Top Related Projects
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Scripted Local Linux Enumeration & Privilege Escalation Checks
A tool designed to exploit a privilege escalation vulnerability in the sudo program on Unix-like systems. It takes advantage of a specific misconfiguration or flaw in sudo to gain elevated privileges on the system, essentially allowing a regular user to execute commands as the root user.
Linux privilege escalation auditing tool
Quick Overview
BeRoot is a post-exploitation tool designed to identify privilege escalation opportunities on Windows and Linux systems. It scans for misconfigurations, vulnerable services, and other potential attack vectors that could allow an attacker to gain higher privileges on a compromised system.
Pros
- Cross-platform support for both Windows and Linux
- Comprehensive scanning of various privilege escalation vectors
- Actively maintained and regularly updated
- Easy to use with minimal setup required
Cons
- May trigger antivirus software or intrusion detection systems
- Requires administrative or root privileges to perform some checks
- Limited documentation for advanced usage scenarios
- Potential for false positives in complex environments
Getting Started
-
Clone the repository:
git clone https://github.com/AlessandroZ/BeRoot.git -
Install dependencies:
pip install -r requirements.txt -
Run BeRoot:
- On Windows:
python beRoot.py - On Linux:
python beRoot.py
- On Windows:
Note: Ensure you have appropriate permissions and understand the legal implications of using this tool in your environment.
Competitor Comparisons
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Pros of PEASS-ng
- More comprehensive privilege escalation suite covering multiple operating systems (Windows, Linux, macOS)
- Actively maintained with frequent updates and contributions from the community
- Includes both automated scripts and manual techniques for privilege escalation
Cons of PEASS-ng
- Larger codebase and more complex structure, potentially harder to navigate for beginners
- May trigger antivirus software due to its comprehensive nature and techniques used
Code Comparison
BeRoot (Python):
def check_msv1_0():
try:
hive = winreg.OpenKey(winreg.HKEY_LOCAL_MACHINE, r"SYSTEM\CurrentControlSet\Control\Lsa")
value = winreg.QueryValueEx(hive, "RunAsPPL")[0]
if value == 0:
print_debug("MSV1_0 authentication package could be used to dump credentials")
except:
pass
PEASS-ng (PowerShell):
function Get-UnquotedService {
$vuln = Get-WmiObject win32_service | Where-Object {$_.PathName -notlike '"*"' -and $_.PathName -like '* *'} | Select-Object Name, PathName, StartMode
if ($vuln) {
$vuln | ForEach-Object {
Write-Host "Unquoted Service Path: $($_.PathName)" -ForegroundColor Yellow
}
}
}
Both tools aim to identify privilege escalation vectors, but PEASS-ng offers a more extensive set of checks across multiple platforms, while BeRoot focuses primarily on Windows and Linux environments.
Scripted Local Linux Enumeration & Privilege Escalation Checks
Pros of LinEnum
- More comprehensive system enumeration, covering a wider range of potential privilege escalation vectors
- Actively maintained with regular updates and contributions from the community
- Includes colorized output for better readability and result interpretation
Cons of LinEnum
- Slower execution due to its extensive checks and system enumeration
- May generate more noise in the output, making it harder to identify critical findings quickly
- Primarily focused on Linux systems, while BeRoot supports both Windows and Linux
Code Comparison
LinEnum:
#!/bin/bash
version="0.982"
# Check for root privileges
if [ "$(/usr/bin/id -u)" -eq "0" ]; then
echo "You are running as root. Please run as a normal user."
exit 1
fi
BeRoot:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from beroot.run import run
if __name__ == '__main__':
run()
LinEnum uses a bash script for its implementation, focusing on Linux-specific checks. BeRoot, on the other hand, is written in Python, allowing for cross-platform support and potentially easier extensibility. LinEnum's code snippet shows a check for root privileges, while BeRoot's main script is more concise and relies on imported modules for its functionality.
A tool designed to exploit a privilege escalation vulnerability in the sudo program on Unix-like systems. It takes advantage of a specific misconfiguration or flaw in sudo to gain elevated privileges on the system, essentially allowing a regular user to execute commands as the root user.
Pros of SUDO_KILLER
- Focuses specifically on sudo misconfigurations and vulnerabilities
- Provides detailed reports and recommendations for remediation
- Includes a feature to check for CVEs related to sudo
Cons of SUDO_KILLER
- Limited to sudo-related privilege escalation techniques
- May require more manual analysis of results compared to BeRoot
- Less frequently updated than BeRoot
Code Comparison
SUDO_KILLER (check for sudo version):
sudo_version=$(sudo -V | grep "Sudo version" | cut -d" " -f3)
if [ -n "$sudo_version" ]; then
echo "[+] Sudo version: $sudo_version"
else
echo "[-] Unable to determine sudo version"
fi
BeRoot (check for writable folders):
def get_writable_folders(self):
writable = []
for path in self.get_system_path():
if os.access(path, os.W_OK):
writable.append(path)
return writable
Both tools aim to identify privilege escalation vulnerabilities, but SUDO_KILLER specializes in sudo-related issues, while BeRoot offers a broader approach to privilege escalation detection across different systems. SUDO_KILLER provides more detailed reports and remediation suggestions, while BeRoot may be easier to integrate into automated workflows due to its Python implementation.
Linux privilege escalation auditing tool
Pros of linux-exploit-suggester
- Focuses specifically on Linux systems, providing more targeted exploit suggestions
- Regularly updated with new exploits and vulnerabilities
- Lightweight and easy to run on target systems
Cons of linux-exploit-suggester
- Limited to Linux systems, while BeRoot supports Windows and Linux
- Lacks privilege escalation techniques beyond kernel exploits
- Does not provide as comprehensive system information gathering as BeRoot
Code Comparison
BeRoot (Python):
def check_msvcr71():
if os.path.exists("C:\\Windows\\System32\\msvcr71.dll"):
return True
return False
linux-exploit-suggester (Bash):
kernel_version=$(uname -r | cut -d'-' f1)
if [[ "$kernel_version" =~ ^2\.6\.(9|10|16|18|20|21|22|23|24|25|26|27|28|29|30|31|32|33|34|35)$ ]]; then
echo "[+] Kernel version $kernel_version is vulnerable to CVE-2010-3301"
fi
Both tools aim to identify potential privilege escalation vectors, but BeRoot provides a more comprehensive approach across multiple operating systems, while linux-exploit-suggester focuses on kernel-level exploits for Linux systems.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
BeRoot Project
BeRoot Project is a post exploitation tool to check common misconfigurations to find a way to escalate our privilege.
It has been added to the pupy project as a post exploitation module (so it will be executed in memory without touching the disk).
This tool does not realize any exploitation. It mains goal is not to realize a configuration assessment of the host (listing all services, all processes, all network connection, etc.) but to print only information that have been found as potential way to escalate our privilege.
This project works on Windows, Linux and Mac OS. You could find the Windows version here and the Linux and Mac OS here
I recommend reading the README depending on the targeted OS, to better understand what's happening.
I tried to implement most techniques described in this picture:
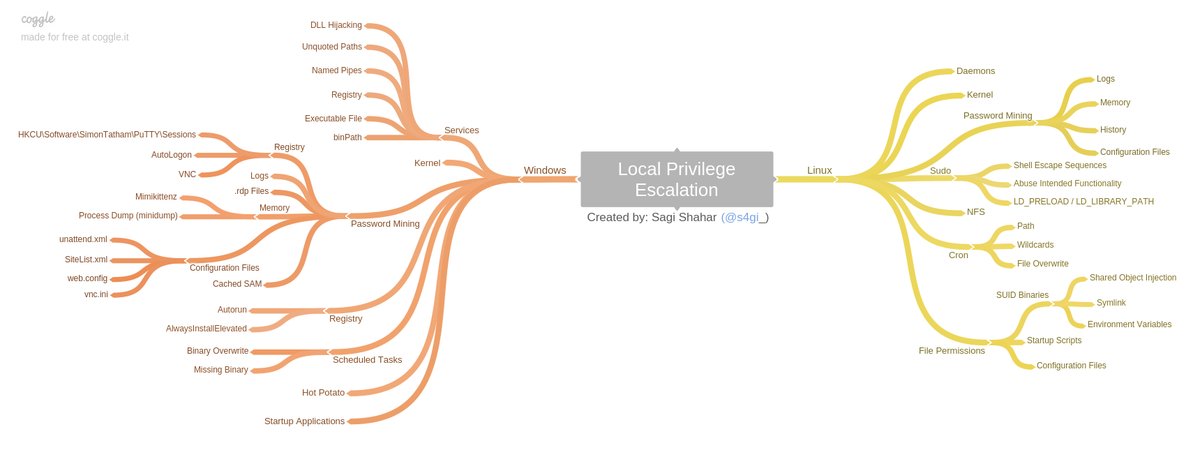
Enjoy ;)
Interesting projects
Top Related Projects
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Scripted Local Linux Enumeration & Privilege Escalation Checks
A tool designed to exploit a privilege escalation vulnerability in the sudo program on Unix-like systems. It takes advantage of a specific misconfiguration or flaw in sudo to gain elevated privileges on the system, essentially allowing a regular user to execute commands as the root user.
Linux privilege escalation auditing tool
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot