 terrascan
terrascan
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Top Related Projects
Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Snyk CLI scans and monitors your projects for security vulnerabilities.
Write tests against structured configuration data using the Open Policy Agent Rego query language
Linting tool for CloudFormation templates
Find secrets with Gitleaks 🔑
Quick Overview
Terrascan is an open-source security vulnerability scanner for Infrastructure as Code (IaC) tools such as Terraform, Kubernetes, Docker, and Helm. It helps detect compliance and security violations across IaC to mitigate risk before provisioning cloud-native infrastructure.
Pros
- Supports multiple IaC tools and cloud platforms
- Integrates easily with CI/CD pipelines
- Customizable policies using Rego language
- Regularly updated with new policies and features
Cons
- Learning curve for custom policy creation
- May produce false positives in some scenarios
- Limited support for certain cloud-specific resources
- Documentation could be more comprehensive for advanced use cases
Getting Started
To install Terrascan:
curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Darwin_x86_64.tar.gz")" > terrascan.tar.gz
tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
sudo mv terrascan /usr/local/bin/
terrascan version
To scan a Terraform directory:
terrascan scan -d /path/to/terraform/directory
To scan a Kubernetes YAML file:
terrascan scan -f /path/to/kubernetes/file.yaml
To run Terrascan with custom policies:
terrascan scan -d /path/to/iac/directory -p /path/to/custom/policies
Competitor Comparisons
Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
Pros of Trivy
- Broader scope: Scans containers, filesystems, git repositories, and more, not just IaC
- Faster scanning speed, especially for large projects
- More frequent updates and larger community support
Cons of Trivy
- Less focused on IaC-specific vulnerabilities compared to Terrascan
- May require additional configuration for comprehensive IaC scanning
- Potentially overwhelming output for users primarily interested in IaC issues
Code Comparison
Terrascan example:
terrascan scan -i terraform
Trivy example:
trivy config ./terraform-files
Both tools can scan Terraform files, but Trivy requires specifying the config scanning mode, while Terrascan is more IaC-focused by default.
Summary
Trivy offers a more versatile scanning solution with broader coverage and faster performance, making it suitable for teams looking for a comprehensive security tool. However, Terrascan provides a more specialized approach to IaC scanning, which may be preferable for teams primarily focused on infrastructure security. The choice between the two depends on specific project requirements and the desired balance between breadth and depth of scanning capabilities.
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Pros of Checkov
- Supports a wider range of infrastructure-as-code (IaC) formats, including Terraform, CloudFormation, Kubernetes, Dockerfile, and more
- Offers a more extensive policy library with over 1000 built-in policies
- Provides integration with CI/CD pipelines and cloud environments for continuous scanning
Cons of Checkov
- May have a steeper learning curve due to its broader scope and feature set
- Can be slower to scan large codebases compared to Terrascan's focused approach
Code Comparison
Terrascan:
resource "aws_s3_bucket" "example" {
bucket = "my-bucket"
acl = "private"
}
Checkov:
resource "aws_s3_bucket" "example" {
bucket = "my-bucket"
acl = "private"
versioning {
enabled = true
}
}
In this example, Checkov's policy library would likely flag the Terrascan example for not enabling versioning, while both tools would pass the Checkov example as it includes versioning configuration.
Snyk CLI scans and monitors your projects for security vulnerabilities.
Pros of Snyk CLI
- Broader scope: Covers more than just IaC, including application dependencies and container security
- Extensive vulnerability database: Provides access to Snyk's comprehensive vulnerability database
- Integration with CI/CD: Offers seamless integration with various CI/CD pipelines
Cons of Snyk CLI
- Requires account: Free tier available, but full features need a paid account
- Resource intensive: Can be slower and more resource-heavy for large projects
- Learning curve: More complex to use due to its broader feature set
Code Comparison
Terrascan:
terrascan scan -i terraform
Snyk CLI:
snyk iac test /path/to/terraform/files
Both tools can scan Terraform files, but Snyk CLI offers a more comprehensive security analysis beyond just Infrastructure as Code.
Key Differences
- Terrascan focuses specifically on IaC security, while Snyk CLI covers a wider range of security concerns
- Terrascan is open-source and free to use, whereas Snyk CLI has a freemium model with paid tiers
- Snyk CLI provides more detailed vulnerability information and remediation advice
Overall, choose Terrascan for focused IaC security scanning, and Snyk CLI for a more comprehensive security solution across multiple aspects of your development pipeline.
Write tests against structured configuration data using the Open Policy Agent Rego query language
Pros of Conftest
- More flexible policy language (Rego) allowing for complex, custom policies
- Supports a wider range of configuration file formats (YAML, JSON, HCL, etc.)
- Can be integrated into various CI/CD pipelines and workflows
Cons of Conftest
- Steeper learning curve due to Rego language complexity
- Less out-of-the-box policies compared to Terrascan
- Requires more manual setup and configuration
Code Comparison
Terrascan policy example:
resource "aws_s3_bucket" "example" {
bucket = "my-bucket"
acl = "private"
}
Conftest policy example:
package main
deny[msg] {
input.resource.aws_s3_bucket[name]
not input.resource.aws_s3_bucket[name].acl == "private"
msg = sprintf("S3 bucket '%v' must have private ACL", [name])
}
Both tools aim to enforce security policies, but Conftest offers more flexibility in policy definition using Rego, while Terrascan provides a simpler approach with pre-defined policies. Conftest's versatility comes at the cost of a steeper learning curve, whereas Terrascan offers easier setup and use with its built-in ruleset.
Linting tool for CloudFormation templates
Pros of cfn_nag
- Specialized for CloudFormation templates, offering deeper AWS-specific checks
- Supports custom rule creation, allowing for tailored security policies
- Integrates well with CI/CD pipelines for AWS-focused projects
Cons of cfn_nag
- Limited to CloudFormation templates, lacking multi-cloud support
- May require more AWS-specific knowledge to use effectively
- Less frequent updates compared to Terrascan
Code Comparison
cfn_nag:
require 'cfn-nag'
cfn_nag = CfnNag.new
violations = cfn_nag.audit_file(filename: 'path/to/cloudformation.yaml')
violations.each do |violation|
puts "#{violation.type} #{violation.message}"
end
Terrascan:
terrascan init
terrascan scan -i aws -t aws
Summary
cfn_nag is a specialized tool for CloudFormation security scanning, offering deep AWS-specific checks and custom rule creation. However, it's limited to CloudFormation and may require more AWS expertise. Terrascan, on the other hand, provides multi-cloud support and more frequent updates, but may lack the depth of AWS-specific checks that cfn_nag offers. The choice between the two depends on the project's focus and the development team's expertise.
Find secrets with Gitleaks 🔑
Pros of Gitleaks
- Specialized in detecting secrets and sensitive information in git repositories
- Supports scanning of local repositories and GitHub/GitLab integrations
- Highly customizable with regex patterns and rules
Cons of Gitleaks
- Limited to secret scanning, lacks broader security and compliance checks
- May require more manual configuration for specific use cases
Code Comparison
Gitleaks configuration example:
[[rules]]
description = "AWS Access Key"
regex = '''(A3T[A-Z0-9]|AKIA|AGPA|AIDA|AROA|AIPA|ANPA|ANVA|ASIA)[A-Z0-9]{16}'''
tags = ["key", "AWS"]
Terrascan rule example:
- name: aws_s3_bucket_versioning_not_enabled
file: s3.tf
resource: aws_s3_bucket
check:
operator: exists
value: versioning
Summary
Gitleaks focuses on secret detection in git repositories, offering specialized features for this purpose. It excels in identifying sensitive information but lacks broader security checks. Terrascan, on the other hand, provides a more comprehensive approach to infrastructure-as-code security and compliance scanning, covering multiple cloud providers and frameworks. The choice between the two depends on specific security needs and the scope of the project.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

Introduction
Terrascan is a static code analyzer for Infrastructure as Code. Terrascan allows you to:
- Seamlessly scan infrastructure as code for misconfigurations.
- Monitor provisioned cloud infrastructure for configuration changes that introduce posture drift, and enables reverting to a secure posture.
- Detect security vulnerabilities and compliance violations.
- Mitigate risks before provisioning cloud native infrastructure.
- Offers flexibility to run locally or integrate with your CI\CD.
Resources
-
To try Terrascan in your browser, see the Terrascan Sandbox https://www.tenable.com/terrascan
-
To learn more about Terrascan's features and capabilities, see the documentation portal: https://runterrascan.io
Key features
- 500+ Policies for security best practices
- Scanning of Terraform (HCL2)
- Scanning of AWS CloudFormation Templates (CFT)
-
- Scanning of Azure Resource Manager (ARM)
- Scanning of Kubernetes (JSON/YAML), Helm v3, and Kustomize
- Scanning of Dockerfiles
- Support for AWS, Azure, GCP, Kubernetes, Dockerfile, and GitHub
- Integrates with docker image vulnerability scanning for AWS, Azure, GCP, Harbor container registries.
Quick Start
Step 1: Install
Terrascan supports multiple ways to install and is also available as a Docker image. See Terrascan's releases page for the latest version of builds in all supported platforms. Select the correct binary for your platform.
Install as a native executable
curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Linux_x86_64.tar.gz")" > terrascan.tar.gz
tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
sudo install terrascan /usr/local/bin && rm terrascan
terrascan
Install on ArchLinux / Manjaro via AUR
ArchLinux and Manjaro users can install by:
yay -S terrascan
Install via brew
Homebrew users can install by:
$ brew install terrascan
Docker image
Terrascan is also available as a Docker image and can be used as follows
$ docker run tenable/terrascan
Refer to documentation for information.
Step 2: Scan
To scan your code for security issues you can run the following (defaults to scanning Terraform).
$ terrascan scan
Note: Terrascan will exit with an error code if any errors or violations are found during a scan.
List of possible Exit Codes
| Scenario | Exit Code |
|---|---|
| scan summary has errors and violations | 5 |
| scan summary has errors but no violations | 4 |
| scan summary has violations but no errors | 3 |
| scan summary has no violations or errors | 0 |
| scan command errors out due to invalid inputs | 1 |
Step 3: Integrate with CI\CD
Terrascan can be integrated into CI/CD pipelines to enforce security best practices. Please refer to our documentation to integrate with your pipeline.
Terrascan Commands
You can use the terrascan command with the following options:
$ terrascan
Terrascan
Usage:
terrascan [command]
Available Commands:
help Help about any command
init Initialize Terrascan
scan Detect compliance and security violations across Infrastructure as Code.
server Run Terrascan as an API server
version Terrascan version
Flags:
-c, --config-path string config file path
-h, --help help for terrascan
-l, --log-level string log level (debug, info, warn, error, panic, fatal) (default "info")
-x, --log-type string log output type (console, json) (default "console")
-o, --output string output type (human, json, yaml, xml) (default "human")
Use "terrascan [command] --help" for more information about a command.
Policies
Terrascan policies are written using the Rego policy language. Every rego includes a JSON "rule" file which defines metadata for the policy. By default, Terrascan downloads policies from Terrascan repositories while scanning for the first time. However, if you want to download the latest policies, you need to run the Initialization process. See Usage for information about the Initialization process.
Note: The scan command will implicitly run the initialization process if there are no policies found.
Docker Image Vulnerabilities
You can use the --find-vuln flag to collect vulnerabilities as reported in its registry as part of Terrascan's output. Currently Terrascan supports Elastic Container Registry (ECR), Azure Container Registry, Google Container Registry, and Google Artifact Registry.
The --find-vuln flag can be used when scanning IaC files as follows:
$ terrascan scan -i <IaC provider> --find-vuln
For more information and explanation of how to setup your environment to authenticate with the registry's APIs see the usage documentation.
Customizing scans
By default, Terrascan scans your entire configuration against all policies. However, Terrascan supports granular configuration of policies and resources.
Read more about in-file instrumentation and the config file on our documentation site.
For now, some quick tips:
- Exclude a particular policy for a specific resource.
- Manually configure policies to be suppressed or applied globally from a scan across all resources or, for just a particular resource.
How to exclude a policy while scanning a resource
You can configure Terrascan to skip a particular policy (rule) while scanning a resource. Follow these steps depending on your platform:
Terraform
Use Terraform scripts to configure Terrascan to skip rules by inserting a comment with the phrase "ts:skip=<RULENAME><SKIP_REASON>". The comment should be included inside the resource as shown in the example below.

Kubernetes
In Kubernetes yamls, you can configure Terrascan to skip policies by adding an annotation as seen in the snippet below.

How to include or exclude specific policies or resources from being scanned
Use the Terrascan config file to manually select the policies which should be included or excluded from the entire scan. This is suitable for edge use cases. Use the "in-file" suppression option to specify resources that should be excluded from being tested against selected policies. This ensures that the policies are skipped only for particular resources, rather than all of the resources.

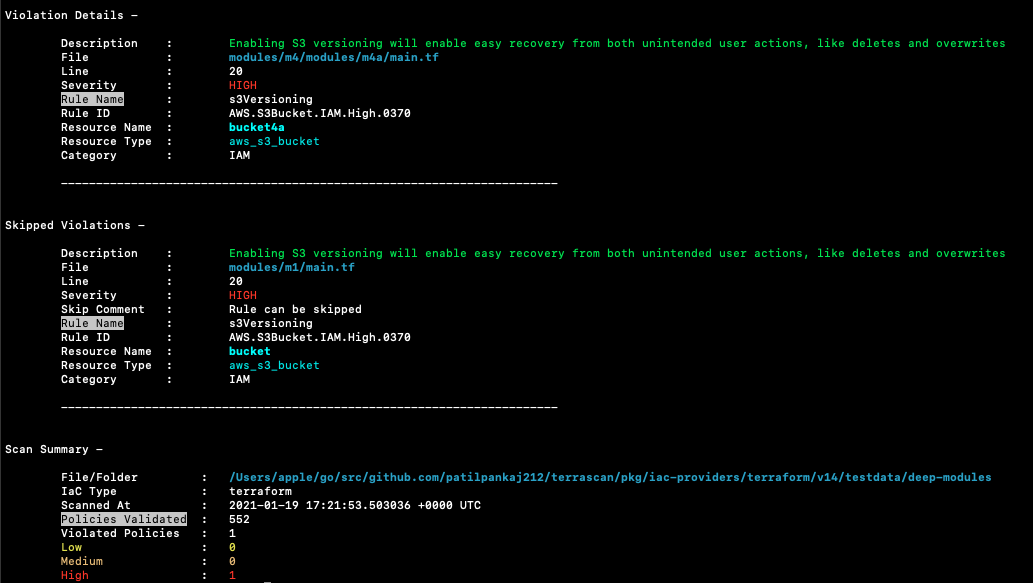
Sample scan output
Terrascan's default output is a list of violations present in the scanned IaC. A sample output:
Building Terrascan
Terrascan can be built locally. This is helpful if you want to be on the latest version or when developing Terrascan. gcc and Go 1.19 or above are required.
$ git clone git@github.com:tenable/terrascan.git
$ cd terrascan
$ make build
$ ./bin/terrascan
To build your own docker, refer to this example (Alpine Linux):
FROM golang:alpine AS build-env
RUN apk add --update git
RUN git clone https://github.com/tenable/terrascan && cd terrascan \
&& CGO_ENABLED=0 GO111MODULE=on go build -o /go/bin/terrascan cmd/terrascan/main.go
Developing Terrascan
To learn more about developing and contributing to Terrascan, refer to the contributing guide.
Code of Conduct
We believe having an open and inclusive community benefits all of us. Please note that this project is released with a Contributor Code of Conduct. By participating in this project you agree to abide by its terms.
License
Terrascan is licensed under the Apache 2.0 License.
Stargazers
Forkers
Top Related Projects
Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Snyk CLI scans and monitors your projects for security vulnerabilities.
Write tests against structured configuration data using the Open Policy Agent Rego query language
Linting tool for CloudFormation templates
Find secrets with Gitleaks 🔑
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot



