Top Related Projects
Hunt down social media accounts by username across social networks
Information gathering framework for phone numbers
E-mails, subdomains and names Harvester - OSINT
SpiderFoot automates OSINT for threat intelligence and mapping your attack surface.
🕵️♂️ Collect a dossier on a person by username from thousands of sites
:scream: A curated list of amazingly awesome OSINT
Quick Overview
Seeker is an open-source geolocation tracking tool designed for educational purposes. It allows users to obtain high-accuracy location data of a target device by creating a malicious website that requests location permissions. The project is intended for cybersecurity research and awareness, not for malicious use.
Pros
- Provides highly accurate geolocation data, including latitude, longitude, and accuracy
- Easy to set up and use, with minimal dependencies
- Supports multiple tunneling options for remote access
- Includes additional device information gathering capabilities
Cons
- Can be misused for malicious purposes if not handled responsibly
- Requires target to grant location permissions, which may raise suspicion
- Limited to devices with GPS capabilities and internet access
- May be detected by some antivirus software as potentially harmful
Getting Started
-
Clone the repository:
git clone https://github.com/thewhiteh4t/seeker.git -
Navigate to the Seeker directory:
cd seeker -
Install dependencies:
pip3 install -r requirements.txt -
Run Seeker:
python3 seeker.py -
Choose a tunneling option when prompted and follow the on-screen instructions to set up the malicious website.
-
Send the generated link to the target and wait for them to grant location permissions.
-
Once the target accesses the link and grants permissions, their location data will be displayed in the terminal.
Note: Use this tool responsibly and only for educational or authorized testing purposes. Obtaining someone's location without consent may be illegal in many jurisdictions.
Competitor Comparisons
Hunt down social media accounts by username across social networks
Pros of Sherlock
- Broader scope: Searches for usernames across 300+ websites
- More active development: Frequent updates and contributions
- Extensive documentation and usage instructions
Cons of Sherlock
- Slower execution due to checking multiple sites
- May produce false positives in some cases
- Requires more dependencies and setup
Code Comparison
Sherlock (Python):
def sherlock(username):
for site in sites:
response = requests.get(f"{site.url}/{username}")
if response.status_code == 200:
print(f"Found on {site.name}")
Seeker (JavaScript):
function getLocation() {
if (navigator.geolocation) {
navigator.geolocation.getCurrentPosition(showPosition);
} else {
console.log("Geolocation is not supported by this browser.");
}
}
Key Differences
Sherlock focuses on username searches across multiple platforms, while Seeker is primarily designed for geolocation tracking. Sherlock is written in Python and has a larger community, whereas Seeker is JavaScript-based and more specialized in its functionality.
Sherlock is better suited for broad online presence investigations, while Seeker excels in targeted geolocation tracking scenarios. The choice between the two depends on the specific use case and required functionality.
Information gathering framework for phone numbers
Pros of PhoneInfoga
- More comprehensive phone number analysis, including carrier and location data
- Supports multiple data sources and APIs for information gathering
- Actively maintained with regular updates and improvements
Cons of PhoneInfoga
- Focused solely on phone number reconnaissance, less versatile than Seeker
- Requires API keys for some features, potentially limiting free usage
- More complex setup and configuration compared to Seeker
Code Comparison
PhoneInfoga (Go):
func (s *Scanner) localScan(number *Number) (*Results, error) {
results := NewResults(number)
s.performLocalScan(number, results)
return results, nil
}
Seeker (Python):
def get_location():
global latitude, longitude
url = 'https://location.services.mozilla.com/v1/geolocate?key=' + lsession
data = requests.get(url).json()
latitude = data['location']['lat']
longitude = data['location']['lng']
PhoneInfoga focuses on phone number analysis using various APIs and data sources, while Seeker is designed for geolocation tracking. PhoneInfoga is written in Go and offers more comprehensive phone-related information, whereas Seeker is a Python-based tool that provides real-time location data. The code snippets demonstrate their different approaches: PhoneInfoga performs local scans on phone numbers, while Seeker retrieves geolocation data from external services.
E-mails, subdomains and names Harvester - OSINT
Pros of theHarvester
- More comprehensive information gathering tool, covering a wider range of sources
- Actively maintained with regular updates and contributions
- Supports multiple output formats (HTML, XML, JSON)
Cons of theHarvester
- More complex to use, requiring more configuration and setup
- Slower execution due to the breadth of sources it queries
- May produce more false positives or irrelevant results
Code Comparison
theHarvester:
from theHarvester.discovery import *
from theHarvester.discovery.constants import *
search = googlesearch.search_google(word, limit, start)
search.process()
emails = search.get_emails()
Seeker:
def get_location():
global latitude, longitude
req = requests.get(f'https://api.ipapi.com/api/{ip}?access_key={access_key}')
data = req.json()
latitude = data['latitude']
longitude = data['longitude']
Summary
theHarvester is a more comprehensive tool for information gathering, offering a wider range of sources and output formats. However, it's more complex to use and may produce more irrelevant results. Seeker, on the other hand, focuses specifically on geolocation tracking, making it simpler and more targeted for that specific use case. The code comparison shows theHarvester's focus on email discovery from various sources, while Seeker emphasizes geolocation data retrieval.
SpiderFoot automates OSINT for threat intelligence and mapping your attack surface.
Pros of Spiderfoot
- More comprehensive OSINT tool with a wider range of modules and data sources
- Offers a web-based GUI for easier visualization and interaction
- Supports automation and scheduling of scans
Cons of Spiderfoot
- More complex setup and configuration process
- Requires more system resources due to its extensive functionality
- Steeper learning curve for new users
Code Comparison
Seeker (Python):
def get_location():
global latitude, longitude
if args.location:
location = args.location.split(',')
latitude = location[0]
longitude = location[1]
else:
latitude = input('\n' + G + '[+]' + C + ' Enter Latitude : ' + W)
longitude = input(G + '[+]' + C + ' Enter Longitude : ' + W)
Spiderfoot (Python):
def scanTarget(self, target):
# Normalize the target
targetType = SpiderFootHelpers.targetTypeFromString(target)
if targetType is None:
self.status("Invalid target type. Could not recognize it as a valid target type.")
return
t = SpiderFootTarget(target, targetType)
self.target = t
Both projects are written in Python, but Spiderfoot's codebase is more extensive and modular. Seeker focuses on geolocation tracking, while Spiderfoot offers a broader range of OSINT capabilities.
🕵️♂️ Collect a dossier on a person by username from thousands of sites
Pros of Maigret
- Supports a much larger number of websites and platforms (2000+)
- More advanced search capabilities, including custom site parsing
- Actively maintained with frequent updates
Cons of Maigret
- More complex setup and usage compared to Seeker
- Requires more system resources due to its extensive functionality
- May produce more false positives due to its broad search scope
Code Comparison
Seeker (Python):
def get_location():
global latitude, longitude
if args.lhost and args.lport:
pass
else:
print('\n' + R + '[-]' + C + ' Getting Location Information...' + W + '\n')
try:
response = requests.get('https://ipapi.co/json/')
result = response.json()
latitude = result['latitude']
longitude = result['longitude']
except:
latitude = 0
longitude = 0
Maigret (Python):
async def extract_ids_from_url(url: str) -> List[str]:
try:
r = await get_response(url)
if r:
return re.findall(r'(?:^|/)(?P<id>[^/]+)/?$', r.url)
except Exception as e:
print(f'Error while fetching {url}: {e}')
return []
The code snippets show that Seeker focuses on geolocation, while Maigret emphasizes ID extraction from URLs, reflecting their different purposes and functionalities.
:scream: A curated list of amazingly awesome OSINT
Pros of awesome-osint
- Comprehensive collection of OSINT tools and resources
- Well-organized into categories for easy navigation
- Regularly updated with new tools and information
Cons of awesome-osint
- Not a standalone tool, requires additional setup for each resource
- May overwhelm users with the sheer number of options
- Lacks specific functionality, serving more as a directory
Code comparison
While a direct code comparison isn't relevant due to the nature of these repositories, here's a brief overview of their structure:
awesome-osint:
## Table of Contents
- [General Search](#general-search)
- [Main National Search Engines](#main-national-search-engines)
- [Meta Search](#meta-search)
...
seeker:
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from __future__ import print_function
import os
import sys
import time
...
Seeker is a focused Python tool for geolocation, while awesome-osint is a curated list of OSINT resources in Markdown format. The code structures reflect their different purposes and implementations.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

Available in

Concept behind Seeker is simple, just like we host phishing pages to get credentials why not host a fake page that requests your location like many popular location based websites. Read more on thewhiteh4t's Blog .Seeker Hosts a fake website which asks for Location Permission and if the target allows it, we can get :
- Longitude
- Latitude
- Accuracy
- Altitude - Not always available
- Direction - Only available if user is moving
- Speed - Only available if user is moving
Along with Location Information we also get Device Information without any permissions :
- Unique ID using Canvas Fingerprinting
- Device Model - Not always available
- Operating System
- Platform
- Number of CPU Cores - Approximate Results
- Amount of RAM - Approximate Results
- Screen Resolution
- GPU information
- Browser Name and Version
- Public IP Address
- Local IP Address
- Local Port
Automatic IP Address Reconnaissance is performed after the above information is received.
This tool is a Proof of Concept and is for Educational Purposes Only, Seeker shows what data a malicious website can gather about you and your devices and why you should not click on random links and allow critical permissions such as Location etc.
How is this Different from IP GeoLocation
-
Other tools and services offer IP Geolocation which is NOT accurate at all and does not give location of the target instead it is the approximate location of the ISP.
-
Seeker uses HTML API and gets Location Permission and then grabs Longitude and Latitude using GPS Hardware which is present in the device, so Seeker works best with Smartphones, if the GPS Hardware is not present, such as on a Laptop, Seeker fallbacks to IP Geolocation or it will look for Cached Coordinates.
-
Generally if a user accepts location permsission, Accuracy of the information recieved is accurate to approximately 30 meters
-
Accuracy depends on multiple factors which you may or may not control such as :
- Device - Won't work on laptops or phones which have broken GPS
- Browser - Some browsers block javascripts
- GPS Calibration - If GPS is not calibrated you may get inaccurate results and this is very common
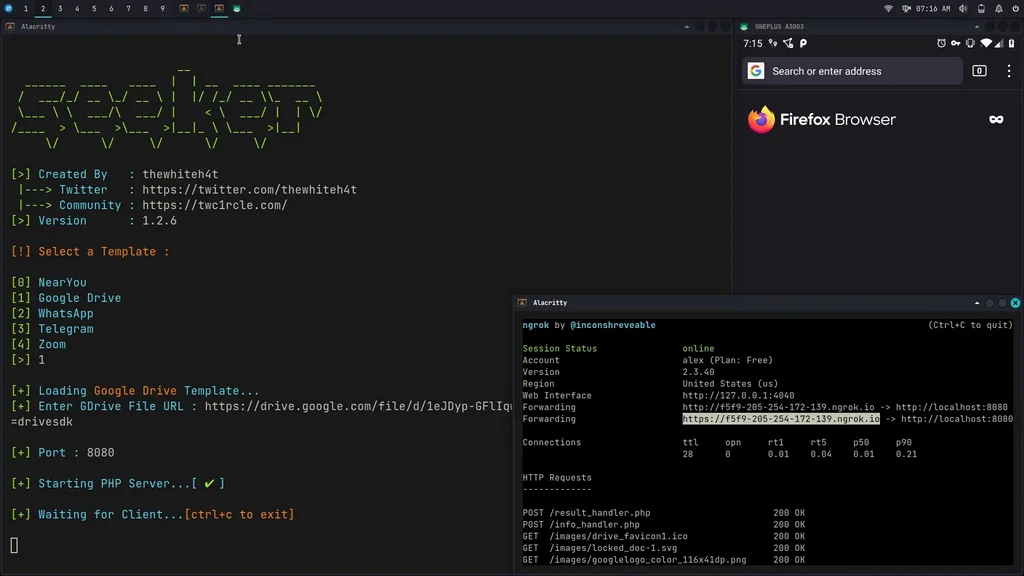
Templates
Available Templates :
- NearYou
- Google Drive (Suggested by @Akaal_no_one)
- WhatsApp (Suggested by @Dazmed707)
- Telegram
- Zoom (Made by @a7maadf)
- Google reCAPTCHA (Made by @MrEgyptian)
Create your own template ! Steps to let you create your template is described in this how-to
Once your template is ready, do not forget to propose it to the community via a PR (pull request)
Tested On :
- Kali Linux
- BlackArch Linux
- Ubuntu
- Fedora
- Kali Nethunter
- Termux
- Parrot OS
- OSX - Monterey v.12.0.1
Installation
Kali Linux / Arch Linux / Ubuntu / Fedora / Parrot OS / Termux
git clone https://github.com/thewhiteh4t/seeker.git
cd seeker/
chmod +x install.sh
./install.sh
BlackArch Linux
sudo pacman -S seeker
Docker
docker pull thewhiteh4t/seeker
OSX
git clone https://github.com/thewhiteh4t/seeker.git
cd seeker/
python3 seeker.py
In order to run in tunnel mode, install ngrok by running this command in the terminal:
brew install ngrok/ngrok/ngrok
ngrok http 8080
Usage
python3 seeker.py -h
usage: seeker.py [-h] [-k KML] [-p PORT] [-u] [-v] [-t TEMPLATE] [-d] [--telegram token:chatId] [--webhook WEBHOOK]
options:
-h, --help show this help message and exit
-k KML, --kml KML KML filename
-p PORT, --port PORT Web server port [ Default : 8080 ]
-u, --update Check for updates
-v, --version Prints version
-t TEMPLATE, --template TEMPLATE Auto choose the template with the given index
-d, --debugHTTP Disable auto http --> https redirection for testing purposes
(only works for the templates having index_temp.html file)
--telegram Send info to a telegram bot, provide telegram token and chat to use
format = token:chatId separated by a colon
--webhook Send events to a webhook endpoint to be processed
Note : endpoint must be unauthenticated and accept POST request
#########################
# Environment Variables #
#########################
Some of the options above can also be enabled via environment variables, to ease deployment.
Other parameters can be provided via environment variables to avoid interactive mode.
Variables:
DEBUG_HTTP Same as -d, --debugHTTP
PORT Same as -p, --port
TEMPLATE Same as -t, --template
TITLE Provide the group title or the page title
REDIRECT Provide the URL to redirect the user to, after the job is done
IMAGE Provide the image to use, can either be remote (http or https) or local
Note : Remote image will be downloaded locally during the startup
DESC Provide the description of the item (group or webpage depending on the template)
SITENAME Provide the name of the website
DISPLAY_URL Provide the URL to display on the page
MEM_NUM Provide the number of group membres (Telegram so far)
ONLINE_NUM Provide the number of the group online members (Telegram so far)
TELEGRAM Provide telegram token and chat to use to send info to a telegram bot
format = token:chatId separated by a colon
WEBHOOK Provide the webhook url to forward the events to
Note : endpoint should be unauthenticated and accept POST method
##################
# Usage Examples #
##################
# Step 1 : In first terminal
$ python3 seeker.py
# Step 2 : In second terminal start a tunnel service such as ngrok
$ ./ngrok http 8080
###########
# Options #
###########
# Ouput KML File for Google Earth
$ python3 seeker.py -k <filename>
# Use Custom Port
$ python3 seeker.py -p 1337
$ ./ngrok http 1337
# Pre-select a specific template
$ python3 seeker.py -t 1
################
# Docker Usage #
################
# Step 1
$ docker network create ngroknet
# Step 2
$ docker run --rm -it --net ngroknet --name seeker thewhiteh4t/seeker
# Step 3
$ docker run --rm -it --net ngroknet --name ngrok wernight/ngrok ngrok http seeker:8080
Local Tunnels
Use
ssh -R 80:localhost:8080 nokey@localhost.run
as an alterntive to ngrok
Demo
YouTube
Top Related Projects
Hunt down social media accounts by username across social networks
Information gathering framework for phone numbers
E-mails, subdomains and names Harvester - OSINT
SpiderFoot automates OSINT for threat intelligence and mapping your attack surface.
🕵️♂️ Collect a dossier on a person by username from thousands of sites
:scream: A curated list of amazingly awesome OSINT
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot




