Top Related Projects
Set up a personal VPN in the cloud
Streisand sets up a new server running your choice of WireGuard, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, or a Tor bridge. It also generates custom instructions for all of these services. At the end of the run you are given an HTML file with instructions that can be shared with friends, family members, and fellow activists.
OpenVPN road warrior installer for Ubuntu, Debian, AlmaLinux, Rocky Linux, CentOS and Fedora
The Simplest VPN installer, designed for Raspberry Pi
Scripts to build your own IPsec VPN server, with IPsec/L2TP, Cisco IPsec and IKEv2
Quick Overview
Subspace is a self-hosted VPN server and client management platform. It provides a simple web UI for managing WireGuard VPN connections and users, making it easier to set up and maintain a private VPN infrastructure.
Pros
- User-friendly web interface for managing WireGuard VPN connections
- Easy setup and deployment using Docker
- Supports multi-user environments with access control
- Automatic key rotation and configuration management
Cons
- Limited to WireGuard protocol only
- Requires self-hosting, which may be challenging for some users
- Documentation could be more comprehensive
- May require additional setup for advanced networking scenarios
Getting Started
- Install Docker and Docker Compose on your server
- Clone the Subspace repository:
git clone https://github.com/subspacecloud/subspace.git - Navigate to the Subspace directory:
cd subspace - Create a
.envfile with the following content:SUBSPACE_HTTP_HOST=vpn.example.com SUBSPACE_LETSENCRYPT_EMAIL=your@email.com - Start Subspace:
docker-compose up -d - Access the web UI at
https://vpn.example.comand follow the setup wizard
Note: Replace vpn.example.com with your actual domain and your@email.com with your email address for Let's Encrypt SSL certificates.
Competitor Comparisons
Set up a personal VPN in the cloud
Pros of algo
- More comprehensive security features, including stronger encryption and firewall rules
- Supports a wider range of cloud providers and deployment options
- Active development with frequent updates and security patches
Cons of algo
- More complex setup process, requiring more technical knowledge
- Less user-friendly interface for managing VPN connections
- Higher resource requirements for server deployment
Code Comparison
algo:
./algo deploy
subspace:
docker run -d --name subspace \
-e SUBSPACE_HTTP_HOST=subspace.example.com \
-v /root/subspace:/data \
-p 80:80 -p 443:443 \
subspacecloud/subspace:latest
The algo deployment process involves running a single command, but requires more configuration beforehand. Subspace uses a Docker container, making it easier to deploy but potentially less flexible for advanced configurations.
Both projects aim to simplify VPN setup, but algo focuses more on security and flexibility, while subspace prioritizes ease of use and management. Algo is better suited for users with technical expertise who require advanced security features, whereas subspace is ideal for those seeking a simpler, more user-friendly VPN solution.
Streisand sets up a new server running your choice of WireGuard, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, or a Tor bridge. It also generates custom instructions for all of these services. At the end of the run you are given an HTML file with instructions that can be shared with friends, family members, and fellow activists.
Pros of Streisand
- Supports a wider range of VPN protocols and services
- Provides more detailed documentation and setup instructions
- Offers additional privacy-enhancing features like DNS leak protection
Cons of Streisand
- More complex setup process
- Requires more server resources due to multiple services
- Less frequent updates and maintenance
Code Comparison
Streisand (Ansible playbook excerpt):
- name: Install OpenVPN
apt:
name: openvpn
state: present
- name: Configure OpenVPN server
template:
src: openvpn-server.conf.j2
dest: /etc/openvpn/server.conf
Subspace (Docker Compose excerpt):
version: '3'
services:
subspace:
image: subspacecloud/subspace:latest
volumes:
- ./data:/data
ports:
- "51820:51820/udp"
Streisand offers a more comprehensive set of VPN options and privacy tools, making it suitable for users who require advanced features and flexibility. However, this comes at the cost of increased complexity and resource requirements.
Subspace, on the other hand, focuses on simplicity and ease of use, leveraging Docker for quick deployment. It's more suitable for users who want a straightforward WireGuard VPN solution without the need for additional services.
The code comparison highlights the different approaches: Streisand uses Ansible for configuration management, while Subspace relies on Docker for containerization and simplified deployment.
OpenVPN road warrior installer for Ubuntu, Debian, AlmaLinux, Rocky Linux, CentOS and Fedora
Pros of openvpn-install
- Simple, straightforward script for quick OpenVPN setup
- Widely used and community-tested
- Supports various Linux distributions
Cons of openvpn-install
- Limited to OpenVPN protocol only
- Lacks a user-friendly interface for management
- Requires manual configuration for advanced features
Code Comparison
openvpn-install:
#!/bin/bash
# OpenVPN installer for Debian, Ubuntu, and CentOS
# Detect Debian users running the script with "sh" instead of bash
if readlink /proc/$$/exe | grep -q "dash"; then
echo 'This installer needs to be run with "bash", not "sh".'
exit
fi
Subspace:
package main
import (
"fmt"
"log"
"net/http"
"os"
"github.com/subspacecloud/subspace/manager"
)
func main() {
manager.Run()
}
The openvpn-install project is a bash script focused solely on OpenVPN installation, while Subspace is a more comprehensive Go-based VPN management solution with a web interface and support for multiple protocols.
The Simplest VPN installer, designed for Raspberry Pi
Pros of PiVPN
- Specifically designed for Raspberry Pi, making it ideal for home/small office setups
- Simple command-line interface for easy setup and management
- Supports both OpenVPN and WireGuard protocols
Cons of PiVPN
- Limited to Raspberry Pi and similar single-board computers
- Lacks a graphical user interface, which may be challenging for less technical users
- Fewer advanced features compared to Subspace
Code Comparison
PiVPN (installation script):
curl -L https://install.pivpn.io | bash
Subspace (Docker deployment):
version: "3.3"
services:
subspace:
image: subspacecloud/subspace:latest
volumes:
- /path/to/data:/data
ports:
- 80:80
While PiVPN uses a simple bash script for installation, Subspace employs Docker for deployment, offering more flexibility and easier management across different platforms.
PiVPN is tailored for Raspberry Pi users seeking a straightforward VPN solution, while Subspace provides a more feature-rich, cross-platform experience with a web-based interface. The choice between them depends on the user's specific needs, technical expertise, and hardware preferences.
Scripts to build your own IPsec VPN server, with IPsec/L2TP, Cisco IPsec and IKEv2
Pros of setup-ipsec-vpn
- Focuses on IPsec/L2TP and Cisco IPsec VPN protocols, which are widely supported by default on many devices
- Provides detailed setup instructions for various cloud providers and operating systems
- Includes additional security features like fail2ban and unattended upgrades
Cons of setup-ipsec-vpn
- Limited to IPsec-based VPN protocols, which may not be ideal for all use cases
- Requires more manual configuration and management compared to Subspace's user-friendly interface
- May have higher resource usage due to the nature of IPsec protocols
Code Comparison
setup-ipsec-vpn:
wget https://git.io/vpnsetup -O vpnsetup.sh
sudo sh vpnsetup.sh
Subspace:
docker run -d --name subspace \
--restart=always \
-v /root/subspace:/data \
-p 80:80 -p 443:443 -p 51820:51820/udp \
subspacecloud/subspace:latest
The setup-ipsec-vpn project uses a shell script for installation, while Subspace utilizes Docker for easy deployment and management.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
NOTE: New versions of Subspace
Subspace Commmunity
The most actively maintained fork of Subspace with a number of improvements.
Subspace Community Fork
WarpSpeed VPN
WarpSpeed VPN is an enhanced commercial rewrite of Subspace with a number of major improvements. It is free for personal use and for small open source projects. Designed to support the Subspace creator's new projects.
WarpSpeed VPN on 1-Click Digital Ocean Marketplace
Subspace - A simple WireGuard VPN server GUI
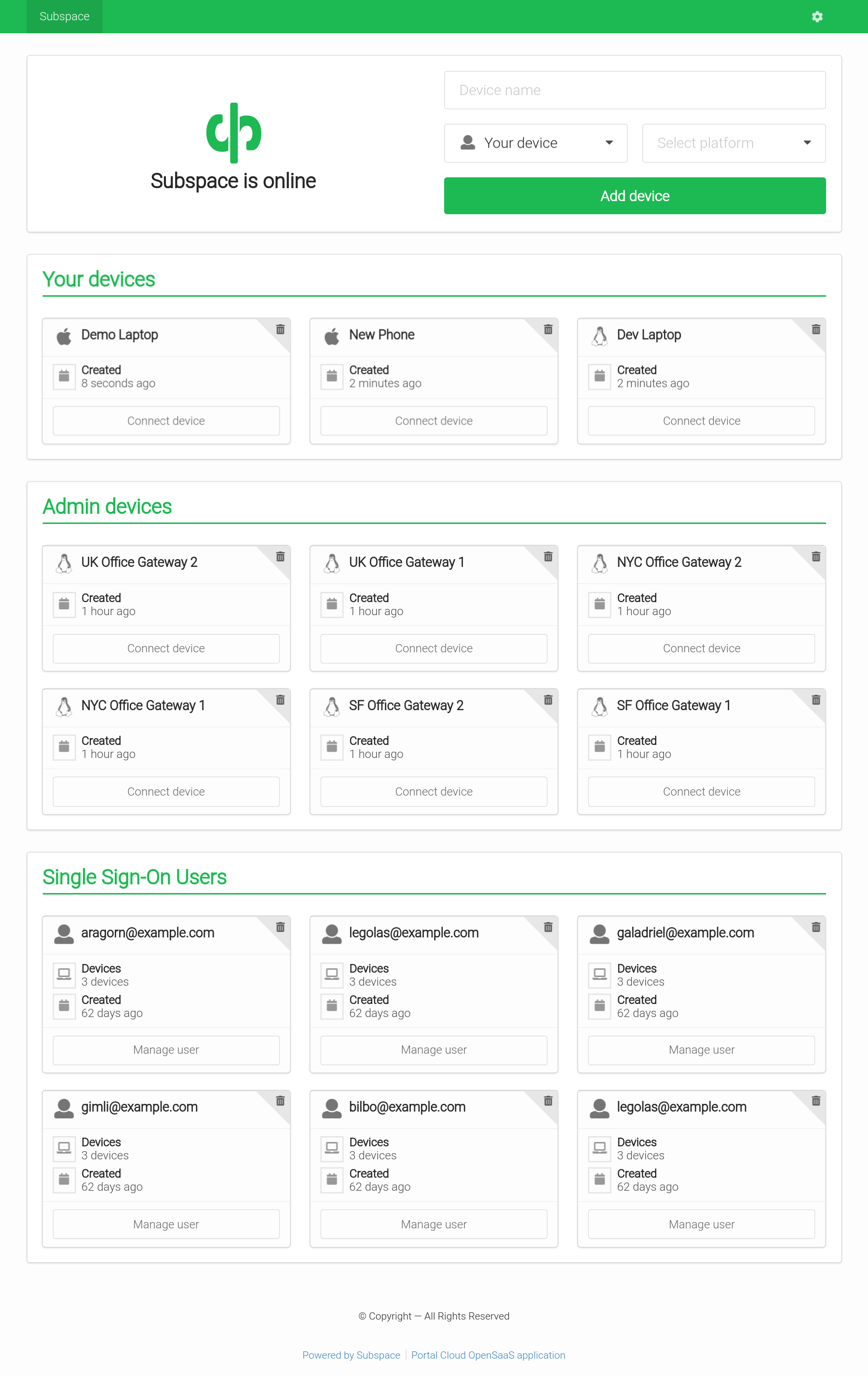
Screenshots
Features
- WireGuard VPN Protocol
- The most modern and fastest VPN protocol.
- Single Sign-On (SSO) with SAML
- Support for SAML providers like G Suite and Okta.
- Add Devices
- Connect from Mac OS X, Windows, Linux, Android, or iOS.
- Remove Devices
- Removes client key and disconnects client.
- Auto-generated Configs
- Each client gets a unique downloadable config file.
- Generates a QR code for easy importing on iOS and Android.
Run Subspace on a VPS
Running Subspace on a VPS is designed to be as simple as possible.
- Public Docker image.
- Single static Go binary with assets bundled.
- Automatic TLS using Let's Encrypt.
- Redirects http to https.
- Works with a reverse proxy or standalone.
1. Get a server
Recommended Specs
- Type: VPS or dedicated
- Distribution: Ubuntu 16.04 (Xenial)
- Memory: 512MB or greater
2. Add a DNS record
Create a DNS A record in your domain pointing to your server's IP address.
Example: subspace.example.com A 172.16.1.1
3. Enable Let's Encrypt
Subspace runs a TLS ("SSL") https server on port 443/tcp. It also runs a standard web server on port 80/tcp to redirect clients to the secure server. Port 80/tcp is required for Let's Encrypt verification.
Requirements
- Your server must have a publicly resolvable DNS record.
- Your server must be reachable over the internet on ports 80/tcp and 443/tcp and 51820/udp (WireGuard).
Usage
Example usage:
$ subspace --http-host subspace.example.com
Usage
-backlink string
backlink (optional)
-datadir string
data dir (default "/data")
-debug
debug mode
-help
display help and exit
-http-addr string
HTTP listen address (default ":80")
-http-host string
HTTP host
-http-insecure
enable sessions cookies for http (no https) not recommended
-letsencrypt
enable TLS using Let's Encrypt on port 443 (default true)
-version
display version and exit
Run as a Docker container
Install WireGuard on the host
The container expects WireGuard to be installed on the host. The official image is subspacecloud/subspace.
add-apt-repository -y ppa:wireguard/wireguard
apt-get update
apt-get install -y wireguard
# Remove dnsmasq because it will run inside the container.
apt-get remove -y dnsmasq
# Set DNS server.
echo nameserver 1.1.1.1 >/etc/resolv.conf
# Load modules.
modprobe wireguard
modprobe iptable_nat
modprobe ip6table_nat
# Enable IP forwarding
sysctl -w net.ipv4.ip_forward=1
sysctl -w net.ipv6.conf.all.forwarding=1
Follow the official Docker install instructions: Get Docker CE for Ubuntu
Make sure to change the --env SUBSPACE_HTTP_HOST to your publicly accessible domain name.
# Your data directory should be bind-mounted as `/data` inside the container using the `--volume` flag.
$ mkdir /data
docker create \
--name subspace \
--restart always \
--network host \
--cap-add NET_ADMIN \
--volume /usr/bin/wg:/usr/bin/wg \
--volume /data:/data \
--env SUBSPACE_HTTP_HOST=subspace.example.com \
subspacecloud/subspace:latest
$ sudo docker start subspace
$ sudo docker logs subspace
<log output>
Updating the container image
Pull the latest image, remove the container, and re-create the container as explained above.
# Pull the latest image
$ sudo docker pull subspacecloud/subspace
# Stop the container
$ sudo docker stop subspace
# Remove the container (data is stored on the mounted volume)
$ sudo docker rm subspace
# Re-create and start the container
$ sudo docker create ... (see above)
Help / Reporting Bugs
Not (currently) available. Coming soon.
Top Related Projects
Set up a personal VPN in the cloud
Streisand sets up a new server running your choice of WireGuard, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, or a Tor bridge. It also generates custom instructions for all of these services. At the end of the run you are given an HTML file with instructions that can be shared with friends, family members, and fellow activists.
OpenVPN road warrior installer for Ubuntu, Debian, AlmaLinux, Rocky Linux, CentOS and Fedora
The Simplest VPN installer, designed for Raspberry Pi
Scripts to build your own IPsec VPN server, with IPsec/L2TP, Cisco IPsec and IKEv2
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot