype /path/to/project
Key Differences
- OSV-Scanner focuses on scanning source code and dependencies against the OSV database
- Grype is designed for scanning container images and filesystems for known vulnerabilities
- OSV-Scanner has native integration with Git repositories and commit ranges
- Grype offers more comprehensive package ecosystem coverage
Use Cases
OSV-Scanner is ideal for:
- Continuous integration pipelines for open-source projects
- Developers looking for a lightweight, fast vulnerability scanner
Grype is better suited for:
- Container image scanning in DevSecOps workflows
- Comprehensive vulnerability assessment of complex applications with multiple package types
Both tools contribute to improving software security, but their specific strengths make them suitable for different scenarios in the software development lifecycle.
Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
Pros of Trivy
- Broader scanning capabilities: Trivy can scan container images, filesystems, git repositories, and more, while OSV-Scanner primarily focuses on scanning source code and dependencies.
- Built-in database: Trivy includes a vulnerability database, reducing reliance on external sources for vulnerability information.
- Faster scanning: Trivy is generally known for its quick scanning speed, especially for container images.
Cons of Trivy
- Higher resource usage: Trivy may require more system resources due to its comprehensive scanning capabilities.
- Steeper learning curve: With more features and options, Trivy can be more complex to set up and use effectively.
Code Comparison
Trivy:
trivy image python:3.4-alpine
OSV-Scanner:
osv-scanner --lockfile=/path/to/requirements.txt
Both tools offer command-line interfaces for scanning, but Trivy's command is more focused on container images, while OSV-Scanner is geared towards dependency files.
Snyk CLI scans and monitors your projects for security vulnerabilities.
Pros of Snyk CLI
- Broader ecosystem support, covering more languages and package managers
- Offers remediation advice and automatic fix pull requests
- Integrates with Snyk's vulnerability database and additional security features
Cons of Snyk CLI
- Requires an account and potentially a paid subscription for full functionality
- May have a steeper learning curve due to more extensive features
- Can be slower for large projects due to its comprehensive analysis
Code Comparison
OSV Scanner:
osv-scanner /path/to/project
Snyk CLI:
snyk test /path/to/project
snyk monitor /path/to/project
OSV Scanner focuses on simplicity and ease of use, with a straightforward command to scan a project. Snyk CLI offers more options, including the ability to test and continuously monitor projects for vulnerabilities.
Both tools aim to identify vulnerabilities in open-source dependencies, but they differ in their approach and feature set. OSV Scanner is a lightweight, open-source tool that leverages the OSV database, while Snyk CLI is part of a larger commercial platform with additional security features and integrations.
🤖 Dependabot's core logic for creating update PRs.
Pros of Dependabot-core
- Broader ecosystem support, covering multiple package managers and languages
- Automated pull request creation for dependency updates
- Integration with GitHub's native features and workflows
Cons of Dependabot-core
- More complex setup and configuration compared to OSV-scanner
- Focused primarily on dependency updates rather than comprehensive vulnerability scanning
- May require more resources to run and maintain
Code Comparison
OSV-scanner:
func ScanArtifact(ctx context.Context, a *artifact.Artifact) ([]*osv.Entry, error) {
// Scanning logic
}
Dependabot-core:
def create_pull_request(dependency, version_to_update, updated_version)
# Pull request creation logic
end
While OSV-scanner focuses on direct vulnerability scanning, Dependabot-core emphasizes dependency update automation. OSV-scanner provides a more straightforward approach to identifying vulnerabilities, while Dependabot-core offers a comprehensive solution for managing dependencies within the GitHub ecosystem. The choice between the two depends on specific project needs, with OSV-scanner being more suitable for quick vulnerability checks and Dependabot-core for ongoing dependency management.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

Use OSV-Scanner to find existing vulnerabilities affecting your project's dependencies. OSV-Scanner provides an officially supported frontend to the OSV database and CLI interface to OSV-Scalibr that connects a projectâs list of dependencies with the vulnerabilities that affect them.
OSV-Scanner supports a wide range of project types, package managers and features, including but not limited to:
- Languages: C/C++, Dart, Elixir, Go, Java, Javascript, PHP, Python, R, Ruby, Rust.
- Package Managers: npm, pip, yarn, maven, go modules, cargo, gem, composer, nuget and others.
- Operating Systems: Detects vulnerabilities in OS packages on Linux systems.
- Containers: Scans container images for vulnerabilities in their base images and included packages.
- Guided Remediation: Provides recommendations for package version upgrades based on criteria such as dependency depth, minimum severity, fix strategy, and return on investment.
OSV-Scanner uses the extensible OSV-Scalibr library under the hood to provide this functionality. If a language or package manager is not supported currently, please file a feature request.
Underlying database
The underlying database, OSV.dev has several benefits in comparison with closed source advisory databases and scanners:
- Covering most open source language and OS ecosystems (including Git), itâs comprehensive.
- Each advisory comes from an open and authoritative source (e.g. GitHub Security Advisories, RustSec Advisory Database, Ubuntu security notices)
- Anyone can suggest improvements to advisories, resulting in a very high quality database.
- The OSV format unambiguously stores information about affected versions in a machine-readable format that precisely maps onto a developerâs list of packages
The above all results in accurate and actionable vulnerability notifications, which reduces the time needed to resolve them. Check out OSV.dev for more details!
Basic installation
To install OSV-Scanner, please refer to the installation section of our documentation. OSV-Scanner releases can be found on the releases page of the GitHub repository. The recommended method is to download a prebuilt binary for your platform. Alternatively, you can use
go install github.com/google/osv-scanner/v2/cmd/osv-scanner@latest to build it from source.
Key Features
For more information, please read our detailed documentation to learn how to use OSV-Scanner. For detailed information about each feature, click their titles in this README.
Please note: These are the instructions for the latest OSV-Scanner V2 beta. If you are using V1, checkout the V1 README and documentation instead.
Scanning a source directory
$ osv-scanner scan source -r /path/to/your/dir
This command will recursively scan the specified directory for any supported package files, such as package.json, go.mod, pom.xml, etc. and output any discovered vulnerabilities.
OSV-Scanner has the option of using call analysis to determine if a vulnerable function is actually being used in the project, resulting in fewer false positives, and actionable alerts.
OSV-Scanner can also detect vendored C/C++ code for vulnerability scanning. See here for details.
Supported Lockfiles
OSV-Scanner supports 11+ language ecosystems and 19+ lockfile types. To check if your ecosystem is covered, please check out our detailed documentation.
Container Scanning
OSV-Scanner also supports comprehensive, layer-aware scanning for container images to detect vulnerabilities the following operating system packages and language-specific dependencies.
| Distro Support | Language Artifacts Support |
|---|---|
| Alpine OS | Go |
| Debian | Java |
| Ubuntu | Node |
| Python |
See the full documentation for details on support.
Usage:
$ osv-scanner scan image my-image-name:tag
License Scanning
Check your dependencies' licenses using deps.dev data. For a summary:
osv-scanner --licenses path/to/repository
To check against an allowed license list (SPDX format):
osv-scanner --licenses="MIT,Apache-2.0" path/to/directory
Offline Scanning
Scan your project against a local OSV database. No network connection is required after the initial database download. The database can also be manually downloaded.
osv-scanner --offline --download-offline-databases ./path/to/your/dir
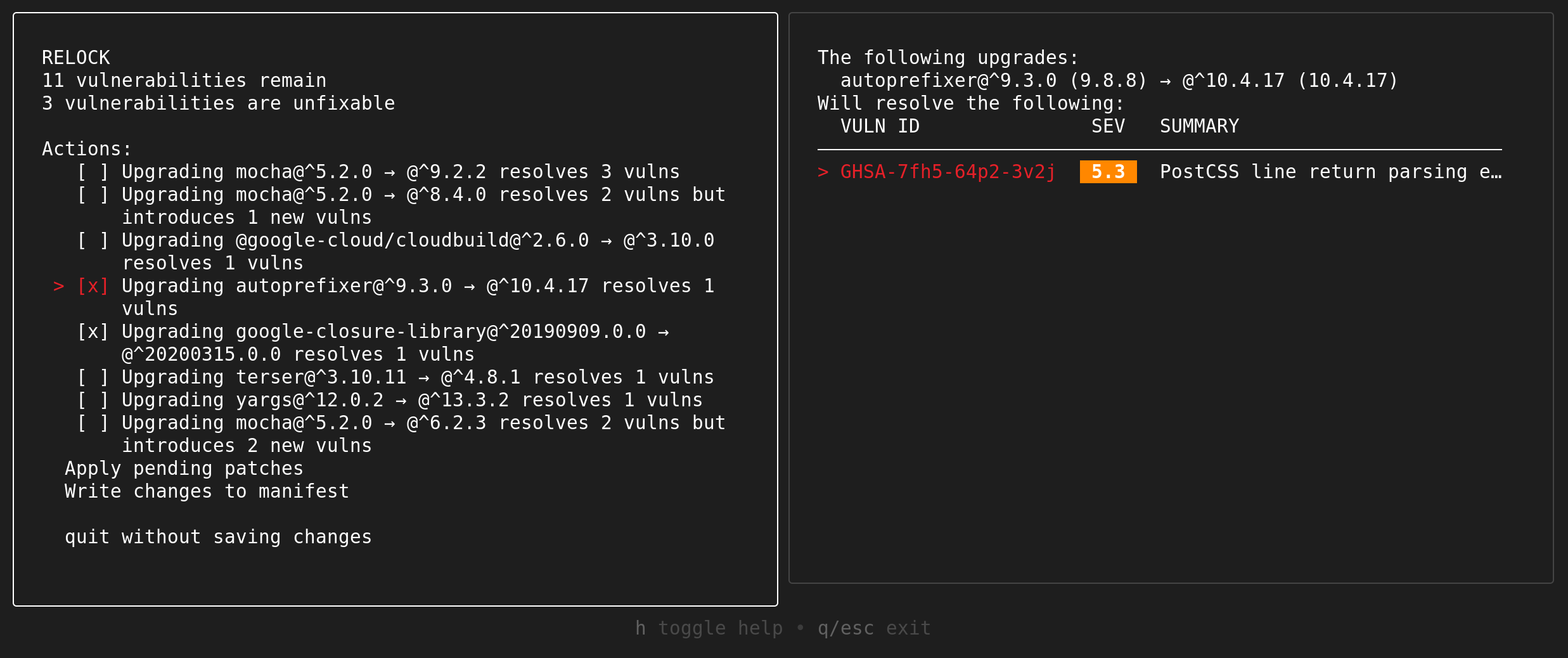
Guided Remediation (Experimental)
OSV-Scanner provides guided remediation, a feature that suggests package version upgrades based on criteria such as dependency depth, minimum severity, fix strategy, and return on investment. We currently support remediating vulnerabilities in the following files:
| Ecosystem | File Format (Type) | Supported Remediation Strategies |
|---|---|---|
| npm | package-lock.json (lockfile) | in-place |
| npm | package.json (manifest) | relock |
| Maven | pom.xml (manifest) | override |
This is available as a headless CLI command, as well as an interactive mode.
Example (for npm)
$ osv-scanner fix \
--max-depth=3 \
--min-severity=5 \
--ignore-dev \
--strategy=in-place \
-L path/to/package-lock.json
Interactive mode (for npm)
$ osv-scanner fix \
-M path/to/package.json \
-L path/to/package-lock.json
Contribute
Report Problems
If you have what looks like a bug, please use the GitHub issue tracking system. Before you file an issue, please search existing issues to see if your issue is already covered.
Contributing code to osv-scanner
See CONTRIBUTING.md for documentation on how to contribute code.
Star History
Top Related Projects
A vulnerability scanner for container images and filesystems
Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
Snyk CLI scans and monitors your projects for security vulnerabilities.
🤖 Dependabot's core logic for creating update PRs.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot
