 cloudmapper
cloudmapper
CloudMapper helps you analyze your Amazon Web Services (AWS) environments.
Top Related Projects
Cartography is a Python tool that consolidates infrastructure assets and the relationships between them in an intuitive graph view powered by a Neo4j database.
Multi-Cloud Security Auditing Tool
Cloud Security Posture Management (CSPM)
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized report.
Prowler is the Open Cloud Security platform for AWS, Azure, GCP, Kubernetes, M365 and more. It helps for continuous monitoring, security assessments & audits, incident response, compliance, hardening and forensics readiness. Includes CIS, NIST 800, NIST CSF, CISA, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, ENS and more
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Quick Overview
CloudMapper is an open-source tool for analyzing AWS environments. It creates network diagrams of AWS accounts and can be used to search for potential misconfigurations and security risks. CloudMapper helps security professionals and cloud architects visualize and understand their AWS infrastructure.
Pros
- Provides visual representation of AWS environments, making it easier to understand complex infrastructures
- Helps identify security risks and misconfigurations in AWS accounts
- Supports multiple AWS accounts and regions
- Offers both command-line interface and web-based user interface
Cons
- Requires AWS credentials with read-only access, which may be a security concern for some organizations
- Limited to AWS environments only, not supporting other cloud providers
- May require significant setup time and effort for large, complex AWS infrastructures
- Visualization can become cluttered and hard to read for very large environments
Code Examples
CloudMapper is not primarily a code library, but a tool. However, here are some example commands for using CloudMapper:
# Generate AWS network data
python cloudmapper.py collect --account my_account
# Create a web-based network diagram
python cloudmapper.py webserver --account my_account
# Search for potential security issues
python cloudmapper.py audit --account my_account
# Generate a report of publicly accessible resources
python cloudmapper.py report --account my_account
Getting Started
To get started with CloudMapper:
-
Clone the repository:
git clone https://github.com/duo-labs/cloudmapper.git -
Install dependencies:
pip install -r requirements.txt -
Configure AWS credentials:
aws configure -
Run CloudMapper:
python cloudmapper.py collect --account your_account_name python cloudmapper.py webserver
This will collect data from your AWS account and start a local web server to view the network diagram.
Competitor Comparisons
Cartography is a Python tool that consolidates infrastructure assets and the relationships between them in an intuitive graph view powered by a Neo4j database.
Pros of Cartography
- Supports multiple cloud providers (AWS, GCP, Azure) and other data sources
- Provides a more comprehensive view of infrastructure relationships
- Offers a Neo4j graph database for advanced querying and visualization
Cons of Cartography
- Requires more setup and infrastructure (Neo4j database)
- Steeper learning curve due to its broader scope and capabilities
- May be overkill for smaller environments or specific AWS-focused use cases
Code Comparison
CloudMapper:
def parse_arguments():
parser = argparse.ArgumentParser()
parser.add_argument("--config", help="Config file name", default="config.json")
parser.add_argument("--account", help="Account to collect from", required=True)
parser.add_argument("--regions", help="Regions to restrict to (ex. us-east-1,us-west-2)")
return parser.parse_args()
Cartography:
def sync(neo4j_session, config, stats):
common_job_parameters = {
'UPDATE_TAG': config.update_tag,
'permission_relationships_only': config.permission_relationships_only,
}
try:
aws_sync.run(neo4j_session, config.accounts, config.regions, common_job_parameters)
except ClientError as e:
logger.debug("Error occurred in AWS sync.", exc_info=True)
Both projects aim to map cloud infrastructure, but Cartography offers a more extensive and flexible approach at the cost of increased complexity.
Multi-Cloud Security Auditing Tool
Pros of ScoutSuite
- Supports multiple cloud providers (AWS, Azure, GCP, Alibaba Cloud, OCI)
- Provides a web-based interface for easy report viewing and navigation
- Offers customizable rulesets for tailored security assessments
Cons of ScoutSuite
- May have a steeper learning curve due to its broader scope
- Potentially slower execution time when scanning multiple cloud providers
- Less focus on network visualization compared to CloudMapper
Code Comparison
ScoutSuite (Python):
from ScoutSuite.core.cli_parser import ScoutSuiteArgumentParser
from ScoutSuite.core.console_manager import ConsoleManager
from ScoutSuite.core.exceptions import RuleExceptions
from ScoutSuite.core.processingengine import ProcessingEngine
from ScoutSuite.core.ruleset import Ruleset
CloudMapper (Python):
from cloudmapper.webserver import run_webserver
from cloudmapper.prepare import prepare
from cloudmapper.gather import gather
from cloudmapper.find_risks import find_risks
from cloudmapper.report import report
Both tools are written in Python and focus on cloud security assessment. ScoutSuite offers a more comprehensive approach with multi-cloud support, while CloudMapper specializes in AWS environments with a strong emphasis on network visualization. ScoutSuite's code structure reflects its modular design for handling multiple cloud providers, whereas CloudMapper's code is more focused on specific AWS-related tasks.
Cloud Security Posture Management (CSPM)
Pros of CloudSploit
- Supports multiple cloud providers (AWS, Azure, GCP, Oracle)
- Offers a wider range of security checks and compliance frameworks
- Provides a web-based interface for easier visualization and management
Cons of CloudSploit
- Less focus on network visualization compared to CloudMapper
- May require more setup and configuration for advanced features
- Potentially steeper learning curve for users new to cloud security
Code Comparison
CloudMapper example (Python):
from cloudmapper.nodes import Account, Region
from cloudmapper.prepare import build_data_structure
account = Account(None, 'demo')
region = Region(account, 'us-west-2')
build_data_structure(account, region, {})
CloudSploit example (JavaScript):
const CloudConfig = require('./helpers/aws');
const scanner = require('./helpers/scanner');
const config = new CloudConfig();
scanner(config, (err, results) => {
console.log(JSON.stringify(results, null, 2));
});
Both tools offer valuable insights into cloud infrastructure security, but they have different strengths. CloudMapper excels in network visualization and AWS-specific analysis, while CloudSploit provides a broader range of checks across multiple cloud providers. The choice between them depends on your specific needs and the cloud environments you're working with.
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized report.
Pros of Cloudsplaining
- Focused specifically on IAM policy analysis and visualization
- Generates HTML reports for easy sharing and viewing
- Lightweight and easy to install via pip
Cons of Cloudsplaining
- Limited to IAM policy analysis, lacks broader AWS infrastructure mapping
- Does not provide real-time monitoring or continuous assessment capabilities
Code Comparison
Cloudsplaining:
from cloudsplaining.scan.policy_document import PolicyDocument
policy = PolicyDocument(policy_dict)
results = policy.analyze()
CloudMapper:
from cloudmapper.nodes import Account, Region
account = Account(None, "demo")
region = Region(account, "us-west-2")
region.get_vpcs()
CloudMapper offers a more comprehensive approach to AWS infrastructure analysis, including network mapping and security group visualization. It provides a broader view of the AWS environment but may require more setup and resources.
Cloudsplaining, on the other hand, specializes in IAM policy analysis, offering detailed insights into permissions and potential security risks. It's more focused but lacks the wider scope of CloudMapper.
Both tools serve different purposes within AWS security analysis. CloudMapper is better suited for overall infrastructure assessment, while Cloudsplaining excels at in-depth IAM policy evaluation.
Prowler is the Open Cloud Security platform for AWS, Azure, GCP, Kubernetes, M365 and more. It helps for continuous monitoring, security assessments & audits, incident response, compliance, hardening and forensics readiness. Includes CIS, NIST 800, NIST CSF, CISA, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, ENS and more
Pros of Prowler
- More comprehensive security assessment, covering over 200 checks across multiple AWS services
- Regularly updated with new checks and features, ensuring coverage of latest AWS security best practices
- Provides detailed reports in various formats (HTML, JSON, CSV) for easy analysis and integration
Cons of Prowler
- Primarily focused on AWS, while CloudMapper supports multi-cloud environments
- May require more setup and configuration for specific use cases
- Can be more resource-intensive due to its extensive checks
Code Comparison
Prowler (Python):
def check_cloudtrail_enabled(self):
regions = self.regions()
for region in regions:
trails = self.client('cloudtrail', region).describe_trails()
if not trails['trailList']:
self.add_issue(0, 'CloudTrail is not enabled', region)
CloudMapper (Python):
def get_ec2_instances(region):
ec2 = boto3.client('ec2', region_name=region)
instances = ec2.describe_instances()
return [i for r in instances['Reservations'] for i in r['Instances']]
Both tools use Python and AWS SDK (boto3) for interacting with AWS services. Prowler's code snippet shows a security check implementation, while CloudMapper's focuses on data collection for visualization.
