 AndroBugs_Framework
AndroBugs_Framework
AndroBugs Framework is an efficient Android vulnerability scanner that helps developers or hackers find potential security vulnerabilities in Android applications. No need to install on Windows.
Top Related Projects
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
Tool to look for several security related Android application vulnerabilities
A collection of android security related resources
The OWASP Mobile Application Security Testing Guide (MASTG) is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the OWASP Mobile Security Weakness Enumeration (MASWE) weaknesses, which are in alignment with the OWASP MASVS.
Android Vulnerability Test Suite - In the spirit of open data collection, and with the help of the community, let's take a pulse on the state of Android security. NowSecure presents an on-device app to test for recent device vulnerabilities.
Quick Overview
AndroBugs Framework is an Android vulnerability scanner designed to help developers and security researchers identify potential security issues in Android applications. It performs static analysis on APK files, checking for common vulnerabilities and misconfigurations in Android apps.
Pros
- Comprehensive vulnerability scanning for Android applications
- Easy to use with both command-line interface and GUI options
- Regularly updated to include new vulnerability checks
- Generates detailed reports in various formats (e.g., HTML, JSON)
Cons
- May produce false positives that require manual verification
- Limited documentation for advanced usage and customization
- Requires some technical knowledge to interpret results effectively
- Performance can be slow for large APK files
Getting Started
To get started with AndroBugs Framework:
-
Clone the repository:
git clone https://github.com/AndroBugs/AndroBugs_Framework.git -
Install dependencies:
pip install -r requirements.txt -
Run a basic scan:
python androbugs.py -f path/to/your/app.apk -
View the generated report in the
reportsdirectory.
For more advanced usage and options, refer to the project's documentation on GitHub.
Competitor Comparisons
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
Pros of Mobile-Security-Framework-MobSF
- More comprehensive analysis, covering both Android and iOS applications
- Active development with frequent updates and a larger community
- User-friendly web interface for easier interaction and result visualization
Cons of Mobile-Security-Framework-MobSF
- Requires more system resources due to its extensive features
- Steeper learning curve for new users compared to AndroBugs Framework
- May produce more false positives in certain scenarios
Code Comparison
AndroBugs Framework:
def analyze_apk(apk_file):
a = APK(apk_file)
d = DalvikVMFormat(a.get_dex())
dx = VMAnalysis(d)
# ... (analysis logic)
Mobile-Security-Framework-MobSF:
def scan_file(file_type, file_name, rescan):
# ... (setup and initialization)
if file_type == "apk":
apk_analysis = StaticAnalyzer.analyze_android(app_dict)
elif file_type == "ipa":
ios_analysis = StaticAnalyzer.analyze_ios(app_dict)
# ... (additional analysis and reporting)
The code snippets show that MobSF supports multiple file types and platforms, while AndroBugs focuses specifically on Android APK analysis. MobSF's structure allows for easier extension to support additional file types and analysis methods.
Tool to look for several security related Android application vulnerabilities
Pros of QARK
- More active development and maintenance
- Broader scope of vulnerability detection, including network security issues
- Better documentation and user guides
Cons of QARK
- Slower analysis compared to AndroBugs Framework
- Higher false positive rate in some cases
- More complex setup process
Code Comparison
QARK example:
def __init__(self):
self.name = 'Intent Spoofing'
self.vulnerability = 'Malicious apps may be able to read or modify this app\'s data'
self.severity = Severity.WARNING
AndroBugs Framework example:
def __init__(self):
self.name = "Intent Spoofing"
self.description = "Potential Intent Spoofing vulnerability detected"
self.severity = "Medium"
Both tools use similar structures for defining vulnerability checks, but QARK provides more detailed information and uses an enumeration for severity levels.
A collection of android security related resources
Pros of android-security-awesome
- Comprehensive collection of Android security resources, tools, and articles
- Regularly updated with new content and community contributions
- Well-organized structure with clear categorization of different security aspects
Cons of android-security-awesome
- Not a standalone tool, primarily serves as a curated list of resources
- Requires users to explore and evaluate individual tools for their specific needs
- May overwhelm beginners with the sheer volume of information
Code comparison
AndroBugs_Framework:
def analyze_apk(apk_file, output_dir, with_html_report=False):
# Perform APK analysis
# Generate reports
android-security-awesome:
## Tools
- [Androguard](https://github.com/androguard/androguard) - Reverse engineering and analysis of Android applications
- [MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF) - Mobile Security Framework for automated pentesting
AndroBugs_Framework is a standalone tool for Android app security analysis, while android-security-awesome is a curated list of resources. The former provides direct functionality for analyzing APKs, whereas the latter offers links to various tools and articles. AndroBugs_Framework is more focused but limited in scope, while android-security-awesome covers a broader range of Android security topics but requires users to explore individual resources.
The OWASP Mobile Application Security Testing Guide (MASTG) is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the OWASP Mobile Security Weakness Enumeration (MASWE) weaknesses, which are in alignment with the OWASP MASVS.
Pros of mastg
- Comprehensive guide covering mobile app security testing and reverse engineering
- Regularly updated with contributions from the security community
- Provides detailed explanations and best practices for secure mobile development
Cons of mastg
- Not an automated tool, requires manual analysis and interpretation
- Steeper learning curve for beginners due to its extensive content
- May require additional tools for practical implementation of security tests
Code comparison
While a direct code comparison is not relevant in this case, we can compare the approach of both projects:
AndroBugs_Framework:
def analyze_apk(apk_file):
# Automated analysis of APK file
# ...
mastg:
## Testing Network Communication
1. Intercept network traffic
2. Analyze SSL/TLS implementation
3. Check for sensitive data leakage
AndroBugs_Framework is a Python-based tool for automated Android app security analysis, while mastg is a comprehensive guide in Markdown format covering various aspects of mobile app security testing and best practices.
Android Vulnerability Test Suite - In the spirit of open data collection, and with the help of the community, let's take a pulse on the state of Android security. NowSecure presents an on-device app to test for recent device vulnerabilities.
Pros of android-vts
- User-friendly mobile app interface for running vulnerability tests
- Regularly updated with new vulnerability checks
- Provides detailed explanations and references for each vulnerability
Cons of android-vts
- Limited to Android platform-specific vulnerabilities
- Requires installation on the target device
- May not cover as wide a range of security issues as AndroBugs_Framework
Code Comparison
AndroBugs_Framework:
def analyze_apk(apk_file, output_dir, extra_options):
# Perform static analysis on APK file
# Generate report based on findings
android-vts:
public class VulnerabilityTest {
public void runTest() {
// Execute vulnerability check
// Display results in app interface
}
}
The code snippets highlight the different approaches:
- AndroBugs_Framework focuses on static analysis of APK files
- android-vts implements individual vulnerability tests that run on the device
Both projects aim to identify Android vulnerabilities, but android-vts provides a more interactive, on-device experience, while AndroBugs_Framework offers broader static analysis capabilities.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
AndroBugs Framework
AndroBugs Framework is an Android vulnerability analysis system that helps developers or hackers find potential security vulnerabilities in Android applications. No splendid GUI interface, but the most efficient (less than 2 minutes per scan in average) and more accurate.
Version: 1.0.0
####Features:####
- Find security vulnerabilities in an Android app
- Check if the code is missing best practices
- Check dangerous shell commands (e.g. âsuâ)
- Collect Information from millions of apps
- Check the appâs security protection (marked as
<Hacker>, designed for app repackaging hacking)
##Author
- Yu-Cheng Lin (androbugs.framework at gmail.com, @AndroBugs)
Steup Steps and Usage for Windows
Easy to use for Android developers or hackers on Microsoft Windows: (a) No need to install Python 2.7 (b) No need to install any 3rd-party library (c) No need to install AndroBugs Framework
- mkdir C:\AndroBugs_Framework
- cd C:\AndroBugs_Framework
- Unzip the latest Windows version of AndroBugs Framework from Windows releases
- Go to Computer->System Properties->Advanced->Environment Variables. Add "C:\AndroBugs_Framework" to the "Path" variable
androbugs.exe -handrobugs.exe -f [APK file]
Massive Analysis Tool Steup Steps and Usage for Windows
- Complete the Steup Steps and Usage for Windows first
- Install the Windows version of MongoDB (https://www.mongodb.org/downloads)
- Install PyMongo library
- Config your own MongoDB settings: C:\AndroBugs_Framework\androbugs-db.cfg
- Choose your preferred MongoDB management tool (http://mongodb-tools.com/)
AndroBugs_MassiveAnalysis.exe -h
- Example:
AndroBugs_MassiveAnalysis.exe -b 20151112 -t BlackHat -d .\All_Your_Apps\ -o .\Massive_Analysis_Reports
AndroBugs_ReportByVectorKey.exe -h
- Example:
AndroBugs_ReportByVectorKey.exe -v WEBVIEW_RCE -l Critical -b 20151112 -t BlackHat
Usage for Unix/Linux
####To run the AndroBugs Framework:####
python androbugs.py -f [APK file]
####To check the usage:####
python androbugs.py -h
Usage of Massive Analysis Tools for Unix/Linux
Prerequisite: Setup MongoDB and config your own MongoDB settings in "androbugs-db.cfg"
####To run the massive analysis for AndroBugs Framework:####
python AndroBugs_MassiveAnalysis.py -b [Your_Analysis_Number] -t [Your_Analysis_Tag] -d [APKs input directory] -o [Report output directory]
Example:
python AndroBugs_MassiveAnalysis.py -b 20151112 -t BlackHat -d ~/All_Your_Apps/ -o ~/Massive_Analysis_Reports
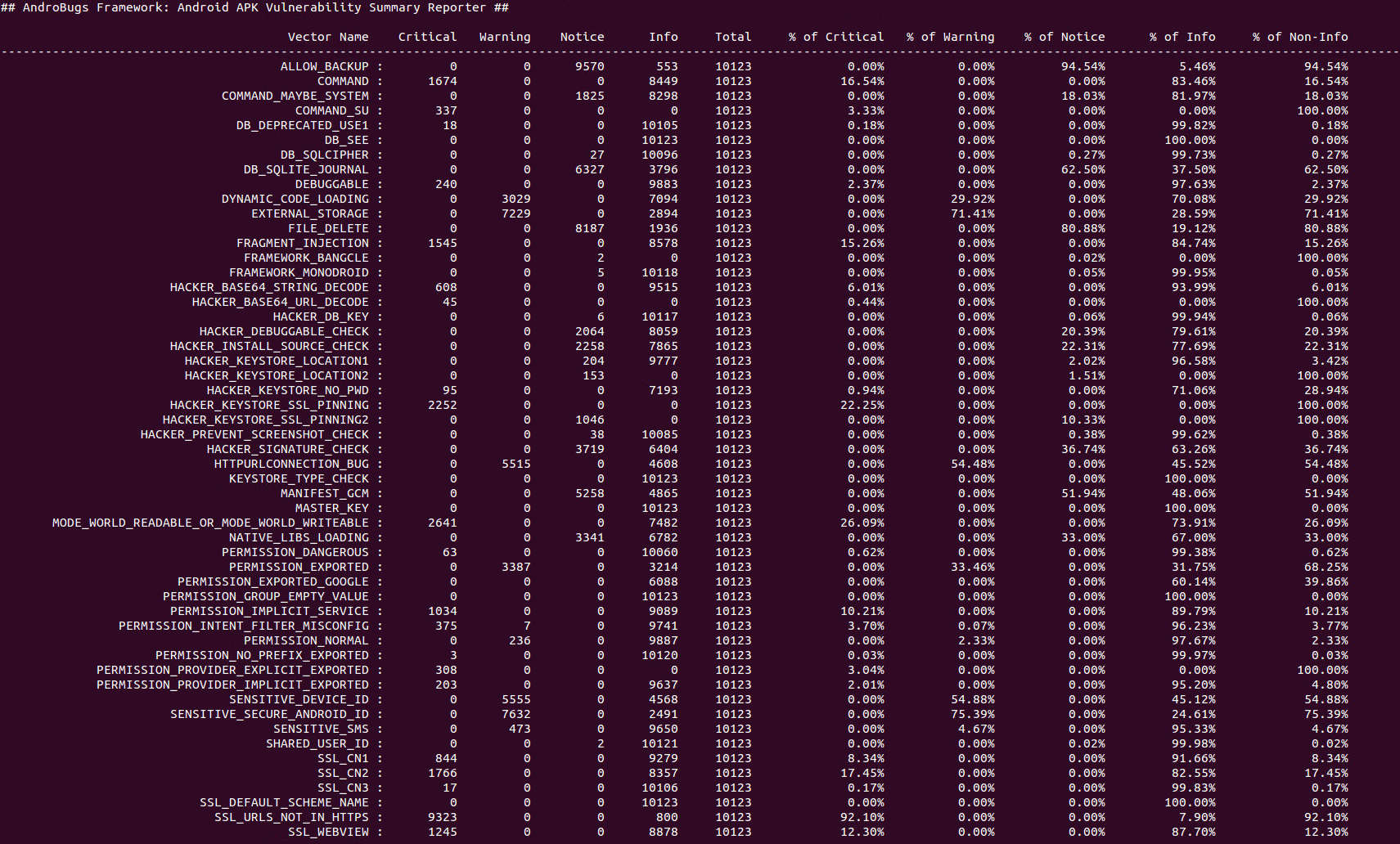
####To get the summary report and all the vectors of massive analysis:####
python AndroBugs_ReportSummary.py -m massive -b [Your_Analysis_Number] -t [Your_Analysis_Tag]
Example:
python AndroBugs_ReportSummary.py -m massive -b 20151112 -t BlackHat
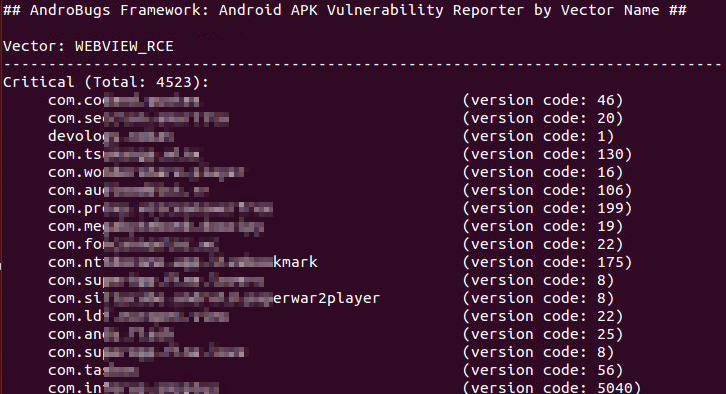
####To list the potentially vulnerable apps by Vector ID and Severity Level (Log Level):####
python AndroBugs_ReportByVectorKey.py -v [Vector ID] -l [Log Level] -b [Your_Analysis_Number] -t [Your_Analysis_Tag]
python AndroBugs_ReportByVectorKey.py -v [Vector ID] -l [Log Level] -b [Your_Analysis_Number] -t [Your_Analysis_Tag] -a
Example:
python AndroBugs_ReportByVectorKey.py -v WEBVIEW_RCE -l Critical -b 20151112 -t BlackHat
python AndroBugs_ReportByVectorKey.py -v WEBVIEW_RCE -l Critical -b 20151112 -t BlackHat -a
##Requirements
- Python 2.7.x (DO NOT USE Python 3.X)
- PyMongo library (If you want to use the massive analysis tool)
##Licenses
- AndroBugs Framework is under the license of GNU GPL v3.0
Top Related Projects
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
Tool to look for several security related Android application vulnerabilities
A collection of android security related resources
The OWASP Mobile Application Security Testing Guide (MASTG) is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the OWASP Mobile Security Weakness Enumeration (MASWE) weaknesses, which are in alignment with the OWASP MASVS.
Android Vulnerability Test Suite - In the spirit of open data collection, and with the help of the community, let's take a pulse on the state of Android security. NowSecure presents an on-device app to test for recent device vulnerabilities.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot