 CredMaster
CredMaster
Refactored & improved CredKing password spraying tool, uses FireProx APIs to rotate IP addresses, stay anonymous, and beat throttling
Top Related Projects
Scripts to make password spraying attacks against Lync/S4B, OWA & O365 a lot quicker, less painful and more efficient
A collection of scripts for assessing Microsoft Azure security
AWS API Gateway management tool for creating on the fly HTTP pass-through proxies for unique IP rotation
Quick Overview
CredMaster is a Python-based tool designed to automate the process of credential management and rotation for various cloud platforms, including AWS, Azure, and Google Cloud. It provides a centralized and secure way to manage credentials, ensuring that they are regularly rotated and updated to enhance security.
Pros
- Automated Credential Rotation: CredMaster automates the process of credential rotation, reducing the risk of credential exposure and ensuring that credentials are regularly updated.
- Multi-Cloud Support: The tool supports multiple cloud platforms, allowing users to manage credentials across different cloud environments from a single interface.
- Centralized Credential Management: CredMaster provides a centralized platform for managing credentials, making it easier to track and control access to sensitive information.
- Secure Storage: Credentials are stored securely using encryption, ensuring that sensitive information is protected from unauthorized access.
Cons
- Limited Platform Support: While CredMaster supports several major cloud platforms, it may not cover all the cloud services and platforms that organizations use.
- Complexity: Configuring and setting up CredMaster may require some technical expertise, which could be a barrier for some users.
- Dependency on External Services: CredMaster relies on external services, such as AWS Secrets Manager or Azure Key Vault, for secure credential storage, which could introduce additional complexity and potential points of failure.
- Potential Performance Issues: Depending on the scale of the credential management requirements, CredMaster's performance may be affected, especially when dealing with a large number of credentials or frequent rotations.
Code Examples
from credmaster.aws import AWSCredentialManager
from credmaster.azure import AzureCredentialManager
from credmaster.gcp import GCPCredentialManager
# AWS Credential Management
aws_manager = AWSCredentialManager(
aws_access_key_id="your_aws_access_key_id",
aws_secret_access_key="your_aws_secret_access_key",
aws_region="us-east-1"
)
aws_manager.rotate_credentials()
# Azure Credential Management
azure_manager = AzureCredentialManager(
azure_tenant_id="your_azure_tenant_id",
azure_client_id="your_azure_client_id",
azure_client_secret="your_azure_client_secret"
)
azure_manager.rotate_credentials()
# GCP Credential Management
gcp_manager = GCPCredentialManager(
gcp_project_id="your_gcp_project_id",
gcp_service_account_key_file="path/to/gcp/service/account/key.json"
)
gcp_manager.rotate_credentials()
These code examples demonstrate how to use the CredMaster library to manage credentials for different cloud platforms, including AWS, Azure, and Google Cloud Platform (GCP). The examples show how to initialize the credential managers for each platform and how to rotate the credentials using the rotate_credentials() method.
Getting Started
To get started with CredMaster, follow these steps:
-
Install the CredMaster library using pip:
pip install credmaster -
Configure the necessary credentials for the cloud platforms you want to manage. This includes setting up the required environment variables or providing the necessary API keys and secrets.
-
Import the relevant credential manager classes from the CredMaster library:
from credmaster.aws import AWSCredentialManager from credmaster.azure import AzureCredentialManager from credmaster.gcp import GCPCredentialManager -
Initialize the credential manager for the cloud platform you want to use, providing the necessary configuration parameters:
aws_manager = AWSCredentialManager( aws_access_key_id="your_aws_access_key_id", aws_secret_access_key="your_aws_secret_access_key", aws_region="us-east-1" ) -
Call the
rotate_credentials()method to initiate the credential rotation process:aws_manager.rotate_credentials() -
Repeat steps 3-5 for each cloud platform you want to manage using CredMaster.
Competitor Comparisons
Scripts to make password spraying attacks against Lync/S4B, OWA & O365 a lot quicker, less painful and more efficient
Pros of SprayingToolkit
- Supports multiple protocols and services (OWA, O365, Lync, etc.)
- Includes tools for both password spraying and user enumeration
- Offers a modular architecture for easy extension
Cons of SprayingToolkit
- Less focus on evasion techniques compared to CredMaster
- May require more manual configuration for complex scenarios
- Limited built-in reporting and result analysis features
Code Comparison
SprayingToolkit:
def spray(self, username, password):
try:
self.auth.login(username, password)
return True
except AuthenticationException:
return False
CredMaster:
def spray(self, username, password):
try:
result = self.auth_module.authenticate(username, password)
self.evasion.apply_delay()
return result
except Exception as e:
self.logger.error(f"Authentication error: {str(e)}")
return False
The code comparison shows that CredMaster includes built-in evasion techniques and more robust error handling, while SprayingToolkit focuses on a simpler authentication process. CredMaster's approach may be more suitable for scenarios where evading detection is crucial, while SprayingToolkit's simplicity could be advantageous for straightforward testing environments.
A collection of scripts for assessing Microsoft Azure security
Pros of MicroBurst
- Broader focus on Azure security, including enumeration and exploitation tools
- More comprehensive set of PowerShell modules for various Azure-related tasks
- Active development with regular updates and contributions
Cons of MicroBurst
- Primarily focused on PowerShell, which may limit its use in certain environments
- Requires more setup and configuration compared to CredMaster's streamlined approach
- Less specialized in credential spraying, offering a more general-purpose toolkit
Code Comparison
MicroBurst (PowerShell):
$Users = Get-Content .\users.txt
$Passwords = Get-Content .\passwords.txt
foreach ($Password in $Passwords) {
foreach ($User in $Users) {
Try-AzureLogin -Username $User -Password $Password
}
}
CredMaster (Python):
for password in passwords:
for username in usernames:
spray_result = spray_account(username, password)
if spray_result:
print(f"Valid credentials: {username}:{password}")
Both tools provide functionality for credential spraying, but CredMaster is more focused on this specific task, while MicroBurst offers a wider range of Azure-related security tools. CredMaster's Python-based approach may be more accessible for some users, while MicroBurst's PowerShell modules integrate well with existing Windows environments and Azure management tasks.
AWS API Gateway management tool for creating on the fly HTTP pass-through proxies for unique IP rotation
Pros of FireProx
- Simpler setup and usage, focusing specifically on AWS API Gateway for proxying
- Provides a command-line interface for easy management of proxy instances
- Designed for quick deployment and teardown of proxies
Cons of FireProx
- Limited to AWS API Gateway, while CredMaster supports multiple proxy types
- Lacks built-in password spraying functionality
- Does not include features for handling various authentication types
Code Comparison
FireProx:
def create_api(self, name):
response = self.client.create_rest_api(
name=name,
description='FireProx API',
endpointConfiguration={'types': ['REGIONAL']}
)
return response['id']
CredMaster:
def create_proxy(self):
if self.proxy_type == "digitalocean":
return self.create_do_proxy()
elif self.proxy_type == "aws":
return self.create_aws_proxy()
elif self.proxy_type == "azure":
return self.create_azure_proxy()
The code snippets highlight the different approaches:
- FireProx focuses on creating AWS API Gateway instances
- CredMaster supports multiple proxy types with a more modular design
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
CredMaster
Launch a password spray / brute force attach via Amazon AWS passthrough proxies, shifting the requesting IP address for every authentication attempt. This dynamically creates FireProx APIs for more evasive password sprays.
Shoutout to @ustayready for his CredKing and FireProx tools, which form the base of this suite.
See all the full notes on the Wiki, tool released with specifics in this blogpost
For detection tips, see the blogpost and detection section.
Be careful for account lockouts, know the reset policies of your target
TL;DR
- git clone the repo down
- If unsure how to create correct keys see this blog.
pip install -r requirements.txt- Fill out the config file (wiki) with desired options, or provide through CLI
Benefits & Features
- Rotates the requesting IP address for every request
- Automatically generates APIs for proxy passthru
- Spoofs API tracking numbers, forwarded-for IPs, and other proxy tracking headers = fully anonymous
- Easily configuation via config file
- Multi-threaded processing
- Password delay counters & configuration for lockout policy evasion
- Easily add new plugins
- Colourised output
- Notification systems for Keybase, Slack, Discord, Teams & Pushover
- WeekdayWarrior setting for timed spraying and SOC evasion
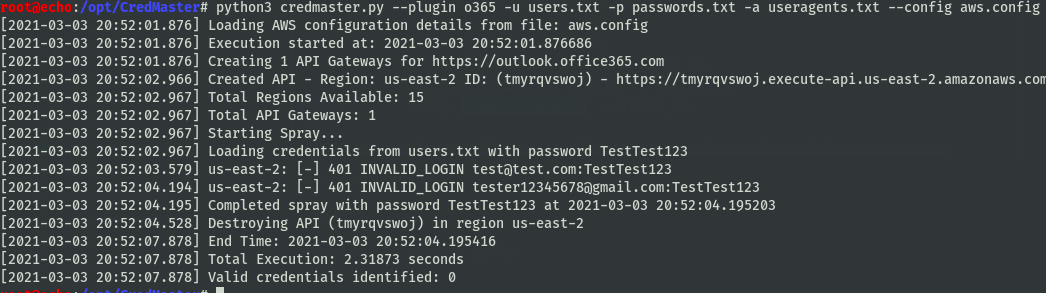
Quick Use
The following plugins are currently supported:
- OWA - Outlook Web Access
--plugin owa
- EWS - Exchange Web Services
--plugin ews
- O365 - Office365 - DEPRECATED
plugin removed
- ADFS - Active Directory Federation Services
--plugin adfs
- O365Enum - Office365 User Enum (No Authentication Request)
--plugin o365enum
- MSOL - Microsoft Online
--plugin msol
- MSGraph - MSGraph Module, msgraph spray point for azure and MSOL credentials
--plugin msgraph
- AzureSSO - Azure AD Seamless SSO Endpoint
--plugin azuresso
- AzVault - AzVault Module, Azure spray point different to MSOL/AzureSSO
--plugin azvault
- Okta - Okta Authentication Portal
--plugin okta
- FortinetVPN - Fortinet VPN Client
--plugin fortinetvpn
- HTTPBrute - Generic HTTP Brute Methods (Basic/Digest/NTLM)
--plugin httpbrute
- GMailEnum - GSuite/Gmail enumeration
--plugin gmailenum
- PingFed - Ping Federated Authentication
--plugin pingfed
- HTTPPost - Generic HTTP POST with custom body and headers
--plugin httppost
Example Use:
python3 credmaster.py --plugin {pluginname} --access_key {key} --secret_access_key {key} -u userfile -p passwordfile -a useragentfile {otherargs}
or
python3 credmaster.py --config config.json
This tool requires AWS API access keys, a walkthrough on how to acquire these keys can be found here: https://bond-o.medium.com/aws-pass-through-proxy-84f1f7fa4b4b
All other usage details can be found on the wiki
TODO
PRs welcome :)
- New Plugin: Optiv's Go365 Method - Includes Office365 auth and userenum capabilities via SOAP
- "Resume" functionality for paused/cancelled scans. Ideally storing data for APIs used, if they were destroyed and what user/pwd the spray was on
- Method to reliably determine if an auth attempt was throttled, so the username could be re-queued and tried again later for full cover (would have to be per-plugin, return "throttled" boolean value in plugin script, requeue if throttled)
- Notification system for webhooks (Teams TODO)
- Stop on success flag
- Spray profile overhaul
- Development notes
- Spray username==password
Credits
- Mike Felch (ustayready) - CredKing & FireProx
- Beau Bullock (dafthack) - MSOLSpray tool
- Martin Ingesen (mrtn9) - MSOLSpray Python tool
- Oliver Morton (grimhacker) - Office365UserEnum tool
- Marcello (byt3bl33d3r) - SprayingToolkit
- Erforschr - HTTP Bruteforce tool
- Florian Hauser (frycos from codewhitesec) - ADFS plugin
- nyxgeek - Azure AD Seamless SSO python implementation
- Joe Helle (joehelle) - Oh365UserFinder
- Cameron Geehr (BarrelTit0r) - o365enum tool
- Max Gruenberg (Max_Gruenberg) - o365enum plugin
- x0rz - GmailEnum technique
- Kole Swesey (0xPanic_) - Assorted PR
- Logan (TheToddLuci0) - Assorted bug squashing, AWS authing, and Keybase notifying
- Andy Gill (ZephrFish) - Colour functions + Tweaks/Notifications, helping on dev rewrite, AzVault module
- Hugo VINCENT (@hugow) - Batch size / delay
- Dennis Herrmann (dhn_ from CODE WHITE GmbH) - Ntfy notifying support
- Jason Juntunen (missing0x00) - PingFed plugin
- Gustavo Penna (moreirapenna2) - HTTP POST plugin
Feel free to drop me a line
- @knave on Keybase
- Twitter - knavesec
Top Related Projects
Scripts to make password spraying attacks against Lync/S4B, OWA & O365 a lot quicker, less painful and more efficient
A collection of scripts for assessing Microsoft Azure security
AWS API Gateway management tool for creating on the fly HTTP pass-through proxies for unique IP rotation
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot