Top Related Projects
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
An automated phishing tool with 30+ templates. This Tool is made for educational purpose only ! Author will not be responsible for any misuse of this toolkit !
Introducing "URL Making Technology" to the world for the very FIRST TIME. Give a Mask to Phishing URL like a PRO.. A MUST have tool for Phishing.
Open-Source Phishing Toolkit
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Quick Overview
SocialFish is an educational tool designed to demonstrate the risks of phishing attacks. It creates fake login pages that mimic popular social media platforms and websites, capturing entered credentials for educational purposes. The project aims to raise awareness about online security and the importance of verifying website authenticity.
Pros
- Provides a hands-on learning experience for cybersecurity education
- Supports multiple templates for various popular websites
- Includes both command-line and graphical user interfaces
- Regularly updated to maintain effectiveness and relevance
Cons
- Can be misused for malicious purposes if not handled responsibly
- Requires careful legal and ethical considerations before use
- May not accurately represent all aspects of real-world phishing attacks
- Limited to specific pre-defined templates
Getting Started
To set up and run SocialFish:
-
Clone the repository:
git clone https://github.com/UndeadSec/SocialFish.git -
Navigate to the project directory:
cd SocialFish -
Install dependencies:
pip3 install -r requirements.txt -
Run the tool:
python3 SocialFish.py -
Follow the on-screen prompts to select a template and start the phishing simulation.
Note: Always use this tool responsibly and only in controlled, authorized environments for educational purposes. Ensure you have proper permissions and comply with all relevant laws and regulations.
Competitor Comparisons
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Pros of social-engineer-toolkit
- More comprehensive toolkit with a wider range of social engineering attacks
- Actively maintained with regular updates and contributions
- Extensive documentation and community support
Cons of social-engineer-toolkit
- Steeper learning curve due to its complexity
- Requires more setup and dependencies
- May be overkill for simple phishing campaigns
Code Comparison
SocialFish (Python):
def runPhishing(social, custom):
system('rm -Rf base/Server/www/*.* && touch base/Server/www/index.html')
if social == "Facebook":
system('cp base/WebPages/fb_standard/*.* base/Server/www/')
if custom == True:
print(cyan("\n[*] Custom server"))
social-engineer-toolkit (Python):
def site_cloner(website, exportpath, *args):
grab_ipaddress()
ipaddr = grab_ipaddress()
filewrite = open(setdir + "/ipaddr.txt", "w")
filewrite.write(ipaddr)
filewrite.close()
subprocess.Popen("wget -c -r -l1 -O " + setdir + "/web_clone/index.html --no-check-certificate " + website, stdout=subprocess.PIPE, stderr=subprocess.PIPE, shell=True).wait()
Both tools use Python for their core functionality, but social-engineer-toolkit offers more advanced features and a broader scope of social engineering techniques.
An automated phishing tool with 30+ templates. This Tool is made for educational purpose only ! Author will not be responsible for any misuse of this toolkit !
Pros of zphisher
- More frequent updates and active development
- Supports a wider range of phishing templates (30+)
- Includes built-in tunneling options (Cloudflared, Ngrok)
Cons of zphisher
- Less focus on social engineering aspects
- May require more manual setup for some features
- Potentially less stable due to rapid development
Code Comparison
SocialFish:
def runPhishing(social, custom):
system('rm -Rf base/Server/www/*.* && touch base/Server/www/index.html')
if social == "Facebook":
system('cp base/WebPages/fb_standard/*.* base/Server/www/')
if custom == True:
print(cyan("\n[*] Custom Folder found. Please note that you need to have index.html in your "
"folder!"))
zphisher:
tunnel_menu() {
if [[ -e ".cld.log" ]]; then
rm -rf ".cld.log"
fi
printf "\n${RED}[${WHITE}-${RED}]${GREEN} Select a Port Forwarding Service:\n"
printf "\n${RED}[${WHITE}01${RED}]${ORANGE} Localhost ${RED}[${CYAN}For Developers${RED}]"
printf "\n${RED}[${WHITE}02${RED}]${ORANGE} Ngrok.io ${RED}[${CYAN}Best${RED}]"
printf "\n${RED}[${WHITE}03${RED}]${ORANGE} Cloudflared ${RED}[${CYAN}New${RED}]"
printf "\n"
read -p "${RED}[${WHITE}-${RED}]${GREEN} Select a Port Forwarding Service: ${BLUE}"
Both repositories focus on creating phishing pages, but their implementations differ. SocialFish uses Python and emphasizes social engineering, while zphisher is written in Bash and offers more templates and tunneling options. The code snippets show these differences in approach and functionality.
Introducing "URL Making Technology" to the world for the very FIRST TIME. Give a Mask to Phishing URL like a PRO.. A MUST have tool for Phishing.
Pros of maskphish
- Simpler and more lightweight tool focused specifically on URL masking
- Easier to set up and use for quick phishing campaigns
- Generates masked links that can be shared directly
Cons of maskphish
- Less comprehensive feature set compared to SocialFish
- Lacks advanced customization options for phishing pages
- No built-in support for capturing and storing credentials
Code comparison
maskphish:
url_checker() {
if [ ! "${1//:*}" = http ]; then
if [ ! "${1//:*}" = https ]; then
echo -e "\e[31m[!] Invalid URL. Please use http or https.\e[0m"
exit 1
fi
fi
}
SocialFish:
def runPhishing(social, custom):
system('rm -Rf base/Server/www/*.* && touch base/Server/www/index.html')
if social == "custom":
print(custom)
system('cp base/WebPages/custom/* base/Server/www/')
else:
system('cp base/WebPages/%s/* base/Server/www/' % social)
The code snippets show that maskphish focuses on URL validation, while SocialFish handles phishing page setup and customization. This reflects the different scopes and approaches of the two tools.
Open-Source Phishing Toolkit
Pros of Gophish
- More comprehensive and feature-rich phishing simulation platform
- Better suited for enterprise-level security testing and training
- Actively maintained with regular updates and a larger community
Cons of Gophish
- Steeper learning curve due to more complex setup and configuration
- Requires more resources to run and manage effectively
- Less focused on social media phishing compared to SocialFish
Code Comparison
SocialFish (Python):
def runPhishing(social, custom):
system('rm -Rf base/Server/www/*.* && touch base/Server/www/index.html')
if social == "Facebook":
system('cp base/WebPages/fb_standard/*.* base/Server/www/')
if custom == True:
print(custom_folder)
Gophish (Go):
func (s *Server) handleLanding(w http.ResponseWriter, r *http.Request) {
ps := struct {
Title string
Org string
Custom interface{}
URL string
Redirect string
}{Title: "Landing Page", Org: "Gophish", URL: r.URL.String()}
getTemplate(w, "landing").Execute(w, ps)
}
The code snippets show that SocialFish focuses on specific social media platforms, while Gophish provides a more generalized approach to creating phishing campaigns. Gophish's code demonstrates its flexibility in handling various landing page scenarios.
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Pros of evilginx2
- More advanced and feature-rich phishing framework
- Supports multiple phishing scenarios and customizable templates
- Capable of bypassing two-factor authentication (2FA)
Cons of evilginx2
- Steeper learning curve and more complex setup
- Requires more technical knowledge to operate effectively
- May be overkill for simpler phishing campaigns
Code Comparison
SocialFish (Python):
def runPhishing(social, custom):
system('sudo docker-compose up -d')
if social:
system('sudo docker-compose exec socialfish python3 SocialFish.py ' + social)
elif custom:
system('sudo docker-compose exec socialfish python3 SocialFish.py custom')
evilginx2 (Go):
func (p *Phishlet) GetLureUrls(domain string) ([]string, error) {
var ret []string
for _, au := range p.authUrls {
ret = append(ret, "https://"+domain+au)
}
return ret, nil
}
SocialFish is simpler and easier to use, focusing on social media phishing. evilginx2 offers more advanced features and flexibility but requires more expertise. SocialFish uses Python and Docker, while evilginx2 is written in Go. evilginx2's code demonstrates its capability to handle multiple phishing scenarios, whereas SocialFish's code shows a more straightforward approach to launching phishing campaigns.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

SocialFish
Are you looking for SF's mobile controller? UndeadSec/SocialFishMobile
Are you looking for SF's old version(Ngrok integrated) ? UndeadSec/SociaFish/.../sharkNet
SETUP AND RUNNING
Visit the wiki for more details.
Setup instructions here.
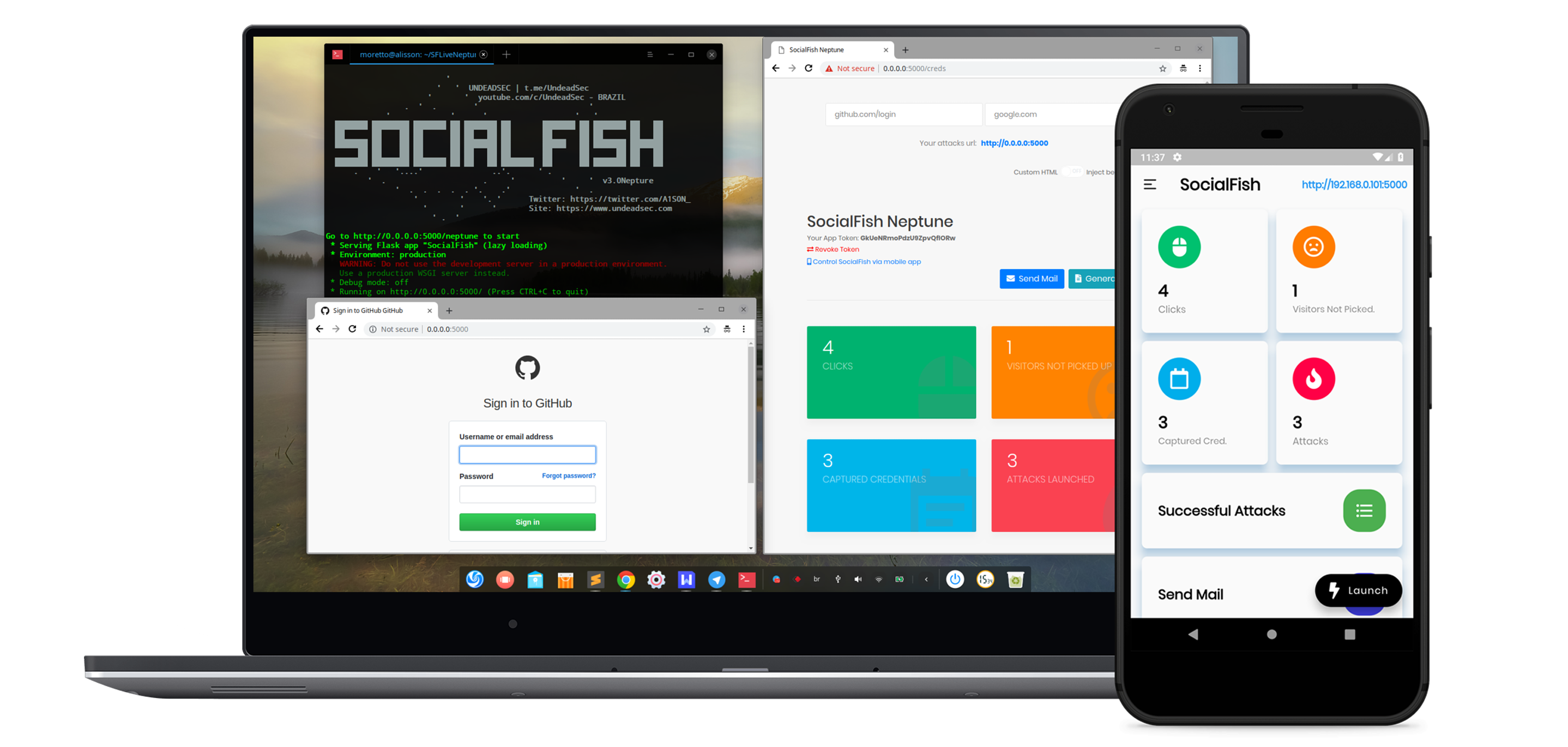
MAINTAINERS
- Alisson Moretto, Twitter: @UndeadSec, GitHub: @UndeadSec
- Vandré Augusto, Twitter: @dr1nKoRdi3, GitHub: @dr1nK0Rdi3
DOCS
- Fernando Bellincanta, Twitter: @ErvalhouS, GitHub: @ErvalhouS
DISCLAIMER
TO BE USED FOR EDUCATIONAL PURPOSES ONLY
The use of the SocialFish is COMPLETE RESPONSIBILITY of the END-USER. Developers assume NO liability and are NOT responsible for any misuse or damage caused by this program.
"DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE." Taken from LICENSE.
Build
Docker
How to run with Docker?
You need to run:
docker compose up
CONTRIBUTING
We encourage you to contribute to SocialFish! Please check out the Contributing to SocialFish guide for guidelines about how to proceed. Join us!
CONTRIBUTOR CODE OF CONDUCT
This project adheres to No Code of Conduct. We are all adults. We accept anyone's contributions. Nothing else matters.
For more information please visit the No Code of Conduct homepage.
Top Related Projects
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
An automated phishing tool with 30+ templates. This Tool is made for educational purpose only ! Author will not be responsible for any misuse of this toolkit !
Introducing "URL Making Technology" to the world for the very FIRST TIME. Give a Mask to Phishing URL like a PRO.. A MUST have tool for Phishing.
Open-Source Phishing Toolkit
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot