 evilginx2
evilginx2
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Top Related Projects
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Framework for Man-In-The-Middle attacks
An interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
The Swiss Army knife for 802.11, BLE, HID, CAN-bus, IPv4 and IPv6 networks reconnaissance and MITM attacks.
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
Incredibly fast crawler designed for OSINT.
Quick Overview
Evilginx2 is a man-in-the-middle attack framework used for setting up phishing pages and capturing credentials. It is designed to be a powerful tool for penetration testers and security researchers to assess the security of web applications and user authentication mechanisms.
Pros
- Highly customizable phishing pages that can mimic popular web services
- Supports a wide range of web services, including Google, Facebook, Twitter, and more
- Provides detailed logs of captured credentials and other user information
- Actively maintained and regularly updated with new features and bug fixes
Cons
- Requires a good understanding of networking and web application security to use effectively
- Can be used for malicious purposes, which raises ethical concerns
- May be detected by some security solutions, limiting its effectiveness in certain scenarios
- Requires a dedicated server or virtual machine to run the framework
Getting Started
To get started with Evilginx2, follow these steps:
- Clone the repository:
git clone https://github.com/kgretzky/evilginx2.git
- Change to the project directory:
cd evilginx2
- Install the required dependencies:
sudo apt-get install golang git make
- Build the Evilginx2 binary:
make
- Run the Evilginx2 server:
sudo ./evilginx
- Follow the on-screen instructions to set up a new phishing campaign.
For more detailed instructions and configuration options, please refer to the project's README file.
Competitor Comparisons
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Pros of Social-Engineer-Toolkit
- Broader range of attack vectors and tools
- More extensive documentation and community support
- Regularly updated with new features and improvements
Cons of Social-Engineer-Toolkit
- Steeper learning curve due to its extensive feature set
- Less focused on specific phishing techniques compared to Evilginx2
- May require more setup and configuration for certain attacks
Code Comparison
Social-Engineer-Toolkit:
# Example of a phishing attack setup
choice = raw_input(setprompt(["1"], "SET vector (website)"))
if choice == "1":
web_server = True
# Start web server and clone the target site
clone_site(website)
Evilginx2:
// Example of a phishing proxy setup
func (p *Phishlet) AddSubFilter(hostname, subdomain, domain, mime, regexp, replace string) error {
sf := SubFilter{
Hostname: hostname,
Subdomain: subdomain,
Domain: domain,
Mime: mime,
Regexp: regexp,
Replace: replace,
}
p.subfilters = append(p.subfilters, sf)
return nil
}
Framework for Man-In-The-Middle attacks
Pros of MITMf
- More versatile with a wider range of attack modules and plugins
- Supports multiple protocols beyond just HTTP/HTTPS
- Offers more customization options for advanced users
Cons of MITMf
- Less focused on phishing specifically, which may reduce effectiveness for that use case
- Requires more setup and configuration compared to Evilginx2's streamlined approach
- Less actively maintained, with the last update being several years ago
Code Comparison
MITMf (Python):
from core.sslstrip.DnsCache import DnsCache
from core.sslstrip.URLMonitor import URLMonitor
dnscache = DnsCache()
urlMonitor = URLMonitor(dnscache)
Evilginx2 (Go):
type Phishlet struct {
Name string
Author string
ProxyHosts []string
LandingURL string
RedirectURL string
}
Both projects aim to facilitate man-in-the-middle attacks, but their implementations and focus areas differ. MITMf provides a broader toolkit for various attack scenarios, while Evilginx2 specializes in advanced phishing campaigns with a more modern and streamlined approach.
An interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
Pros of mitmproxy
- More versatile and can be used for a wider range of network analysis tasks
- Offers a command-line interface, web interface, and Python API for greater flexibility
- Actively maintained with regular updates and a larger community
Cons of mitmproxy
- Requires more technical knowledge to set up and use effectively
- Less focused on phishing attacks, which is the primary purpose of evilginx2
- May require additional configuration for specific use cases
Code Comparison
mitmproxy:
from mitmproxy import http
def request(flow: http.HTTPFlow) -> None:
if flow.request.pretty_url.startswith("https://example.com"):
flow.request.headers["Custom-Header"] = "Modified"
evilginx2:
func (p *Phishlet) handleRequest(req *http.Request) {
if strings.HasPrefix(req.URL.Host, "example.com") {
req.Header.Set("Custom-Header", "Modified")
}
}
Both examples show how to modify headers for specific requests, but mitmproxy uses Python and offers a more straightforward API, while evilginx2 uses Go and is more focused on phishing-specific functionality.
The Swiss Army knife for 802.11, BLE, HID, CAN-bus, IPv4 and IPv6 networks reconnaissance and MITM attacks.
Pros of Bettercap
- More versatile, supporting a wide range of network attacks and monitoring capabilities
- Active development with frequent updates and community contributions
- Extensive documentation and user-friendly CLI interface
Cons of Bettercap
- Steeper learning curve due to its broader feature set
- May require more setup and configuration for specific attack scenarios
- Less focused on phishing attacks compared to Evilginx2
Code Comparison
Bettercap (JavaScript module):
var targets = []
var start = function() {
// ... (code to start the attack)
}
Evilginx2 (Go module):
type Phishlet struct {
Name string
Author string
ProxyHosts []string
// ... (other struct fields)
}
Both projects use different programming languages and architectures. Bettercap is more modular and extensible, while Evilginx2 is more focused on phishing attacks with a streamlined structure.
Bettercap offers a broader range of network security tools, making it suitable for various penetration testing scenarios. Evilginx2, on the other hand, specializes in advanced phishing techniques, providing a more targeted approach for social engineering assessments.
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
Pros of Responder
- Simpler setup and usage, making it more accessible for beginners
- Broader attack surface, targeting multiple protocols and services
- Active development with frequent updates and community contributions
Cons of Responder
- Less stealthy, potentially easier to detect by security systems
- Limited to local network attacks, unlike Evilginx2's remote phishing capabilities
- Requires more manual intervention for credential harvesting
Code Comparison
Responder (Python):
def start():
try:
server = ThreadingUDPServer(('', 137), NBTNSResponder)
server.serve_forever()
except:
print("[!] Error starting NBT-NS responder")
Evilginx2 (Go):
func (p *Phishlet) GetLureURL(path string) (string, error) {
b64 := base64.URLEncoding.EncodeToString([]byte(path))
return fmt.Sprintf("%s?%s=%s", p.cfg.BaseURL, p.cfg.ParamName, b64), nil
}
The code snippets demonstrate the different approaches: Responder focuses on network protocol manipulation, while Evilginx2 emphasizes URL manipulation for phishing attacks.
Incredibly fast crawler designed for OSINT.
Pros of Photon
- Focused on web reconnaissance and information gathering
- Lightweight and easy to use for quick scans
- Supports multiple output formats for flexibility
Cons of Photon
- Limited to passive information gathering
- Less sophisticated in terms of attack capabilities
- May require additional tools for comprehensive security testing
Code Comparison
Photon (Python):
def photon(url, level, threads, delay, timeout, cook, headers):
colors.info('Photon Internet Crawler')
colors.info('Crawling the target')
# ... (crawling logic)
Evilginx2 (Go):
func (p *Phishlet) GetLureUrls() []string {
var ret []string
for _, l := range p.lures {
ret = append(ret, l.GetUrl())
}
return ret
}
Photon is primarily designed for web crawling and information gathering, making it more suitable for reconnaissance tasks. It's written in Python, which can be easier for beginners to understand and modify.
Evilginx2, on the other hand, is a more advanced tool focused on creating and managing phishing campaigns. It's written in Go, which offers better performance but may have a steeper learning curve.
While both tools can be used for security testing, they serve different purposes and have distinct strengths. Photon excels in passive information gathering, while Evilginx2 is more suited for active phishing simulations and advanced security assessments.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

Evilginx 3.0
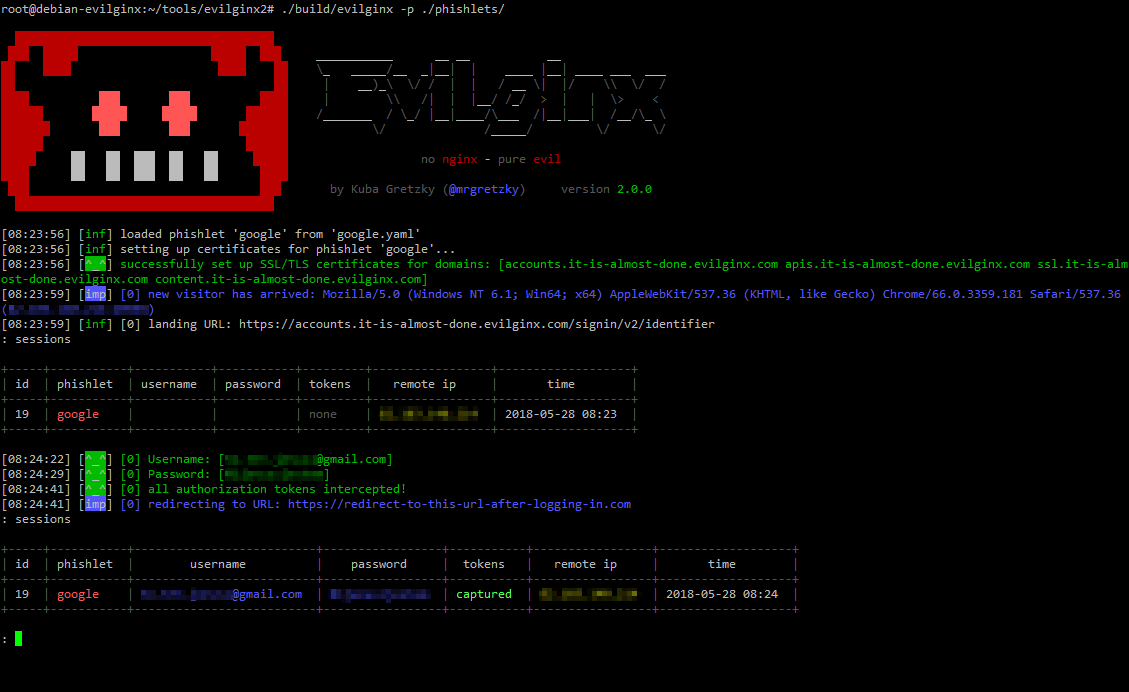
Evilginx is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
This tool is a successor to Evilginx, released in 2017, which used a custom version of nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use.
Disclaimer
I am very much aware that Evilginx can be used for nefarious purposes. This work is merely a demonstration of what adept attackers can do. It is the defender's responsibility to take such attacks into consideration and find ways to protect their users against this type of phishing attacks. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties.
Evilginx Pro is now available!
This is it! After over two years of development, countless delays, and hundreds of manual company verifications, concluded with multiple hurdles related to export regulations, Evilginx Pro is finally live!
Evilginx Pro is the fruit of a passion I've had for a long time in developing offensive security tools for cybersecurity enthusiasts. The journey has just begun, and now that the product is officially released, I can focus on making it even better by implementing all the ideas I've planned for it.
Key features:
- Out-of-the-box phishing detection evasion (including Chrome's Enchanced Browser Protection)
- Tested and maintained official phishlets database
- Botguard to prevent bot traffic by default (same concept as Cloudflare Turnstile)
- Evilpuppet for advanced phishing capability (Google)
- External DNS providers with multi-domain support
- Website spoofing for unauthorized requests
- JavaScript & HTML obfuscation
- Wildcard TLS certificates
- Automated server deployment
- SQLite database support
Find out more on the official release blog post.
Evilginx Mastery Training Course
If you want everything about reverse proxy phishing with Evilginx - check out my Evilginx Mastery course!
Learn everything about the latest methods of phishing, using reverse proxying to bypass Multi-Factor Authentication. Learn to think like an attacker, during your red team engagements, and become the master of phishing with Evilginx.
Grab it here: https://academy.breakdev.org/evilginx-mastery
Official Gophish integration
If you'd like to use Gophish to send out phishing links compatible with Evilginx, please use the official Gophish integration with Evilginx 3.3. You can find the custom version here in the forked repository: Gophish with Evilginx integration
If you want to learn more about how to set it up, please follow the instructions in this blog post
Write-ups
If you want to learn more about reverse proxy phishing, I've published extensive blog posts about Evilginx here:
Evilginx 2.2 - Jolly Winter Update
Evilginx 2.3 - Phisherman's Dream
Help
In case you want to learn how to install and use Evilginx, please refer to online documentation available at:
Support
I DO NOT offer support for providing or creating phishlets. I will also NOT help you with creation of your own phishlets. Please look for ready-to-use phishlets, provided by other people.
License
evilginx2 is made by Kuba Gretzky (@mrgretzky) and it's released under BSD-3 license.
Top Related Projects
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Framework for Man-In-The-Middle attacks
An interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
The Swiss Army knife for 802.11, BLE, HID, CAN-bus, IPv4 and IPv6 networks reconnaissance and MITM attacks.
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
Incredibly fast crawler designed for OSINT.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot
