 laravel-roles
laravel-roles
A Powerful package for handling roles and permissions in Laravel with GUI.
Top Related Projects
Associate users with roles and permissions
Role-based Permissions for Laravel 5
Handle roles and permissions in your Laravel application
A framework agnostic authentication & authorization system.
Quick Overview
Laravel-roles is a comprehensive role and permission management system for Laravel applications. It provides a flexible and easy-to-use solution for implementing user roles, permissions, and access control in Laravel projects. The package offers a robust set of features for managing user roles and permissions, including middleware, blade directives, and helper methods.
Pros
- Easy integration with existing Laravel projects
- Comprehensive set of features for role and permission management
- Well-documented with clear usage instructions
- Actively maintained and regularly updated
Cons
- May be overkill for simple projects with basic role requirements
- Requires additional database tables and migrations
- Learning curve for developers new to role-based access control concepts
- Potential performance impact on large-scale applications with many roles and permissions
Code Examples
- Checking if a user has a specific role:
if ($user->hasRole('admin')) {
// User has admin role
}
- Assigning a role to a user:
$user->attachRole($role);
- Checking if a user has a specific permission:
if ($user->hasPermission('edit-posts')) {
// User has permission to edit posts
}
- Using middleware to restrict access based on role:
Route::group(['middleware' => ['role:admin']], function () {
// Routes accessible only to admin users
});
Getting Started
- Install the package via Composer:
composer require jeremykenedy/laravel-roles
- Publish the package config and migrations:
php artisan vendor:publish --tag=laravelroles
- Run the migrations:
php artisan migrate
- Add the trait to your User model:
use jeremykenedy\LaravelRoles\Traits\HasRoleAndPermission;
class User extends Authenticatable
{
use HasRoleAndPermission;
// ...
}
- Create roles and permissions in your database or through seeders:
use jeremykenedy\LaravelRoles\Models\Role;
use jeremykenedy\LaravelRoles\Models\Permission;
$adminRole = Role::create([
'name' => 'Admin',
'slug' => 'admin',
'description' => 'Administrator role',
'level' => 5,
]);
$editPermission = Permission::create([
'name' => 'Edit Posts',
'slug' => 'edit-posts',
'description' => 'Can edit blog posts',
]);
Now you can start using the package features in your Laravel application.
Competitor Comparisons
Associate users with roles and permissions
Pros of laravel-permission
- More actively maintained with frequent updates
- Extensive documentation and community support
- Seamless integration with Laravel's built-in Gate functionality
Cons of laravel-permission
- Lacks some advanced features like permission inheritance
- May require more setup for complex role-based systems
Code Comparison
laravel-permission:
$user->givePermissionTo('edit articles');
$user->assignRole('writer');
$user->hasRole('writer');
$user->hasPermissionTo('edit articles');
laravel-roles:
$user->attachRole($role);
$user->hasRole($role);
$user->can('permission-name');
$user->level();
Key Differences
- laravel-permission focuses on simplicity and integration with Laravel's core features
- laravel-roles offers additional functionality like permission inheritance and user levels
- laravel-permission uses a more intuitive API for assigning and checking permissions
- laravel-roles provides methods for managing role hierarchies and user levels
Community and Support
laravel-permission has a larger user base and more active community support, with regular updates and contributions. laravel-roles, while still maintained, has less frequent updates and a smaller community.
Integration and Flexibility
laravel-permission integrates seamlessly with Laravel's authorization features, making it easier to use with existing Laravel projects. laravel-roles offers more flexibility in terms of role and permission management, but may require more custom implementation.
Role-based Permissions for Laravel 5
Pros of Entrust
- Simpler and more lightweight implementation
- Easier to set up and integrate into existing projects
- Better documentation and community support
Cons of Entrust
- Less actively maintained (last update in 2019)
- Fewer features compared to Laravel Roles
- Limited flexibility for complex permission structures
Code Comparison
Entrust:
$user->hasRole('admin');
$user->can('edit-post');
$user->attachRole('moderator');
Laravel Roles:
$user->hasRole('admin');
$user->hasPermission('edit.post');
$user->assignRole('moderator');
Key Differences
- Entrust uses
can()for permission checks, while Laravel Roles useshasPermission() - Laravel Roles offers more granular control with methods like
levelCheck()androleHasPermission() - Entrust provides a simpler API, while Laravel Roles offers more advanced features
Conclusion
Entrust is a good choice for simpler projects or those requiring quick integration. Laravel Roles is more suitable for complex applications needing fine-grained access control and active maintenance. Consider your project's specific needs and long-term requirements when choosing between these two packages.
Handle roles and permissions in your Laravel application
Pros of Laratrust
- More actively maintained with frequent updates
- Supports Laravel 10 and PHP 8.2
- Offers a more flexible permission system with teams support
Cons of Laratrust
- Steeper learning curve due to more complex features
- May be overkill for simpler projects
- Requires more configuration and setup
Code Comparison
Laratrust permission check:
if (auth()->user()->isAbleTo('edit-post')) {
// User can edit post
}
Laravel-roles permission check:
if ($user->hasPermission('edit.post')) {
// User can edit post
}
Key Differences
- Laratrust offers a more granular permission system with support for teams and multiple user models
- Laravel-roles provides a simpler, more straightforward approach to role-based access control
- Laratrust has better documentation and more extensive examples
- Laravel-roles includes built-in middleware for role and permission checks
Conclusion
Choose Laratrust for complex, team-based permission systems in larger projects. Opt for Laravel-roles for simpler role-based access control in smaller applications. Consider your project's specific needs, team expertise, and scalability requirements when making your decision.
A framework agnostic authentication & authorization system.
Pros of Sentinel
- More comprehensive authentication system with features like throttling and checkpoints
- Supports multiple user models and providers
- Offers more flexibility in customizing authentication flows
Cons of Sentinel
- Steeper learning curve due to its extensive feature set
- Requires more setup and configuration compared to Laravel Roles
- May be overkill for simpler projects that only need basic role management
Code Comparison
Laravel Roles:
$user->hasRole('admin');
$user->hasPermission('edit.posts');
$user->assignRole('editor');
Sentinel:
Sentinel::getUser()->hasAccess('admin');
Sentinel::getUser()->hasAccess('edit.posts');
Sentinel::findRoleBySlug('editor')->users()->attach($user);
Key Differences
- Laravel Roles focuses primarily on role and permission management, while Sentinel provides a complete authentication solution
- Sentinel uses its own user model and authentication system, whereas Laravel Roles integrates with Laravel's built-in authentication
- Laravel Roles offers a simpler API for common role-based operations, while Sentinel provides more granular control over user access and authentication
Use Cases
- Choose Laravel Roles for projects that need straightforward role and permission management within the Laravel ecosystem
- Opt for Sentinel when building applications requiring advanced authentication features, multiple user types, or custom authentication flows
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

Laravel Roles
A Powerful package for handling roles and permissions in Laravel. Supports Laravel 5.3, 5.4, 5.5, 5.6, 5.7, 5.8, 6.0, 7.0, and 8.0+.
Table of contents
- Features
- Installation
- Usage
- Configuration
- More Information
- Optional GUI Routes
- Screen Shots
- File Tree
- Opening an Issue
- License
Features
| Laravel Roles Features |
|---|
| Built in migrations with ability to publish and modify your own. |
| Built in seed with ability to publish and modify your own. |
| Roles with levels and relationships to users, permissions |
| Permissions with relationships to users and levels |
| Soft deletes with full restore and destroy |
| Optional CRUD of Roles and Permissions |
| Lots of configuration options |
| All Extendable from .env |
Installation
This package is very easy to set up. There are only couple of steps.
Composer
From your projects root folder in terminal run:
Laravel 5.8 and up use:
composer require jeremykenedy/laravel-roles
Laravel 5.7 and below use:
composer require jeremykenedy/laravel-roles:1.4.0
- Note: The major difference is that Laravel's users table migration out the box changed from
$table->increments('id');to$table->bigIncrements('id');in Laravel 5.8.
Service Provider
-
Laravel 5.5 and up Uses package auto discovery feature, no need to edit the
config/app.phpfile. -
Laravel 5.4 and below Add the package to your application service providers in
config/app.phpfile.
'providers' => [
...
/**
* Third Party Service Providers...
*/
jeremykenedy\LaravelRoles\RolesServiceProvider::class,
],
Publish All Assets
php artisan vendor:publish --tag=laravelroles
Publish Specific Assets
php artisan vendor:publish --tag=laravelroles-config
php artisan vendor:publish --tag=laravelroles-migrations
php artisan vendor:publish --tag=laravelroles-seeds
php artisan vendor:publish --tag=laravelroles-views
php artisan vendor:publish --tag=laravelroles-lang
HasRoleAndPermission Trait And Contract
-
Include
HasRoleAndPermissiontrait and also implementHasRoleAndPermissioncontract inside yourUsermodel. See example below. -
Include
use jeremykenedy\LaravelRoles\Traits\HasRoleAndPermission;in the top of yourUsermodel below the namespace and implement theHasRoleAndPermissiontrait. See example below.
Example User model Trait And Contract:
<?php
namespace App;
use Illuminate\Database\Eloquent\Model;
use Illuminate\Notifications\Notifiable;
use jeremykenedy\LaravelRoles\Traits\HasRoleAndPermission;
use Illuminate\Foundation\Auth\User as Authenticatable;
class User extends Authenticatable
{
use Notifiable;
use HasRoleAndPermission;
// rest of your model ...
}
Migrations and seeds
This uses the default users table which is in Laravel. You should already have the migration file for the users table available and migrated.
-
Setup the needed tables:
php artisan migrate -
Update
database\seeds\DatabaseSeeder.phpto include the seeds. See example below.
<?php
use Illuminate\Database\Seeder;
use Illuminate\Database\Eloquent\Model;
use Database\Seeders\PermissionsTableSeeder;
use Database\Seeders\RolesTableSeeder;
use Database\Seeders\ConnectRelationshipsSeeder;
class DatabaseSeeder extends Seeder
{
/**
* Run the database seeds.
*
* @return void
*/
public function run()
{
Model::unguard();
$this->call(PermissionsTableSeeder::class);
$this->call(RolesTableSeeder::class);
$this->call(ConnectRelationshipsSeeder::class);
//$this->call('UsersTableSeeder');
Model::reguard();
}
}
- Seed an initial set of Permissions, Roles, and Users with roles.
composer dump-autoload
php artisan db:seed
Roles Seeded
| Property | Value |
|---|---|
| Name | Admin |
| Slug | admin |
| Description | Admin Role |
| Level | 5 |
| Property | Value |
|---|---|
| Name | User |
| Slug | user |
| Description | User Role |
| Level | 1 |
| Property | Value |
|---|---|
| Name | Unverified |
| Slug | unverified |
| Description | Unverified Role |
| Level | 0 |
Permissions Seeded:
| Property | Value |
|---|---|
| name | Can View Users |
| slug | view.users |
| description | Can view users |
| model | Permission |
| Property | Value |
|---|---|
| name | Can Create Users |
| slug | create.users |
| description | Can create new users |
| model | Permission |
| Property | Value |
|---|---|
| name | Can Edit Users |
| slug | edit.users |
| description | Can edit users |
| model | Permission |
| Property | Value |
|---|---|
| name | Can Delete Users |
| slug | delete.users |
| description | Can delete users |
| model | Permission |
And that's it!
Migrate from bican roles
If you migrate from bican/roles to jeremykenedy/LaravelRoles you will need to update a few things.
- Change all calls to
can,canOneandcanAlltohasPermission,hasOnePermission,hasAllPermissions. - Change all calls to
is,isOneandisAlltohasRole,hasOneRole,hasAllRoles.
Usage
Creating Roles
$adminRole = config('roles.models.role')::create([
'name' => 'Admin',
'slug' => 'admin',
'description' => '',
'level' => 5,
]);
$moderatorRole = config('roles.models.role')::create([
'name' => 'Forum Moderator',
'slug' => 'forum.moderator',
]);
Because of
Slugabletrait, if you make a mistake and for example leave a space in slug parameter, it'll be replaced with a dot automatically, because ofstr_slugfunction.
Attaching, Detaching and Syncing Roles
It's really simple. You fetch a user from database and call attachRole method. There is BelongsToMany relationship between User and Role model.
$user = config('roles.models.defaultUser')::find($id);
$user->attachRole($adminRole); // you can pass whole object, or just an id
$user->detachRole($adminRole); // in case you want to detach role
$user->detachAllRoles(); // in case you want to detach all roles
$user->syncRoles($roles); // you can pass Eloquent collection, or just an array of ids
Assign a user role to new registered users
You can assign the user a role upon the users registration by updating the file app\Http\Controllers\Auth\RegisterController.php.
You can assign a role to a user upon registration by including the needed models and modifying the create() method to attach a user role. See example below:
- Updated
create()method ofapp\Http\Controllers\Auth\RegisterController.php:
protected function create(array $data)
{
$user = config('roles.models.defaultUser')::create([
'name' => $data['name'],
'email' => $data['email'],
'password' => bcrypt($data['password']),
]);
$role = config('roles.models.role')::where('name', '=', 'User')->first(); //choose the default role upon user creation.
$user->attachRole($role);
return $user;
}
Checking For Roles
You can now check if the user has required role.
if ($user->hasRole('admin')) { // you can pass an id or slug
//
}
You can also do this:
if ($user->isAdmin()) {
//
}
And of course, there is a way to check for multiple roles:
if ($user->hasRole(['admin', 'moderator'])) {
/*
| Or alternatively:
| $user->hasRole('admin, moderator'), $user->hasRole('admin|moderator'),
| $user->hasOneRole('admin, moderator'), $user->hasOneRole(['admin', 'moderator']), $user->hasOneRole('admin|moderator')
*/
// The user has at least one of the roles
}
if ($user->hasRole(['admin', 'moderator'], true)) {
/*
| Or alternatively:
| $user->hasRole('admin, moderator', true), $user->hasRole('admin|moderator', true),
| $user->hasAllRoles('admin, moderator'), $user->hasAllRoles(['admin', 'moderator']), $user->hasAllRoles('admin|moderator')
*/
// The user has all roles
}
Levels
When you are creating roles, there is optional parameter level. It is set to 1 by default, but you can overwrite it and then you can do something like this:
if ($user->level() > 4) {
//
}
If user has multiple roles, method
levelreturns the highest one.
Level has also big effect on inheriting permissions. About it later.
Creating Permissions
It's very simple thanks to Permission model called from config('roles.models.permission').
$createUsersPermission = config('roles.models.permission')::create([
'name' => 'Create users',
'slug' => 'create.users',
'description' => '', // optional
]);
$deleteUsersPermission = config('roles.models.permission')::create([
'name' => 'Delete users',
'slug' => 'delete.users',
]);
Attaching, Detaching and Syncing Permissions
You can attach permissions to a role or directly to a specific user (and of course detach them as well).
$role = config('roles.models.role')::find($roleId);
$role->attachPermission($createUsersPermission); // permission attached to a role
$user = config('roles.models.defaultUser')::find($userId);
$user->attachPermission($deleteUsersPermission); // permission attached to a user
$role->detachPermission($createUsersPermission); // in case you want to detach permission
$role->detachAllPermissions(); // in case you want to detach all permissions
$role->syncPermissions($permissions); // you can pass Eloquent collection, or just an array of ids
$user->detachPermission($deleteUsersPermission);
$user->detachAllPermissions();
$user->syncPermissions($permissions); // you can pass Eloquent collection, or just an array of ids
Checking For Permissions
if ($user->hasPermission('create.users')) { // you can pass an id or slug
//
}
if ($user->canDeleteUsers()) {
//
}
You can check for multiple permissions the same way as roles. You can make use of additional methods like hasOnePermission or hasAllPermissions.
Permissions Inheritance
By default, roles with higher level inherit all permissions from roles with lower level.
For example:
You have three roles: user, moderator and admin. User has a permission to read articles, moderator can manage comments and admin can create articles. User has a level 1, moderator level 2 and admin level 3. With inheritance enabled, moderator and administrator also have the permission to read articles, and administrator can manage comments as well.
If you don't want the permissions inheritance feature enabled in you application, set the config value roles.inheritance (or its corresponding .env parameter, ROLES_INHERITANCE) to false. Alternatively, simply ignore the
levelparameter when you're creating roles.
Entity Check
Let's say you have an article and you want to edit it. This article belongs to a user (there is a column user_id in articles table).
use App\Article;
$editArticlesPermission = config('roles.models.permission')::create([
'name' => 'Edit articles',
'slug' => 'edit.articles',
'model' => 'App\Article',
]);
$user->attachPermission($editArticlesPermission);
$article = Article::find(1);
if ($user->allowed('edit.articles', $article)) { // $user->allowedEditArticles($article)
//
}
This condition checks if the current user is the owner of article. If not, it will be looking inside user permissions for a row we created before.
if ($user->allowed('edit.articles', $article, false)) { // now owner check is disabled
//
}
Blade Extensions
There are four Blade extensions. Basically, it is replacement for classic if statements.
@role('admin') // @if(Auth::check() && Auth::user()->hasRole('admin'))
// user has admin role
@endrole
@permission('edit.articles') // @if(Auth::check() && Auth::user()->hasPermission('edit.articles'))
// user has edit articles permissison
@endpermission
@level(2) // @if(Auth::check() && Auth::user()->level() >= 2)
// user has level 2 or higher
@endlevel
@allowed('edit', $article) // @if(Auth::check() && Auth::user()->allowed('edit', $article))
// show edit button
@endallowed
@role('admin|moderator', true) // @if(Auth::check() && Auth::user()->hasRole('admin|moderator', true))
// user has admin and moderator role
@else
// something else
@endrole
Middleware
This package comes with VerifyRole, VerifyPermission and VerifyLevel middleware.
The middleware aliases are already registered in \jeremykenedy\LaravelRoles\RolesServiceProvider as of 1.7.
You can optionally add them inside your app/Http/Kernel.php file with your own aliases like outlined below:
/**
* The application's route middleware.
*
* @var array
*/
protected $routeMiddleware = [
'auth' => \App\Http\Middleware\Authenticate::class,
'auth.basic' => \Illuminate\Auth\Middleware\AuthenticateWithBasicAuth::class,
'bindings' => \Illuminate\Routing\Middleware\SubstituteBindings::class,
'cache.headers' => \Illuminate\Http\Middleware\SetCacheHeaders::class,
'can' => \Illuminate\Auth\Middleware\Authorize::class,
'guest' => \App\Http\Middleware\RedirectIfAuthenticated::class,
'signed' => \Illuminate\Routing\Middleware\ValidateSignature::class,
'throttle' => \Illuminate\Routing\Middleware\ThrottleRequests::class,
'verified' => \Illuminate\Auth\Middleware\EnsureEmailIsVerified::class,
'role' => \jeremykenedy\LaravelRoles\App\Http\Middleware\VerifyRole::class,
'permission' => \jeremykenedy\LaravelRoles\App\Http\Middleware\VerifyPermission::class,
'level' => \jeremykenedy\LaravelRoles\App\Http\Middleware\VerifyLevel::class,
];
Now you can easily protect your routes.
Route::get('/', function () {
//
})->middleware('role:admin');
Route::get('/', function () {
//
})->middleware('permission:edit.articles');
Route::get('/', function () {
//
})->middleware('level:2'); // level >= 2
Route::get('/', function () {
//
})->middleware('role:admin', 'level:2'); // level >= 2 and Admin
Route::group(['middleware' => ['role:admin']], function () {
//
});
It throws \jeremykenedy\LaravelRoles\App\Exceptions\RoleDeniedException, \jeremykenedy\LaravelRoles\App\Exceptions\PermissionDeniedException or \jeremykenedy\LaravelRoles\App\Exceptions\LevelDeniedException exceptions if it goes wrong.
You can catch these exceptions inside app/Exceptions/Handler.php file and do whatever you want.
/**
* Render an exception into an HTTP response.
*
* @param \Illuminate\Http\Request $request
* @param \Throwable $e
* @return \Illuminate\Http\Response
*/
public function render($request, Throwable $e)
{
$userLevelCheck = $e instanceof \jeremykenedy\LaravelRoles\App\Exceptions\RoleDeniedException ||
$e instanceof \jeremykenedy\LaravelRoles\App\Exceptions\PermissionDeniedException ||
$e instanceof \jeremykenedy\LaravelRoles\App\Exceptions\LevelDeniedException;
if ($userLevelCheck) {
if ($request->expectsJson()) {
return Response::json(array(
'error' => 403,
'message' => 'Unauthorized.'
), 403);
}
abort(403);
}
return parent::render($request, $e);
}
Configuration
- You can change connection for models, slug separator, models path and there is also a handy pretend feature.
- There are many configurable options which have been extended to be able to configured via
.envfile variables. - Editing the configuration file directly may not needed becuase of this.
- See config file: roles.php.
<?php
return [
/*
|--------------------------------------------------------------------------
| Package Connection
|--------------------------------------------------------------------------
|
| You can set a different database connection for this package. It will set
| new connection for models Role and Permission. When this option is null,
| it will connect to the main database, which is set up in database.php
|
*/
'connection' => env('ROLES_DATABASE_CONNECTION', null),
'rolesTable' => env('ROLES_ROLES_DATABASE_TABLE', 'roles'),
'roleUserTable' => env('ROLES_ROLE_USER_DATABASE_TABLE', 'role_user'),
'permissionsTable' => env('ROLES_PERMISSIONS_DATABASE_TABLE', 'permissions'),
'permissionsRoleTable' => env('ROLES_PERMISSION_ROLE_DATABASE_TABLE', 'permission_role'),
'permissionsUserTable' => env('ROLES_PERMISSION_USER_DATABASE_TABLE', 'permission_user'),
/*
|--------------------------------------------------------------------------
| Slug Separator
|--------------------------------------------------------------------------
|
| Here you can change the slug separator. This is very important in matter
| of magic method __call() and also a `Slugable` trait. The default value
| is a dot.
|
*/
'separator' => env('ROLES_DEFAULT_SEPARATOR', '.'),
/*
|--------------------------------------------------------------------------
| Models
|--------------------------------------------------------------------------
|
| If you want, you can replace default models from this package by models
| you created. Have a look at `jeremykenedy\LaravelRoles\Models\Role` model and
| `jeremykenedy\LaravelRoles\Models\Permission` model.
|
*/
'models' => [
'role' => env('ROLES_DEFAULT_ROLE_MODEL', jeremykenedy\LaravelRoles\Models\Role::class),
'permission' => env('ROLES_DEFAULT_PERMISSION_MODEL', jeremykenedy\LaravelRoles\Models\Permission::class),
'defaultUser' => env('ROLES_DEFAULT_USER_MODEL', config('auth.providers.users.model')),
],
/*
|--------------------------------------------------------------------------
| Roles, Permissions and Allowed "Pretend"
|--------------------------------------------------------------------------
|
| You can pretend or simulate package behavior no matter what is in your
| database. It is really useful when you are testing you application.
| Set up what will methods hasRole(), hasPermission() and allowed() return.
|
*/
'pretend' => [
'enabled' => false,
'options' => [
'hasRole' => true,
'hasPermission' => true,
'allowed' => true,
],
],
/*
|--------------------------------------------------------------------------
| Default Migrations
|--------------------------------------------------------------------------
|
| These are the default package migrations. If you publish the migrations
| to your project, then this is not necessary and should be disabled. This
| will enable our default migrations.
|
*/
'defaultMigrations' => [
'enabled' => env('ROLES_MIGRATION_DEFAULT_ENABLED', false),
],
/*
|--------------------------------------------------------------------------
| Default Seeds
|--------------------------------------------------------------------------
|
| These are the default package seeds. You can seed the package built
| in seeds without having to seed them. These seed directly from
| the package. These are not the published seeds.
|
*/
'defaultSeeds' => [
'PermissionsTableSeeder' => env('ROLES_SEED_DEFAULT_PERMISSIONS', true),
'RolesTableSeeder' => env('ROLES_SEED_DEFAULT_ROLES', true),
'ConnectRelationshipsSeeder' => env('ROLES_SEED_DEFAULT_RELATIONSHIPS', true),
'UsersTableSeeder' => env('ROLES_SEED_DEFAULT_USERS', false),
],
/*
|--------------------------------------------------------------------------
| Laravel Roles GUI Settings
|--------------------------------------------------------------------------
|
| This is the GUI for Laravel Roles to be able to CRUD them
| easily and fast. This is optional and is not needed
| for your application.
|
*/
// Enable Optional Roles Gui
'rolesGuiEnabled' => env('ROLES_GUI_ENABLED', false),
// Enable `auth` middleware
'rolesGuiAuthEnabled' => env('ROLES_GUI_AUTH_ENABLED', true),
// Enable Roles GUI middleware
'rolesGuiMiddlewareEnabled' => env('ROLES_GUI_MIDDLEWARE_ENABLED', true),
// Optional Roles GUI Middleware
'rolesGuiMiddleware' => env('ROLES_GUI_MIDDLEWARE', 'role:admin'),
// User Permissions or Role needed to create a new role
'rolesGuiCreateNewRolesMiddlewareType' => env('ROLES_GUI_CREATE_ROLE_MIDDLEWARE_TYPE', 'role'), //permissions or roles
'rolesGuiCreateNewRolesMiddleware' => env('ROLES_GUI_CREATE_ROLE_MIDDLEWARE_TYPE', 'admin'), // admin, XXX. ... or perms.XXX
// User Permissions or Role needed to create a new permission
'rolesGuiCreateNewPermissionMiddlewareType' => env('ROLES_GUI_CREATE_PERMISSION_MIDDLEWARE_TYPE', 'role'), //permissions or roles
'rolesGuiCreateNewPermissionsMiddleware' => env('ROLES_GUI_CREATE_PERMISSION_MIDDLEWARE_TYPE', 'admin'), // admin, XXX. ... or perms.XXX
// The parent blade file
'bladeExtended' => env('ROLES_GUI_BLADE_EXTENDED', 'layouts.app'),
// Blade Extension Placement
'bladePlacement' => env('ROLES_GUI_BLADE_PLACEMENT', 'yield'),
'bladePlacementCss' => env('ROLES_GUI_BLADE_PLACEMENT_CSS', 'inline_template_linked_css'),
'bladePlacementJs' => env('ROLES_GUI_BLADE_PLACEMENT_JS', 'inline_footer_scripts'),
// Titles placement extend
'titleExtended' => env('ROLES_GUI_TITLE_EXTENDED', 'template_title'),
// Switch Between bootstrap 3 `panel` and bootstrap 4 `card` classes
'bootstapVersion' => env('ROLES_GUI_BOOTSTRAP_VERSION', '4'),
// Additional Card classes for styling -
// See: https://getbootstrap.com/docs/4.0/components/card/#background-and-color
// Example classes: 'text-white bg-primary mb-3'
'bootstrapCardClasses' => env('ROLES_GUI_CARD_CLASSES', ''),
// Bootstrap Tooltips
'tooltipsEnabled' => env('ROLES_GUI_TOOLTIPS_ENABLED', true),
// jQuery
'enablejQueryCDN' => env('ROLES_GUI_JQUERY_CDN_ENABLED', true),
'JQueryCDN' => env('ROLES_GUI_JQUERY_CDN_URL', 'https://code.jquery.com/jquery-3.3.1.min.js'),
// Selectize JS
'enableSelectizeJsCDN' => env('ROLES_GUI_SELECTIZEJS_CDN_ENABLED', true),
'SelectizeJsCDN' => env('ROLES_GUI_SELECTIZEJS_CDN_URL', 'https://cdnjs.cloudflare.com/ajax/libs/selectize.js/0.12.6/js/standalone/selectize.min.js'),
'enableSelectizeJs' => env('ROLES_GUI_SELECTIZEJS_ENABLED', true),
'enableSelectizeJsCssCDN' => env('ROLES_GUI_SELECTIZEJS_CSS_CDN_ENABLED', true),
'SelectizeJsCssCDN' => env('ROLES_GUI_SELECTIZEJS_CSS_CDN_URL', 'https://cdnjs.cloudflare.com/ajax/libs/selectize.js/0.12.6/css/selectize.min.css'),
// Font Awesome
'enableFontAwesomeCDN' => env('ROLES_GUI_FONT_AWESOME_CDN_ENABLED', true),
'fontAwesomeCDN' => env('ROLES_GUI_FONT_AWESOME_CDN_URL', 'https://maxcdn.bootstrapcdn.com/font-awesome/4.7.0/css/font-awesome.min.css'),
// Flash Messaging
'builtInFlashMessagesEnabled' => env('ROLES_GUI_FLASH_MESSAGES_ENABLED', true),
/*
|--------------------------------------------------------------------------
| Laravel Roles API Settings
|--------------------------------------------------------------------------
|
| This is the API for Laravel Roles to be able to CRUD them
| easily and fast via an API. This is optional and is
| not needed for your application.
|
*/
'rolesApiEnabled' => env('ROLES_API_ENABLED', false),
// Enable `auth` middleware
'rolesAPIAuthEnabled' => env('ROLES_API_AUTH_ENABLED', true),
// Enable Roles API middleware
'rolesAPIMiddlewareEnabled' => env('ROLES_API_MIDDLEWARE_ENABLED', true),
// Optional Roles API Middleware
'rolesAPIMiddleware' => env('ROLES_API_MIDDLEWARE', 'role:admin'),
// User Permissions or Role needed to create a new role
'rolesAPICreateNewRolesMiddlewareType' => env('ROLES_API_CREATE_ROLE_MIDDLEWARE_TYPE', 'role'), //permissions or roles
'rolesAPICreateNewRolesMiddleware' => env('ROLES_API_CREATE_ROLE_MIDDLEWARE_TYPE', 'admin'), // admin, XXX. ... or perms.XXX
// User Permissions or Role needed to create a new permission
'rolesAPICreateNewPermissionMiddlewareType' => env('ROLES_API_CREATE_PERMISSION_MIDDLEWARE_TYPE', 'role'), //permissions or roles
'rolesAPICreateNewPermissionsMiddleware' => env('ROLES_API_CREATE_PERMISSION_MIDDLEWARE_TYPE', 'admin'), // admin, XXX. ... or perms.XXX
/*
|--------------------------------------------------------------------------
| Laravel Roles GUI Datatables Settings
|--------------------------------------------------------------------------
*/
'enabledDatatablesJs' => env('ROLES_GUI_DATATABLES_JS_ENABLED', false),
'datatablesJsStartCount' => env('ROLES_GUI_DATATABLES_JS_START_COUNT', 25),
'datatablesCssCDN' => env('ROLES_GUI_DATATABLES_CSS_CDN', 'https://cdn.datatables.net/1.10.19/css/dataTables.bootstrap4.min.css'),
'datatablesJsCDN' => env('ROLES_GUI_DATATABLES_JS_CDN', 'https://cdn.datatables.net/1.10.19/js/jquery.dataTables.min.js'),
'datatablesJsPresetCDN' => env('ROLES_GUI_DATATABLES_JS_PRESET_CDN', 'https://cdn.datatables.net/1.10.19/js/dataTables.bootstrap4.min.js'),
/*
|--------------------------------------------------------------------------
| Laravel Roles Package Integration Settings
|--------------------------------------------------------------------------
*/
'laravelUsersEnabled' => env('ROLES_GUI_LARAVEL_ROLES_ENABLED', false),
];
Environment File
# Roles Default Models
ROLES_DEFAULT_USER_MODEL=App\User
ROLES_DEFAULT_ROLE_MODEL=jeremykenedy\LaravelRoles\Models\Role
ROLES_DEFAULT_PERMISSION_MODEL=jeremykenedy\LaravelRoles\Models\Permission
# Roles database information
ROLES_DATABASE_CONNECTION=null
ROLES_ROLES_DATABASE_TABLE=roles
ROLES_ROLE_USER_DATABASE_TABLE=role_user
ROLES_PERMISSIONS_DATABASE_TABLE=permissions
ROLES_PERMISSION_ROLE_DATABASE_TABLE=permission_role
ROLES_PERMISSION_USER_DATABASE_TABLE=permission_user
# Roles Misc Settings
ROLES_DEFAULT_SEPARATOR='.'
# Roles Database Migrations Settings
ROLES_MIGRATION_DEFAULT_ENABLED=true
# Roles Database Seeder Settings
ROLES_SEED_DEFAULT_PERMISSIONS=true
ROLES_SEED_DEFAULT_ROLES=true
ROLES_SEED_DEFAULT_RELATIONSHIPS=true
ROLES_SEED_DEFAULT_USERS=false
# Roles GUI Settings
ROLES_GUI_ENABLED=false
ROLES_GUI_AUTH_ENABLED=true
ROLES_GUI_MIDDLEWARE_ENABLED=true
ROLES_GUI_MIDDLEWARE='role:admin'
ROLES_GUI_CREATE_ROLE_MIDDLEWARE_TYPE='role'
ROLES_GUI_CREATE_ROLE_MIDDLEWARE_TYPE='admin'
ROLES_GUI_CREATE_PERMISSION_MIDDLEWARE_TYPE='role'
ROLES_GUI_CREATE_PERMISSION_MIDDLEWARE_TYPE='admin'
ROLES_GUI_BLADE_EXTENDED='layouts.app'
ROLES_GUI_TITLE_EXTENDED='template_title'
ROLES_GUI_LARAVEL_ROLES_ENABLED=false
ROLES_GUI_TOOLTIPS_ENABLED=true
ROLES_GUI_DATATABLES_JS_ENABLED=false
More Information
For more information, please have a look at HasRoleAndPermission contract.
Optional GUI Routes
+--------+-----------+---------------------------------+-----------------------------------------------+-----------------------------------------------------------------------------------------------------------------+---------------------+
| Domain | Method | URI | Name | Action | Middleware |
+--------+-----------+---------------------------------+-----------------------------------------------+-----------------------------------------------------------------------------------------------------------------+---------------------+
| | GET|HEAD | permission-deleted/{id} | laravelroles::permission-show-deleted | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelpermissionsDeletedController@show | web,auth,role:admin |
| | DELETE | permission-destroy/{id} | laravelroles::permission-item-destroy | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelpermissionsDeletedController@destroy | web,auth,role:admin |
| | PUT | permission-restore/{id} | laravelroles::permission-restore | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelpermissionsDeletedController@restorePermission | web,auth,role:admin |
| | POST | permissions | laravelroles::permissions.store | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@store | web,auth,role:admin |
| | GET|HEAD | permissions | laravelroles::permissions.index | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@index | web,auth,role:admin |
| | GET|HEAD | permissions-deleted | laravelroles::permissions-deleted | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelpermissionsDeletedController@index | web,auth,role:admin |
| | DELETE | permissions-deleted-destroy-all | laravelroles::destroy-all-deleted-permissions | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelpermissionsDeletedController@destroyAllDeletedPermissions | web,auth,role:admin |
| | POST | permissions-deleted-restore-all | laravelroles::permissions-deleted-restore-all | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelpermissionsDeletedController@restoreAllDeletedPermissions | web,auth,role:admin |
| | GET|HEAD | permissions/create | laravelroles::permissions.create | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@create | web,auth,role:admin |
| | PUT|PATCH | permissions/{permission} | laravelroles::permissions.update | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@update | web,auth,role:admin |
| | GET|HEAD | permissions/{permission} | laravelroles::permissions.show | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@show | web,auth,role:admin |
| | DELETE | permissions/{permission} | laravelroles::permissions.destroy | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@destroy | web,auth,role:admin |
| | GET|HEAD | permissions/{permission}/edit | laravelroles::permissions.edit | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelPermissionsController@edit | web,auth,role:admin |
| | GET|HEAD | role-deleted/{id} | laravelroles::role-show-deleted | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesDeletedController@show | web,auth,role:admin |
| | DELETE | role-destroy/{id} | laravelroles::role-item-destroy | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesDeletedController@destroy | web,auth,role:admin |
| | PUT | role-restore/{id} | laravelroles::role-restore | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesDeletedController@restoreRole | web,auth,role:admin |
| | POST | roles | laravelroles::roles.store | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@store | web,auth,role:admin |
| | GET|HEAD | roles | laravelroles::roles.index | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@index | web,auth,role:admin |
| | GET|HEAD | roles-deleted | laravelroles::roles-deleted | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesDeletedController@index | web,auth,role:admin |
| | DELETE | roles-deleted-destroy-all | laravelroles::destroy-all-deleted-roles | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesDeletedController@destroyAllDeletedRoles | web,auth,role:admin |
| | POST | roles-deleted-restore-all | laravelroles::roles-deleted-restore-all | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesDeletedController@restoreAllDeletedRoles | web,auth,role:admin |
| | GET|HEAD | roles/create | laravelroles::roles.create | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@create | web,auth,role:admin |
| | DELETE | roles/{role} | laravelroles::roles.destroy | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@destroy | web,auth,role:admin |
| | PUT|PATCH | roles/{role} | laravelroles::roles.update | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@update | web,auth,role:admin |
| | GET|HEAD | roles/{role} | laravelroles::roles.show | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@show | web,auth,role:admin |
| | GET|HEAD | roles/{role}/edit | laravelroles::roles.edit | jeremykenedy\LaravelRoles\App\Http\Controllers\LaravelRolesController@edit | web,auth,role:admin |
+--------+-----------+---------------------------------+-----------------------------------------------+-----------------------------------------------------------------------------------------------------------------+---------------------+
Screen Shots
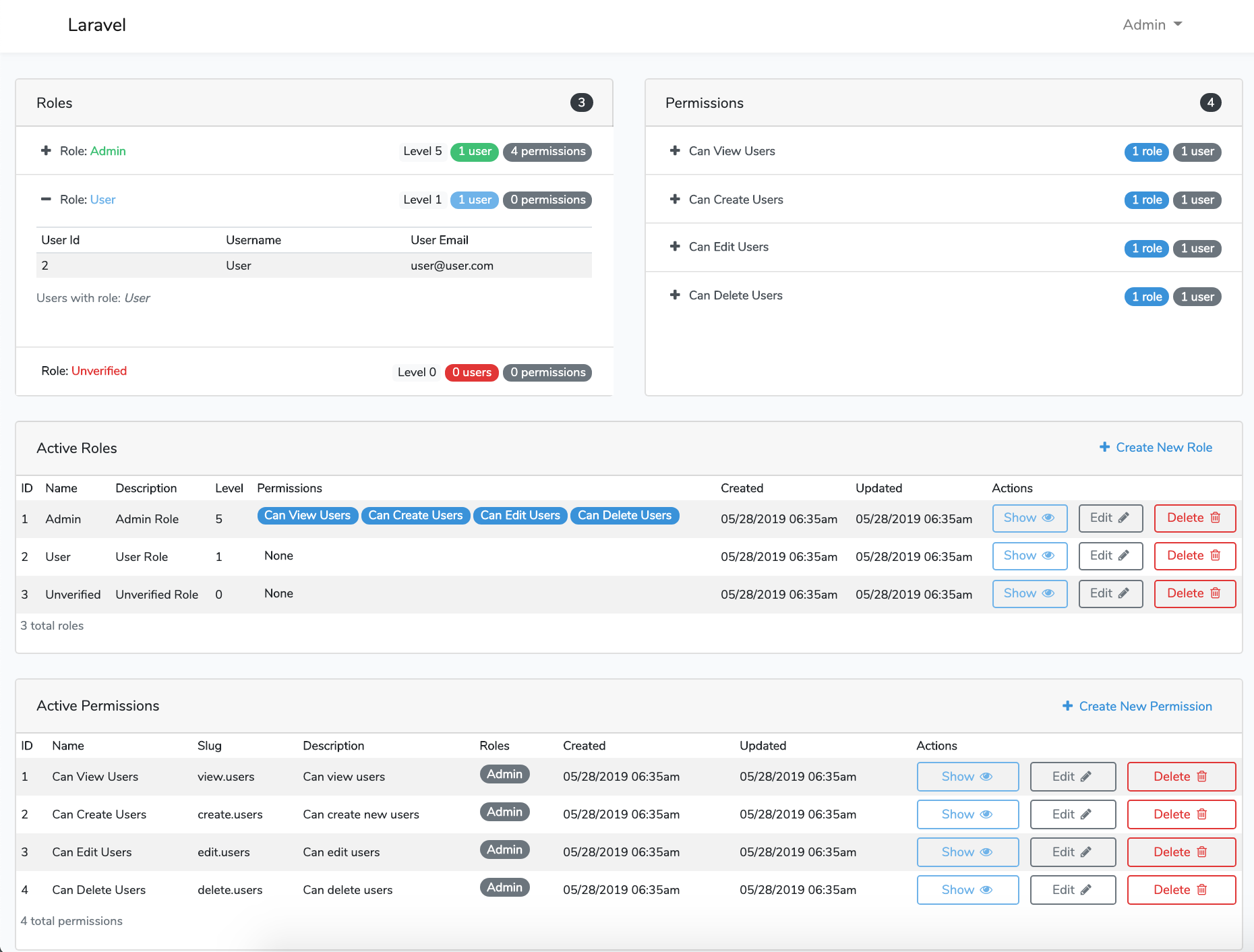
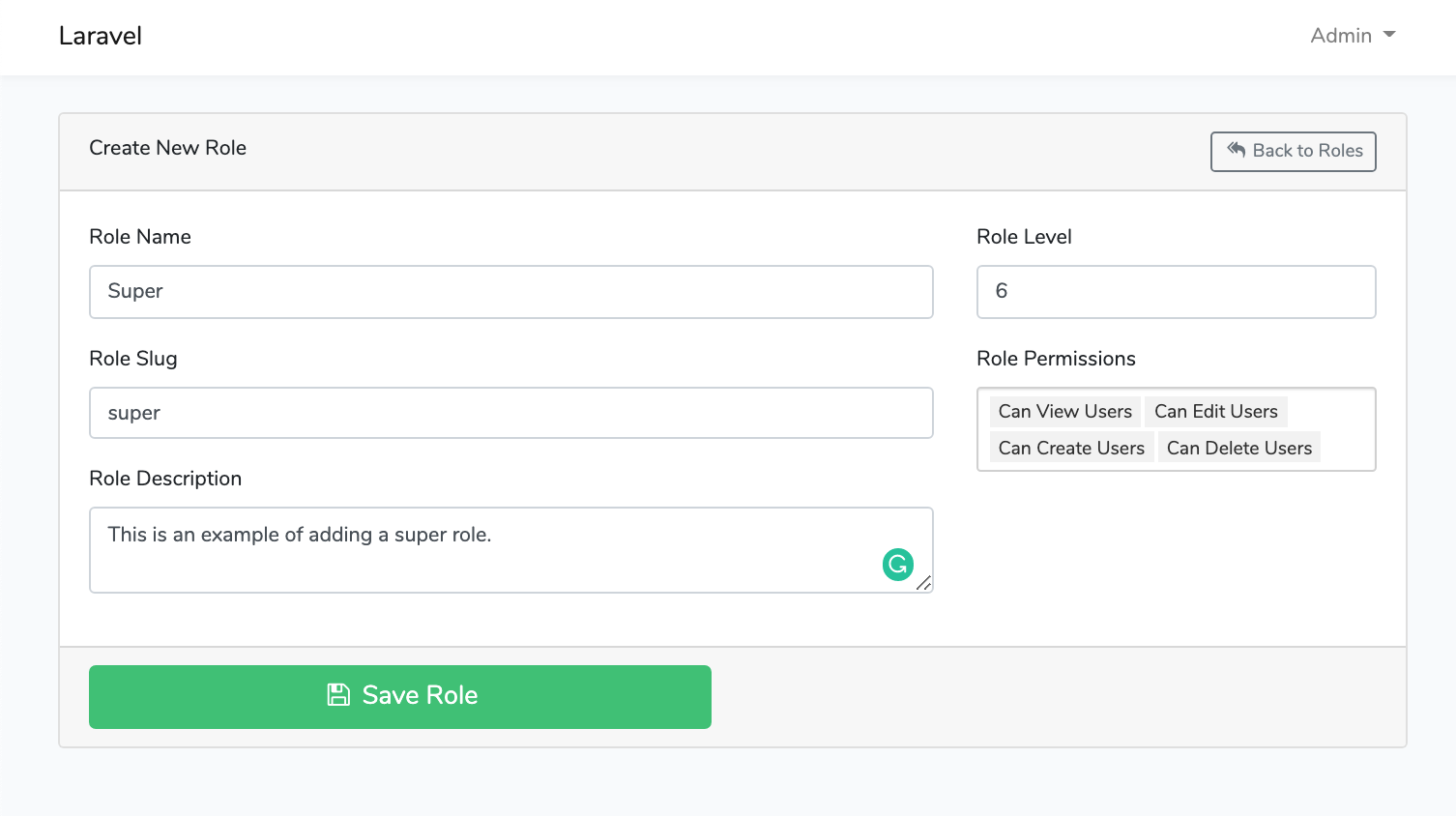
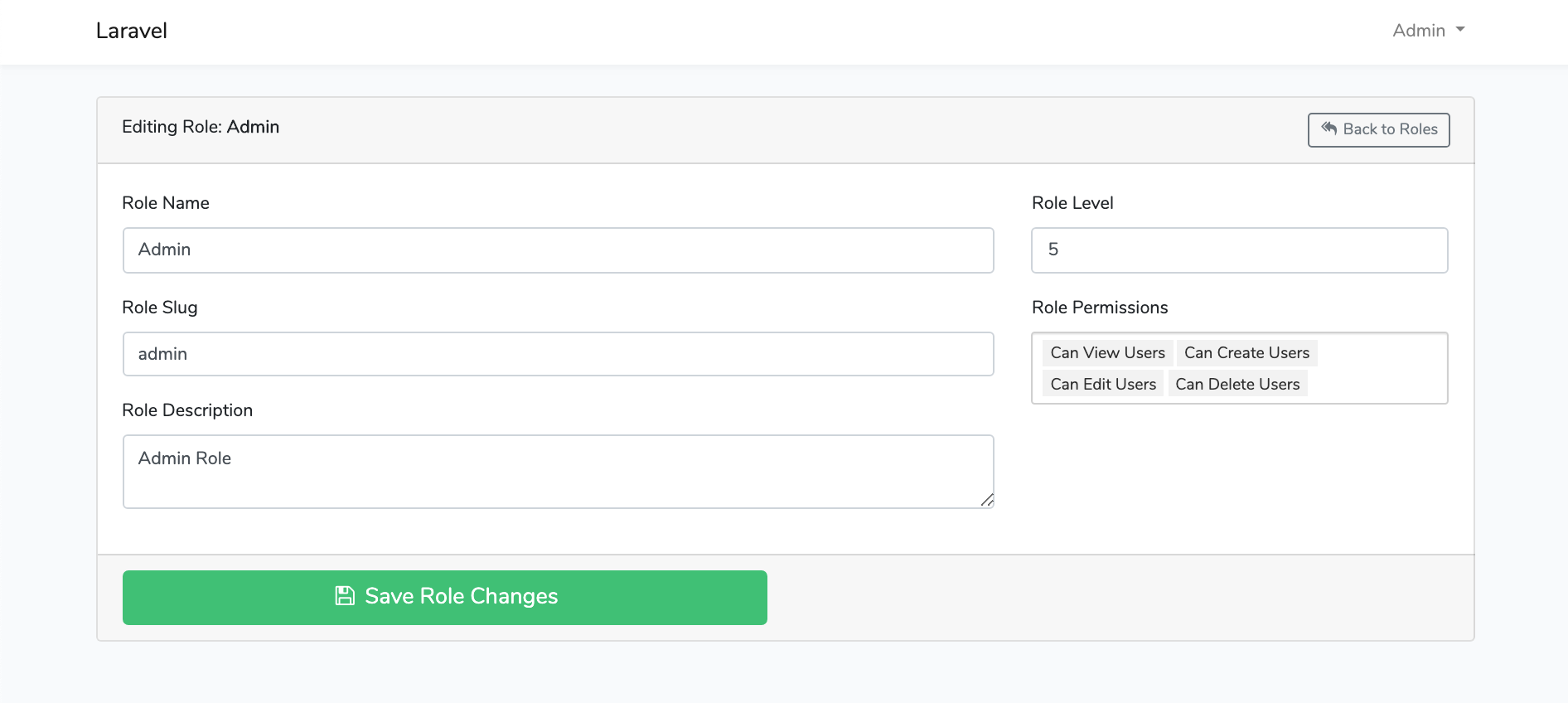
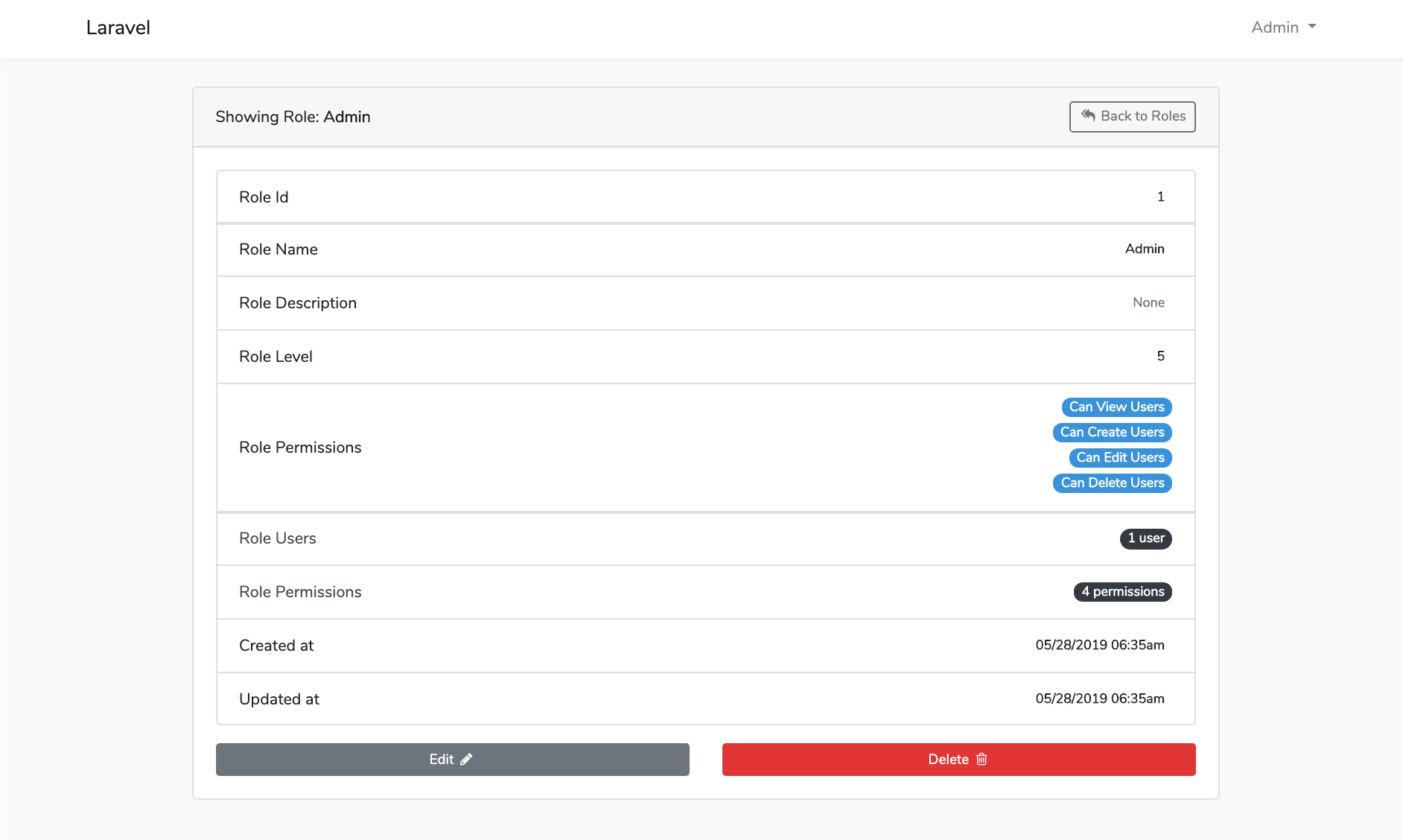
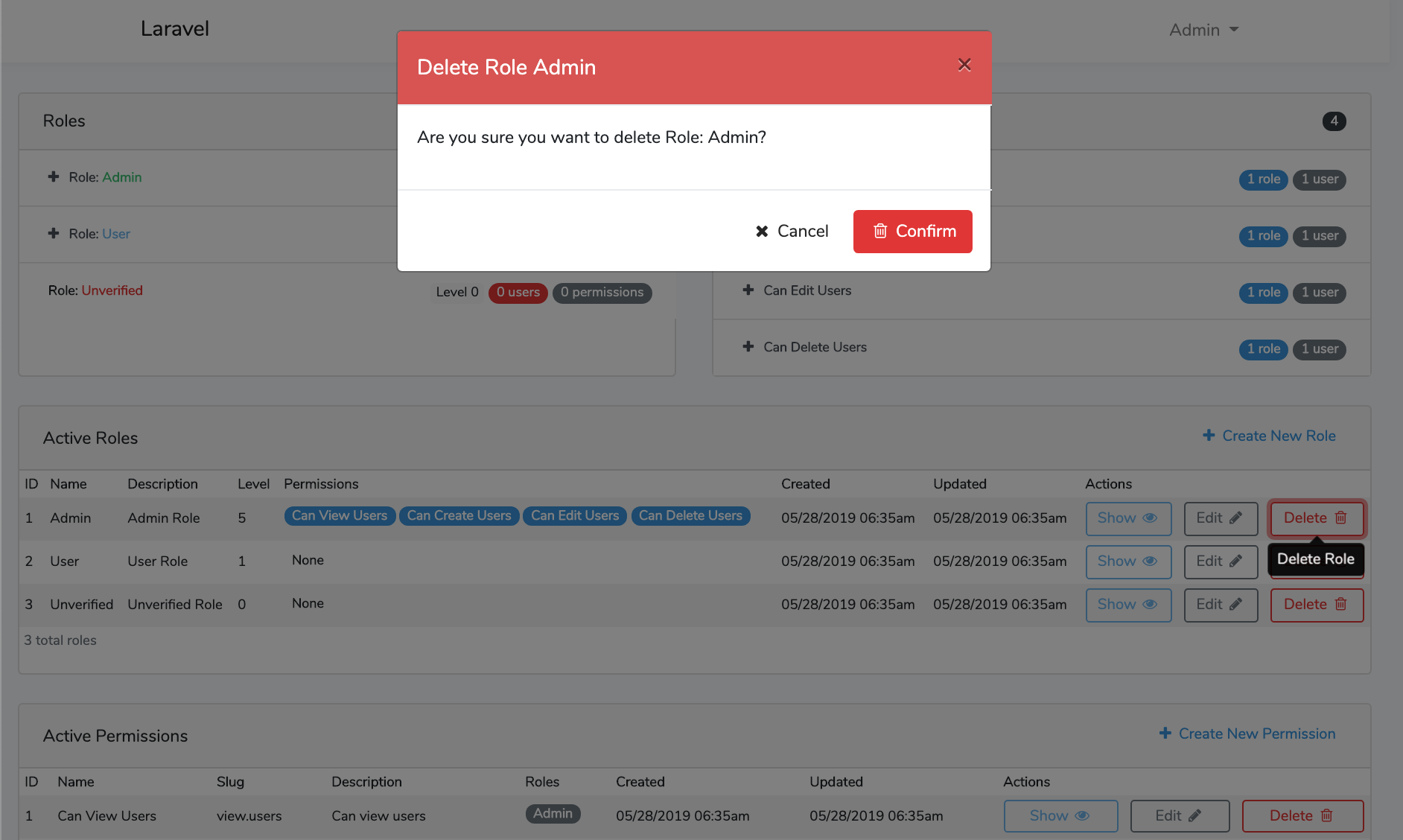
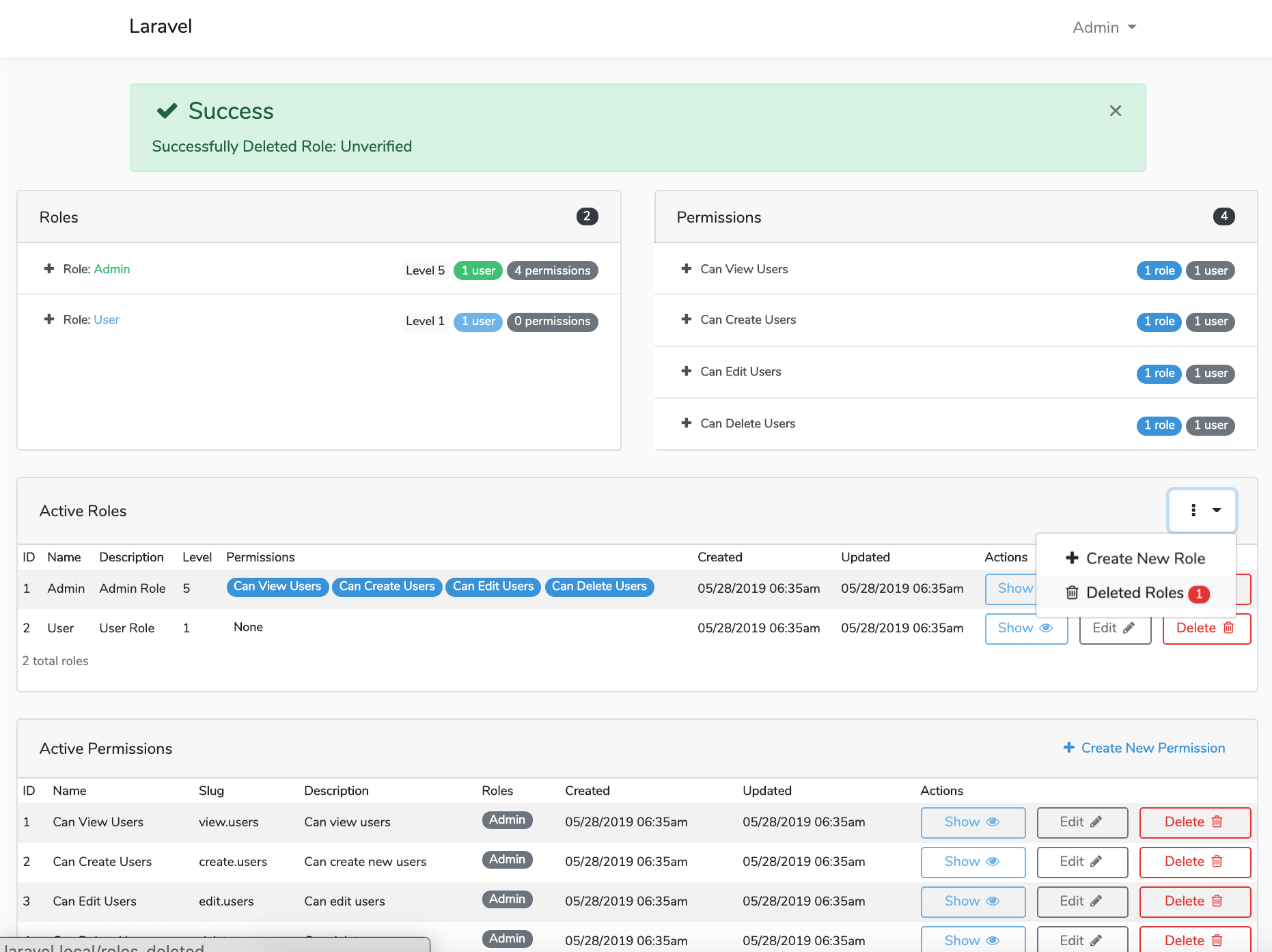
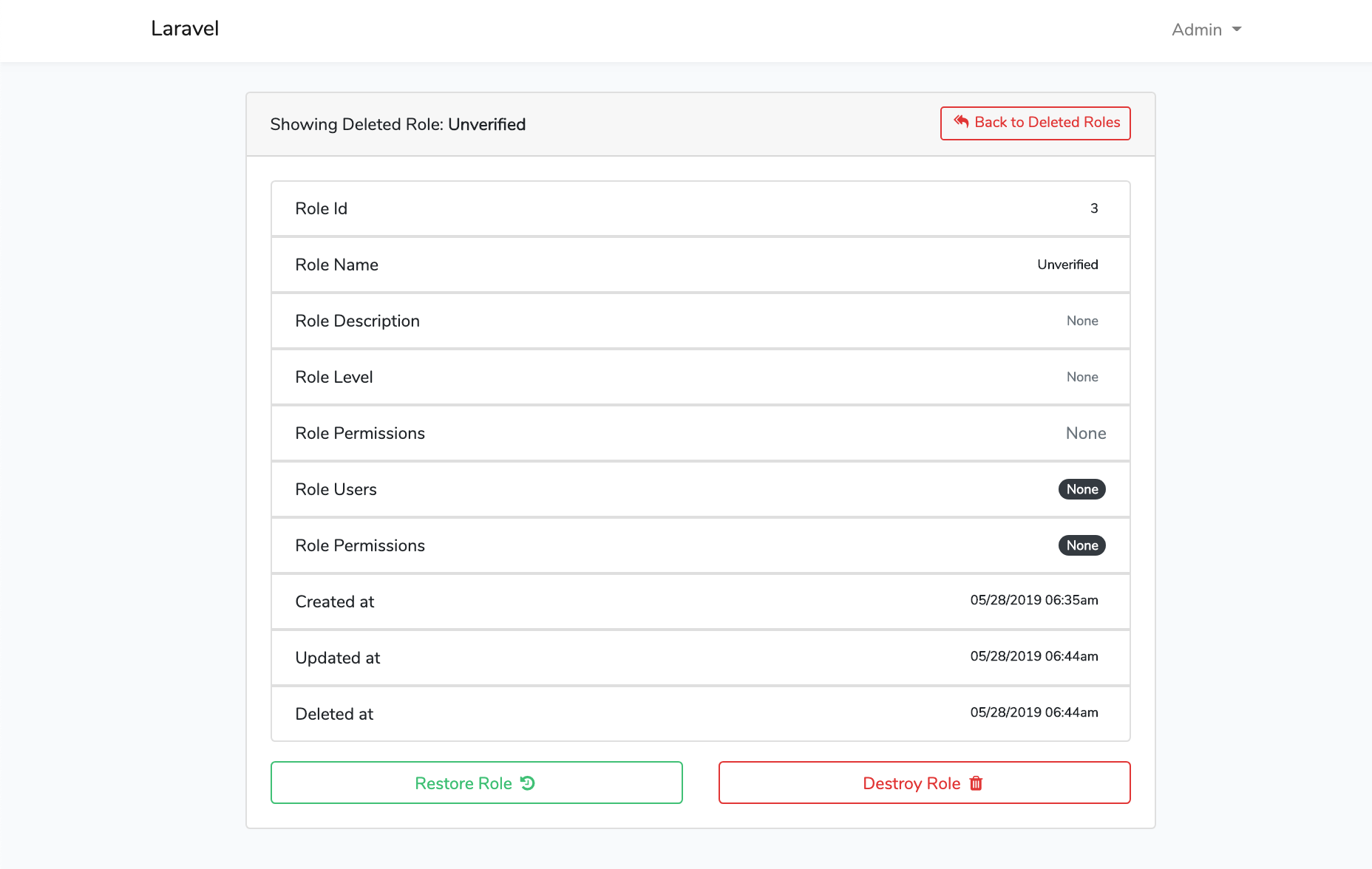
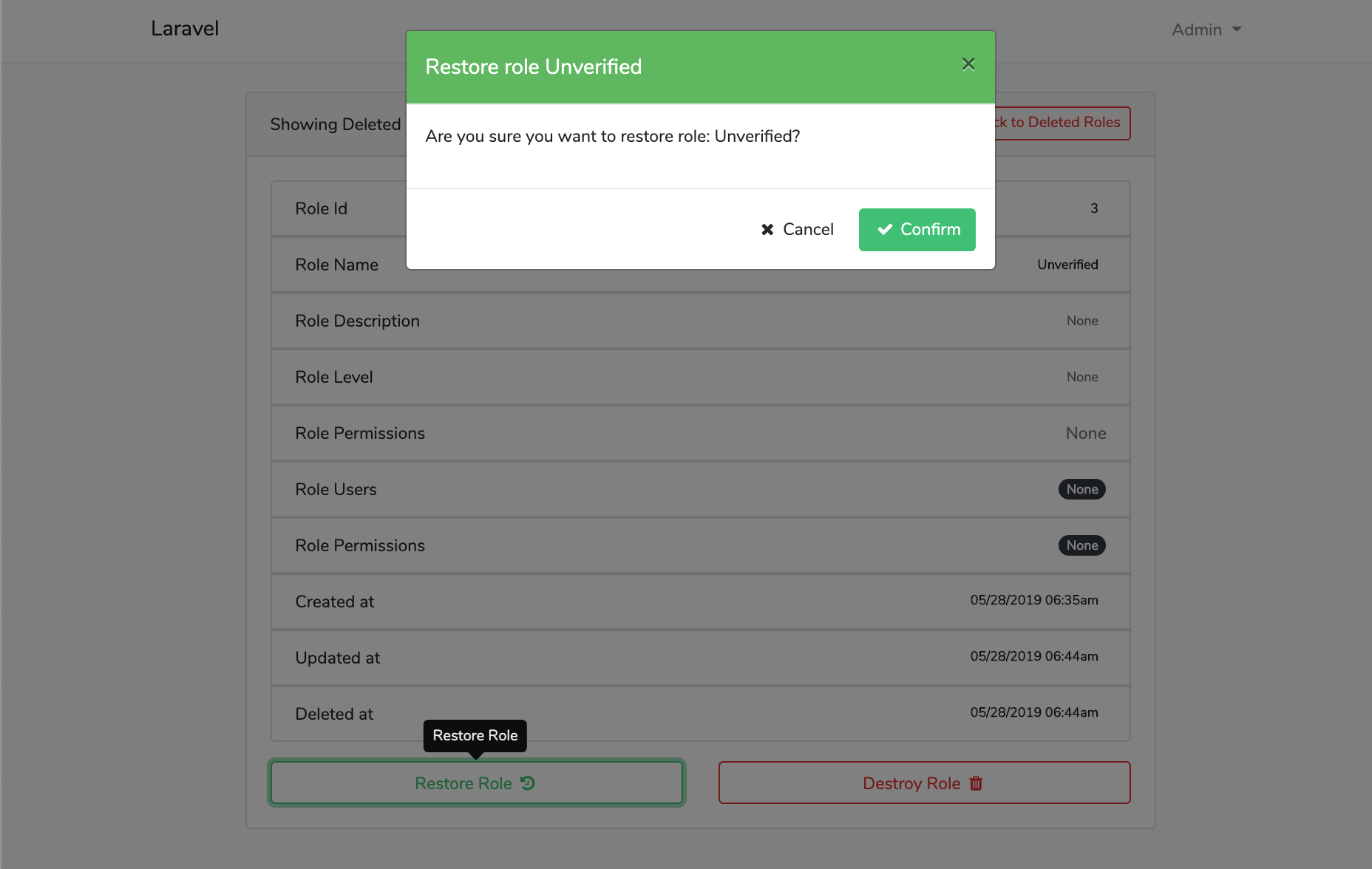
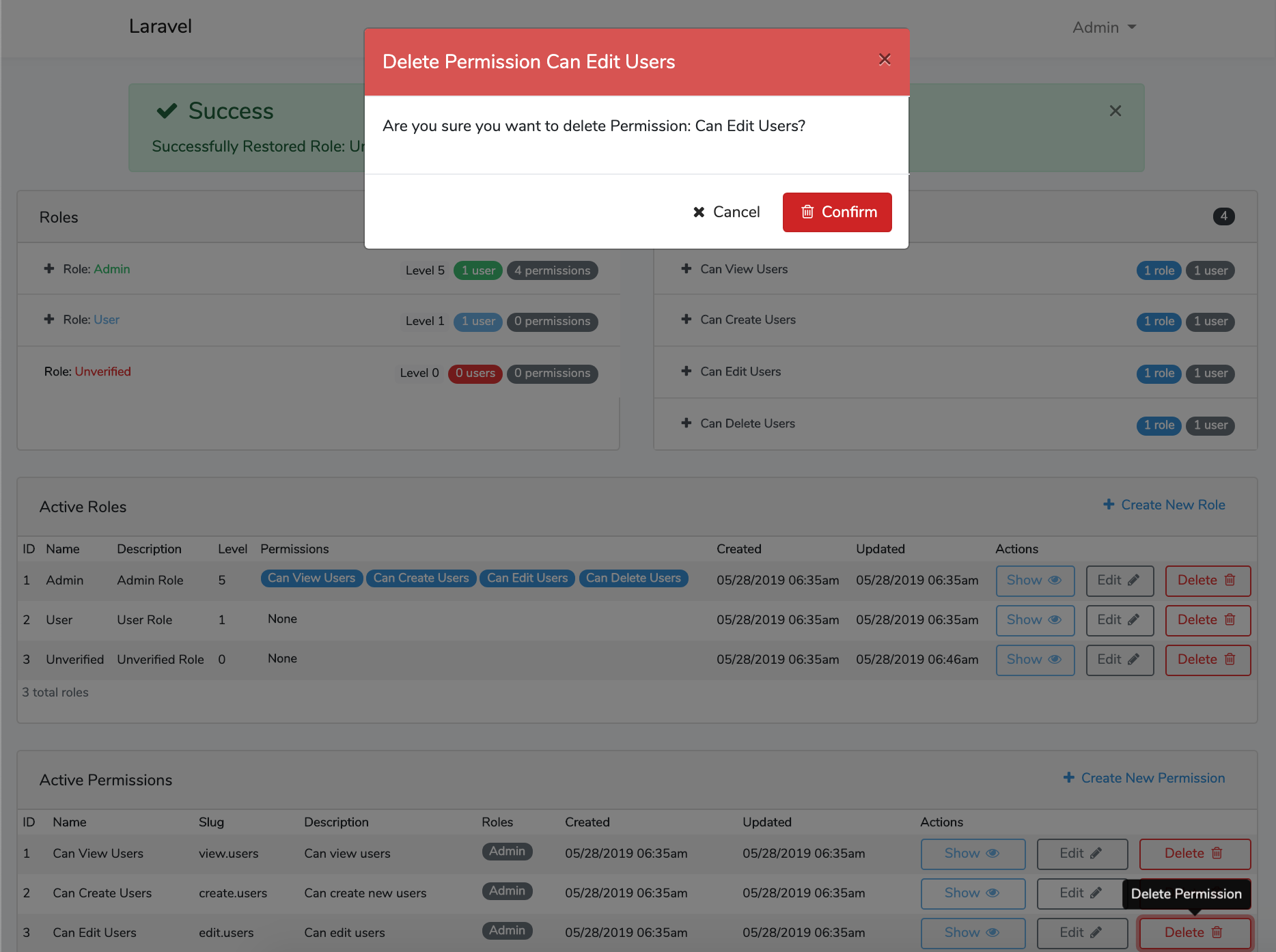
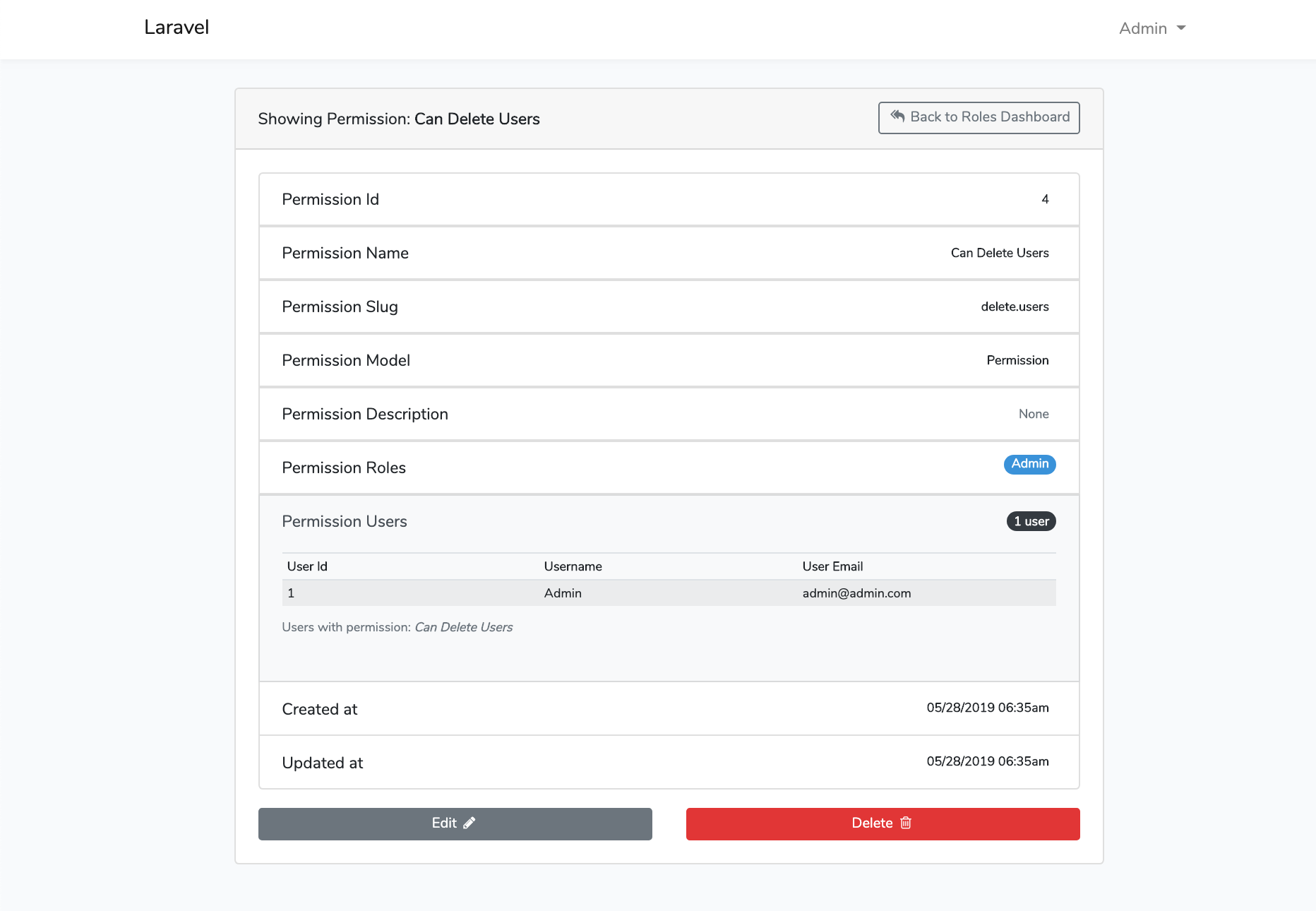
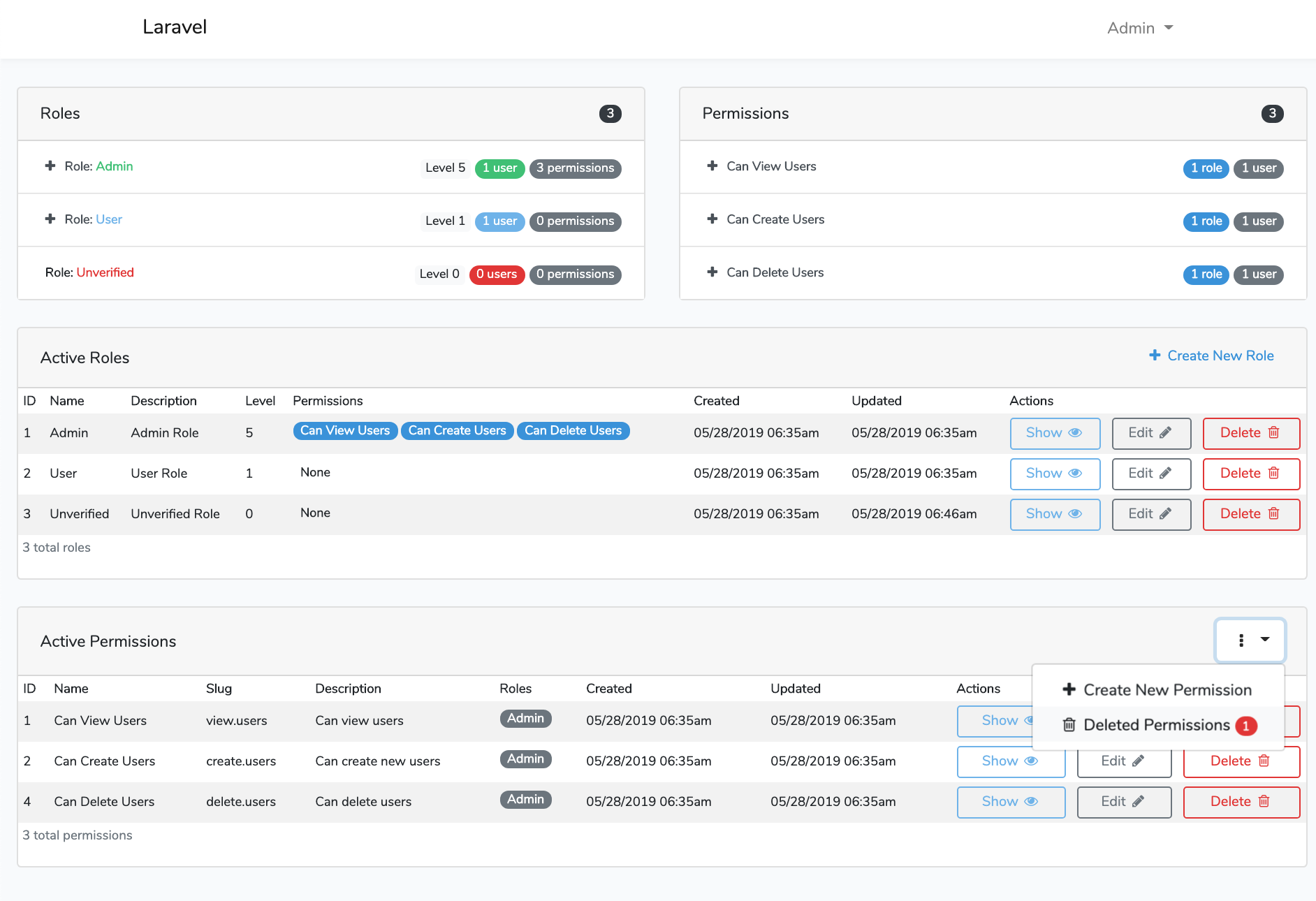
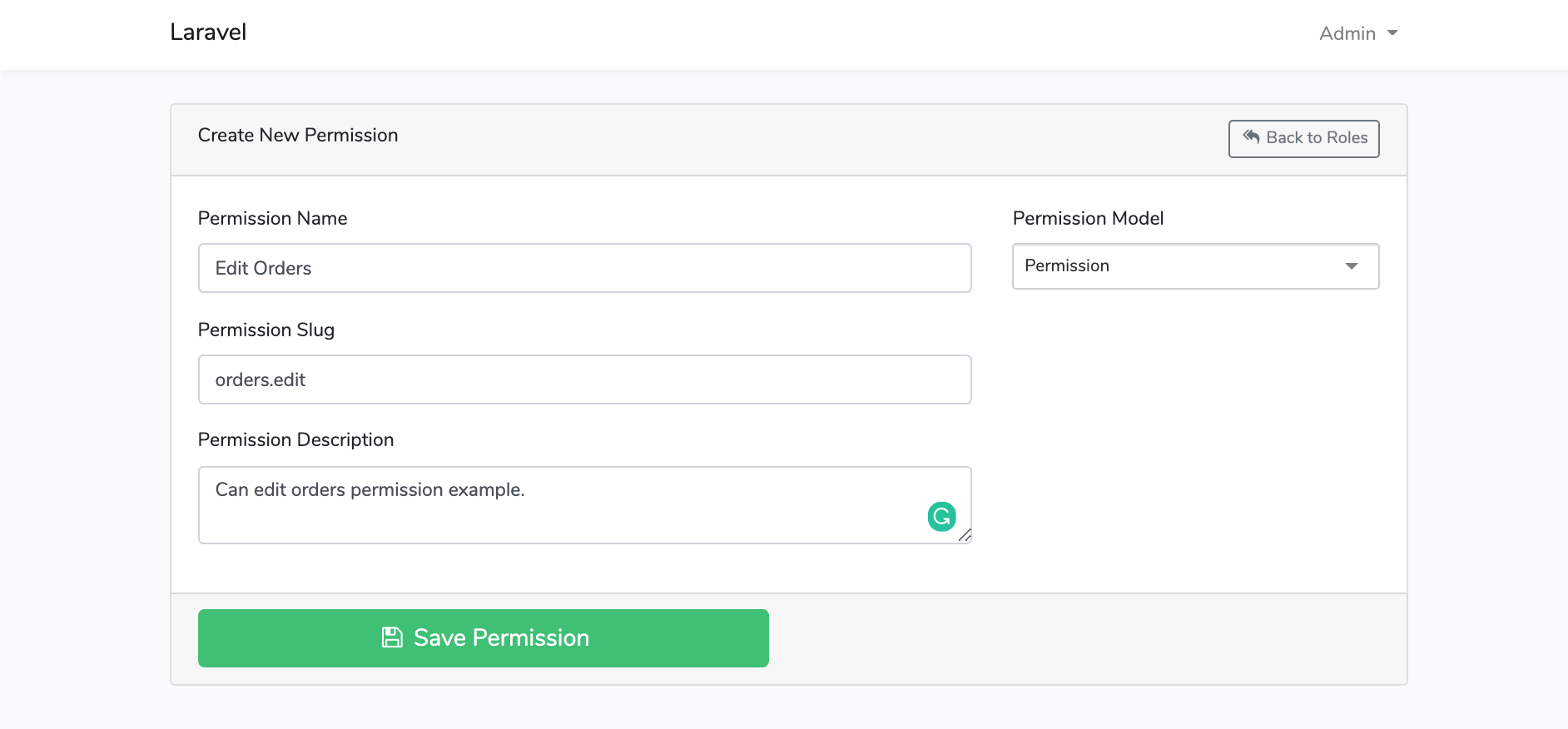
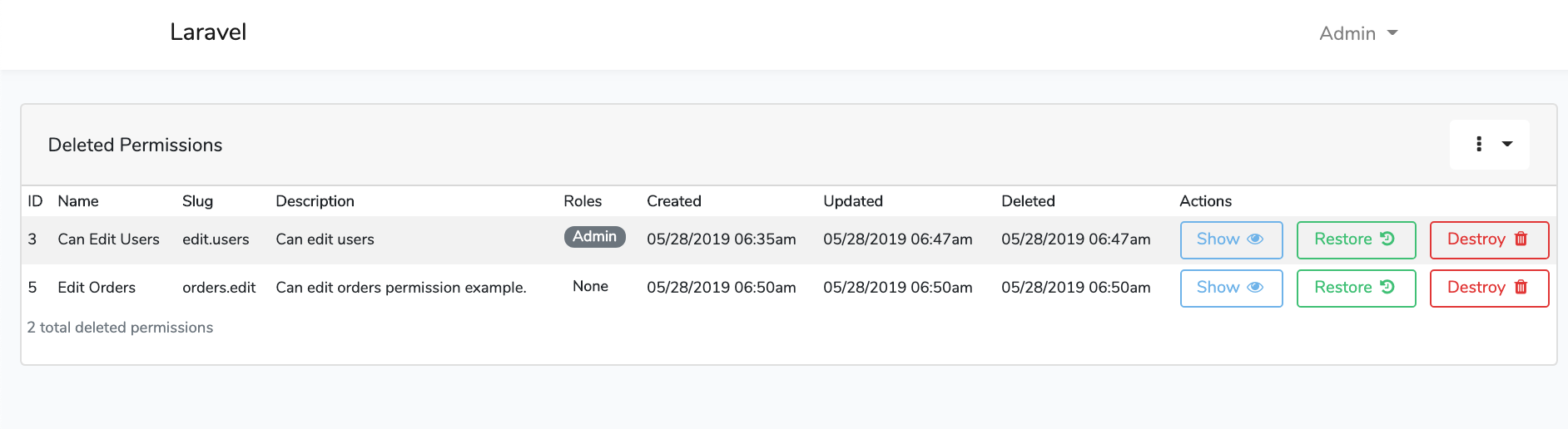
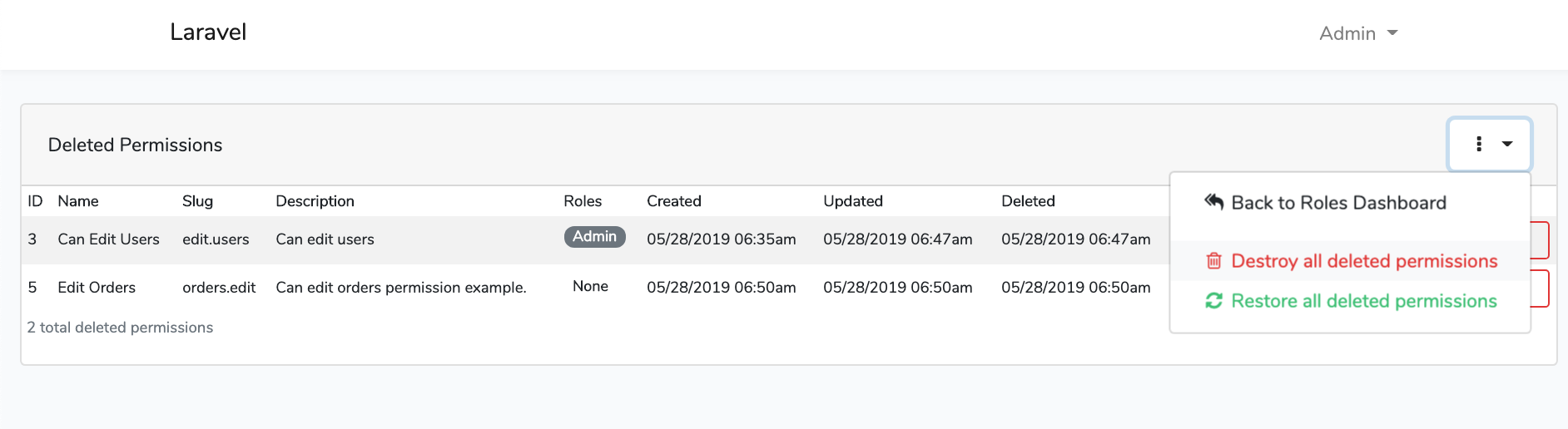
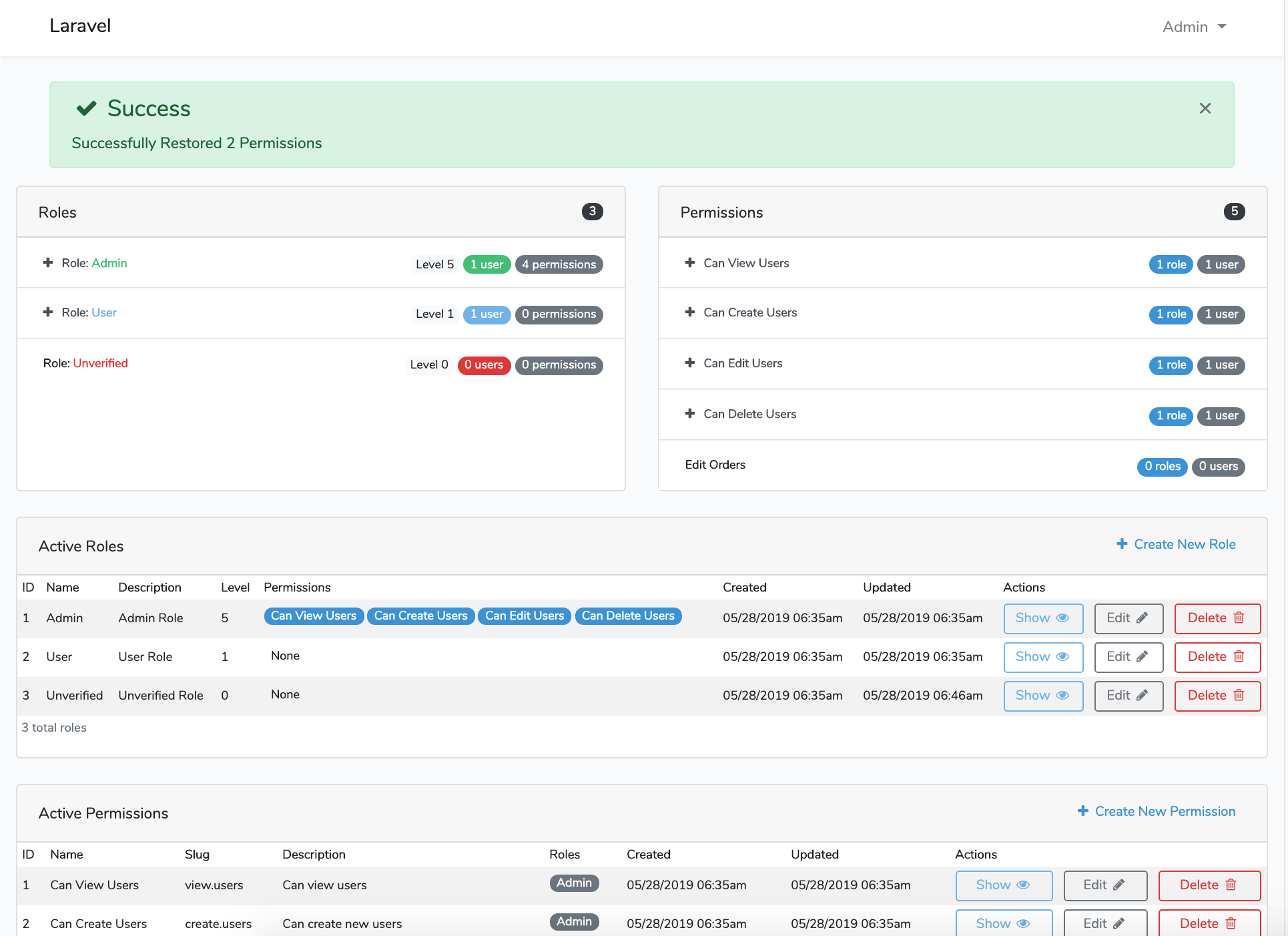
File Tree
âââ .env.example
âââ .env.travis
âââ .gitignore
âââ .travis.yml
âââ LICENSE
âââ composer.json
âââ phpunit.xml
âââ readme.md
âââ src
âââ App
â  âââ Exceptions
â  â  âââ AccessDeniedException.php
â  â  âââ LevelDeniedException.php
â  â  âââ PermissionDeniedException.php
â  â  âââ RoleDeniedException.php
â  âââ Http
â  â  âââ Controllers
â  â  â  âââ Api
â  â  â  â  âââ LaravelRolesApiController.php
â  â  â  âââ LaravelPermissionsController.php
â  â  â  âââ LaravelRolesController.php
â  â  â  âââ LaravelRolesDeletedController.php
â  â  â  âââ LaravelpermissionsDeletedController.php
â  â  âââ Middleware
â  â  â  âââ VerifyLevel.php
â  â  â  âââ VerifyPermission.php
â  â  â  âââ VerifyRole.php
â  â  âââ Requests
â  â  âââ StorePermissionRequest.php
â  â  âââ StoreRoleRequest.php
â  â  âââ UpdatePermissionRequest.php
â  â  âââ UpdateRoleRequest.php
â  âââ Services
â  âââ PermissionFormFields.php
â  âââ RoleFormFields.php
âââ Contracts
â  âââ HasRoleAndPermission.php
â  âââ PermissionHasRelations.php
â  âââ RoleHasRelations.php
âââ Models
â  âââ Permission.php
â  âââ Role.php
âââ RolesFacade.php
âââ RolesServiceProvider.php
âââ Traits
â  âââ DatabaseTraits.php
â  âââ HasRoleAndPermission.php
â  âââ PermissionHasRelations.php
â  âââ RoleHasRelations.php
â  âââ RolesAndPermissionsHelpersTrait.php
â  âââ RolesUsageAuthTrait.php
â  âââ Slugable.php
âââ config
â  âââ roles.php
âââ database
â  âââ Migrations
â  â  âââ 2016_01_15_105324_create_roles_table.php
â  â  âââ 2016_01_15_114412_create_role_user_table.php
â  â  âââ 2016_01_26_115212_create_permissions_table.php
â  â  âââ 2016_01_26_115523_create_permission_role_table.php
â  â  âââ 2016_02_09_132439_create_permission_user_table.php
â  âââ Seeds
â  âââ DefaultConnectRelationshipsSeeder.php
â  âââ DefaultPermissionsTableSeeder.php
â  âââ DefaultRolesTableSeeder.php
â  âââ DefaultUsersTableSeeder.php
â  âââ publish
â  âââ ConnectRelationshipsSeeder.php
â  âââ PermissionsTableSeeder.php
â  âââ RolesTableSeeder.php
â  âââ UsersTableSeeder.php
âââ resources
â  âââ lang
â  â  âââ en
â  â  âââ laravelroles.php
â  âââ views
â  âââ laravelroles
â  âââ cards
â  â  âââ permissions-card.blade.php
â  â  âââ roles-card.blade.php
â  âââ crud
â  â  âââ dashboard.blade.php
â  â  âââ permissions
â  â  â  âââ create.blade.php
â  â  â  âââ deleted
â  â  â  â  âââ index.blade.php
â  â  â  âââ edit.blade.php
â  â  â  âââ show.blade.php
â  â  âââ roles
â  â  âââ create.blade.php
â  â  âââ deleted
â  â  â  âââ index.blade.php
â  â  âââ edit.blade.php
â  â  âââ show.blade.php
â  âââ forms
â  â  âââ create-permission-form.blade.php
â  â  âââ create-role-form.blade.php
â  â  âââ delete-sm.blade.php
â  â  âââ destroy-all-permissions.blade.php
â  â  âââ destroy-all-roles.blade.php
â  â  âââ destroy-sm.blade.php
â  â  âââ edit-permission-form.blade.php
â  â  âââ edit-role-form.blade.php
â  â  âââ partials
â  â  â  âââ permission-desc-input.blade.php
â  â  â  âââ permission-name-input.blade.php
â  â  â  âââ permission-slug-input.blade.php
â  â  â  âââ permissions-model-select.blade.php
â  â  â  âââ role-desc-input.blade.php
â  â  â  âââ role-level-input.blade.php
â  â  â  âââ role-name-input.blade.php
â  â  â  âââ role-permissions-select.blade.php
â  â  â  âââ role-slug-input.blade.php
â  â  âââ permission-form.blade.php
â  â  âââ restore-all-permissions.blade.php
â  â  âââ restore-all-roles.blade.php
â  â  âââ restore-item.blade.php
â  â  âââ role-form.blade.php
â  âââ modals
â  â  âââ confirm-modal.blade.php
â  âââ partials
â  â  âââ bs-visibility-css.blade.php
â  â  âââ flash-messages.blade.php
â  â  âââ form-status.blade.php
â  â  âââ styles.blade.php
â  âââ scripts
â  â  âââ confirm-modal.blade.php
â  â  âââ datatables.blade.php
â  â  âââ form-inputs-helpers.blade.php
â  â  âââ selectize.blade.php
â  â  âââ selectizePermission.blade.php
â  â  âââ tooltips.blade.php
â  âââ tables
â  âââ permission-items-table.blade.php
â  âââ permissions-table.blade.php
â  âââ role-items-table.blade.php
â  âââ roles-table.blade.php
âââ routes
âââ api.php
âââ web.php
- Tree command can be installed using brew:
brew install tree - File tree generated using command
tree -a -I '.git|node_modules|vendor|storage|tests'
Opening an Issue
Before opening an issue there are a couple of considerations:
- You are all awesome!
- Read the instructions and make sure all steps were followed correctly.
- Check that the issue is not specific to your development environment setup.
- Provide duplication steps.
- Attempt to look into the issue, and if you have a solution, make a pull request.
- Show that you have made an attempt to look into the issue.
- Check to see if the issue you are reporting is a duplicate of a previous reported issue.
- Following these instructions show me that you have tried.
- If you have a questions send me an email to jeremykenedy@gmail.com
- Need some help, I can do my best on Slack: https://opensourcehelpgroup.slack.com
- Please be considerate that this is an open source project that I provide to the community for FREE when opening an issue.
Credit Note:
The HasRoleAndPermission Trait And Contract is and an adaptation of romanbican/roles. I liked the method he made so I used them.
License
This package is free software distributed under the terms of the MIT license. Enjoy!
Top Related Projects
Associate users with roles and permissions
Role-based Permissions for Laravel 5
Handle roles and permissions in your Laravel application
A framework agnostic authentication & authorization system.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot