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Pros of Checkov
- Supports multiple cloud providers (AWS, Azure, GCP) and IaC tools (Terraform, CloudFormation, Kubernetes)
- Offers a wide range of pre-built policies and custom policy creation
- Integrates easily with CI/CD pipelines and provides machine-readable output
Cons of Checkov
- Focuses primarily on static analysis, lacking the network visualization capabilities of CloudMapper
- May require more setup and configuration for complex environments
- Does not provide detailed AWS account inventory like CloudMapper
Code Comparison
CloudMapper example (Python):
from cloudmapper.nodes import Account, Region
from cloudmapper.query import query_aws
account = Account(None, 'demo')
region = Region(account, 'us-west-2')
query_aws(account, region)
Checkov example (CLI):
checkov -d /path/to/iac/code --framework terraform
CloudMapper is more focused on AWS-specific network mapping and visualization, while Checkov offers broader cloud security posture management across multiple providers and IaC tools. CloudMapper provides deeper AWS-specific insights, whereas Checkov excels in policy-based security checks and CI/CD integration.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
CloudMapper
Note the Network Visualization functionality (command prepare) is no longer maintained.
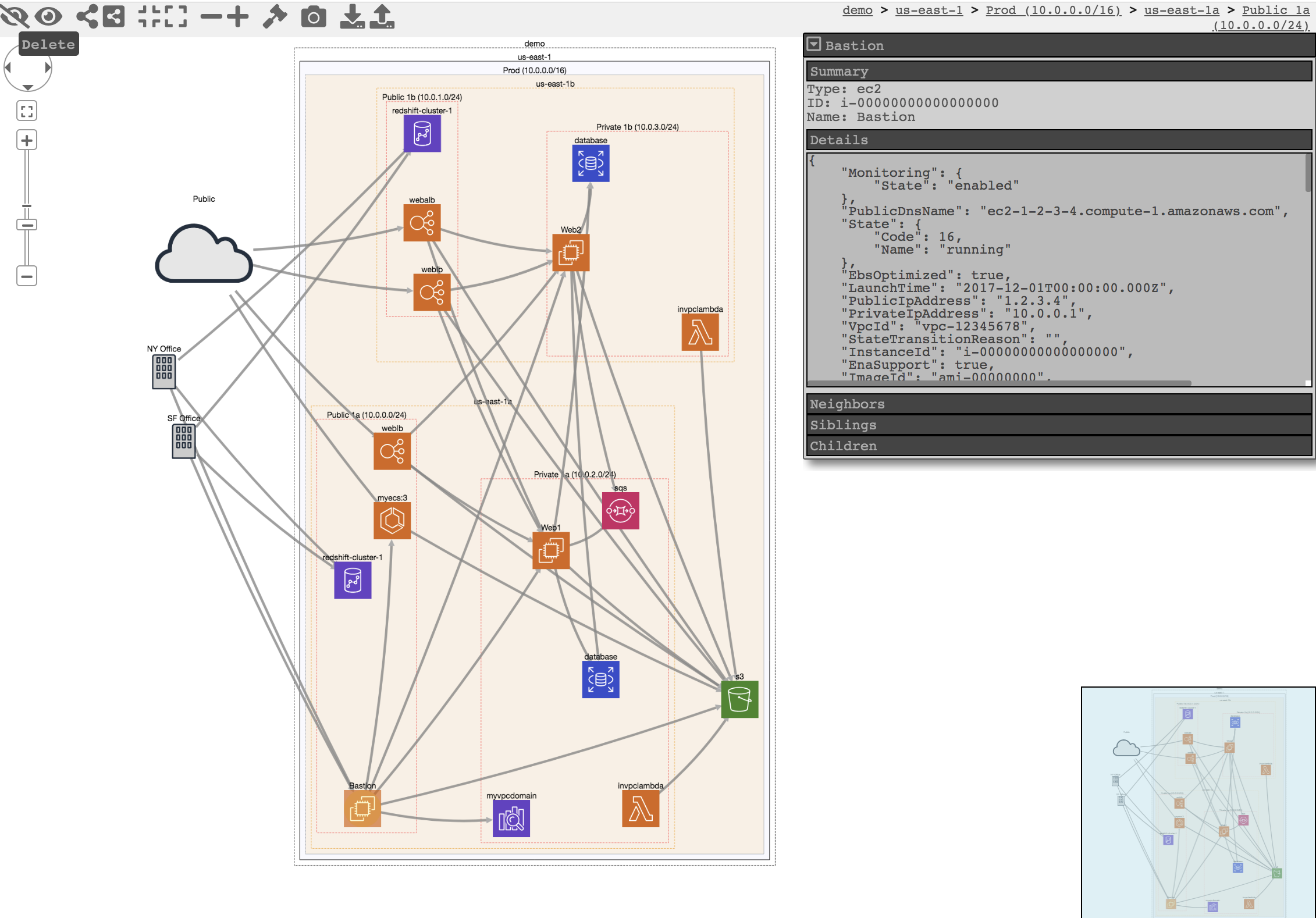
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your browser (functionality no longer maintained). It now contains much more functionality, including auditing for security issues.
- Network mapping demo
- Report demo
- Intro post
- Post to show spotting misconfigurations in networks
- Post on performing continuous auditing
Commands
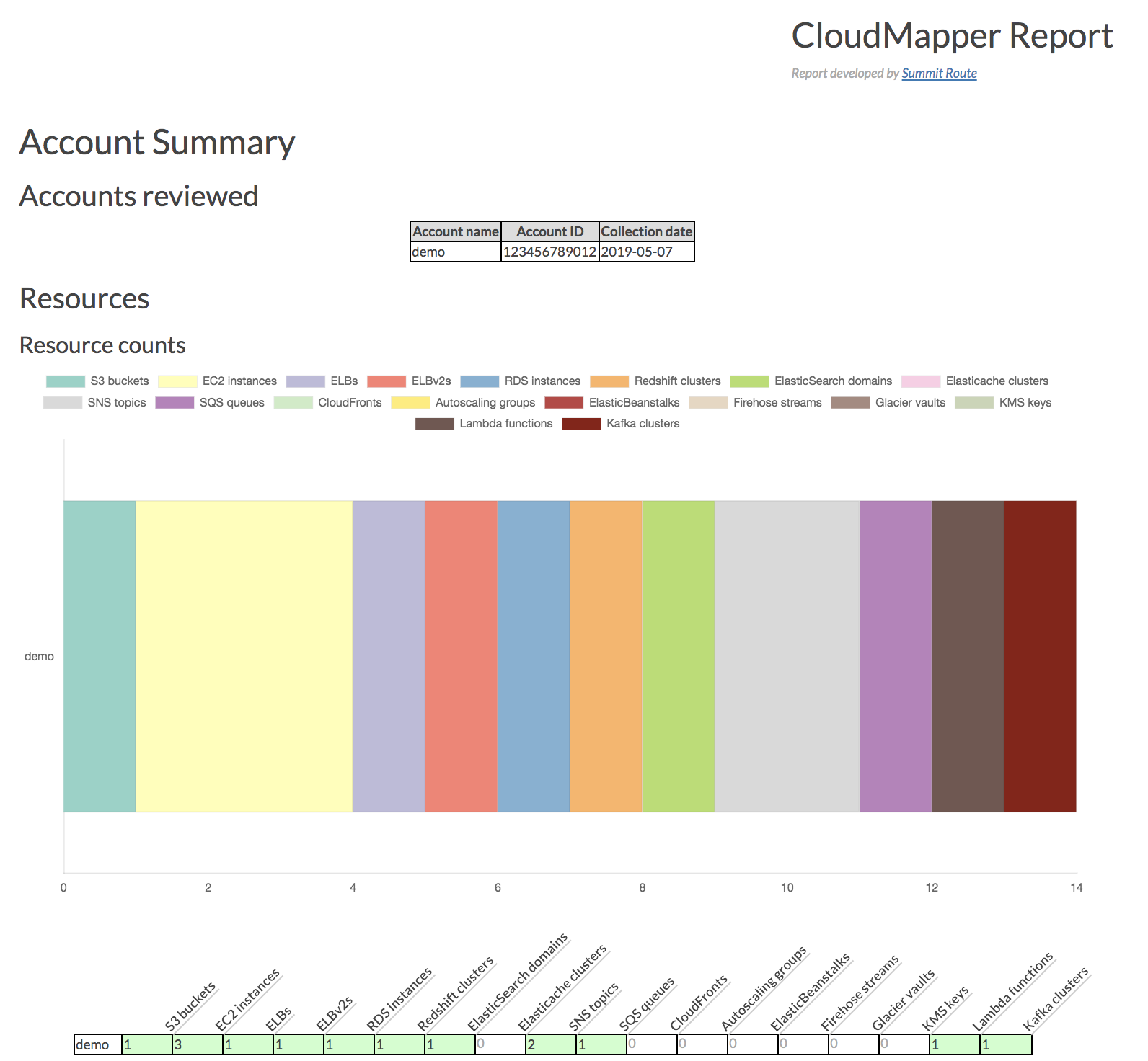
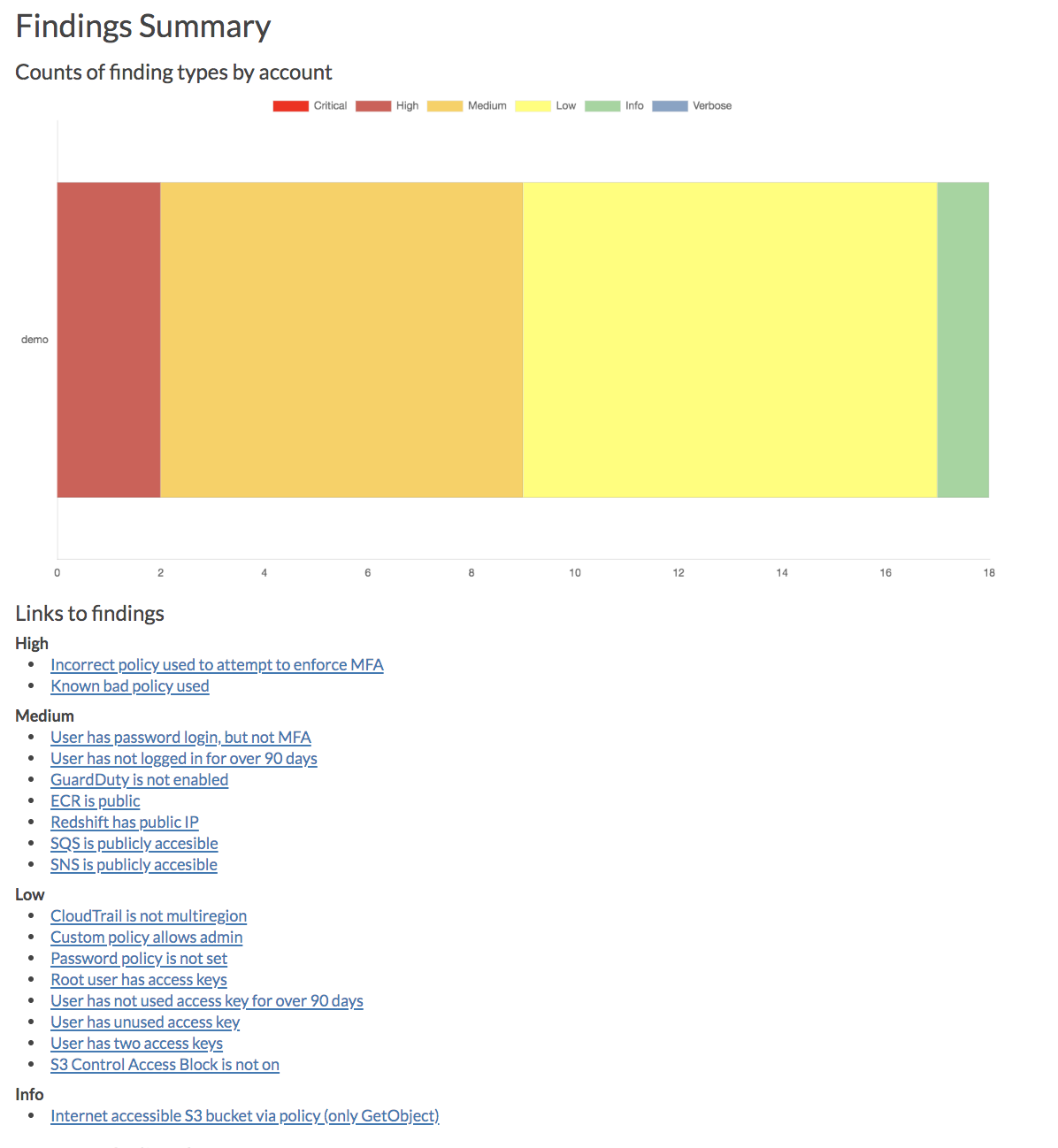
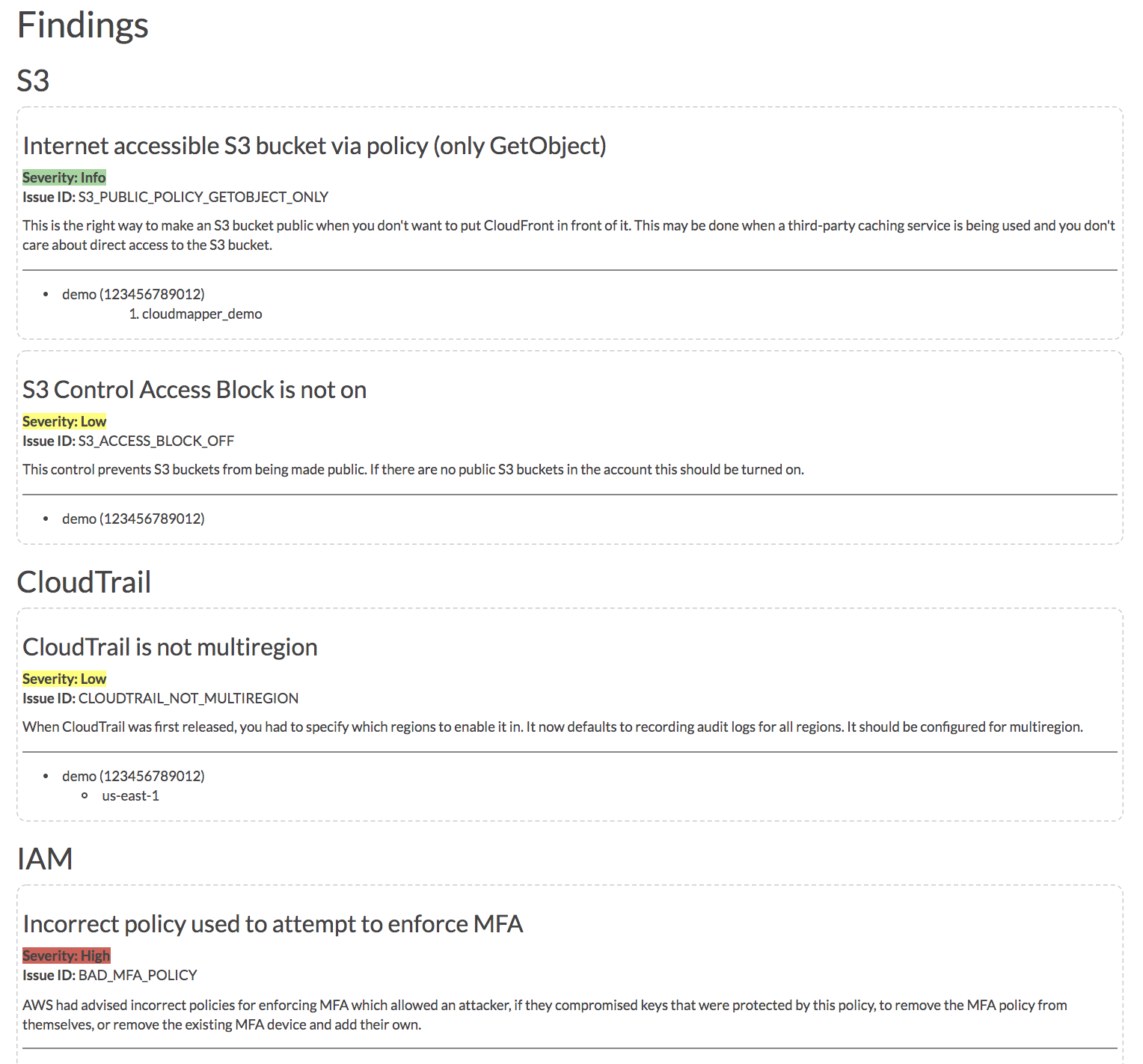
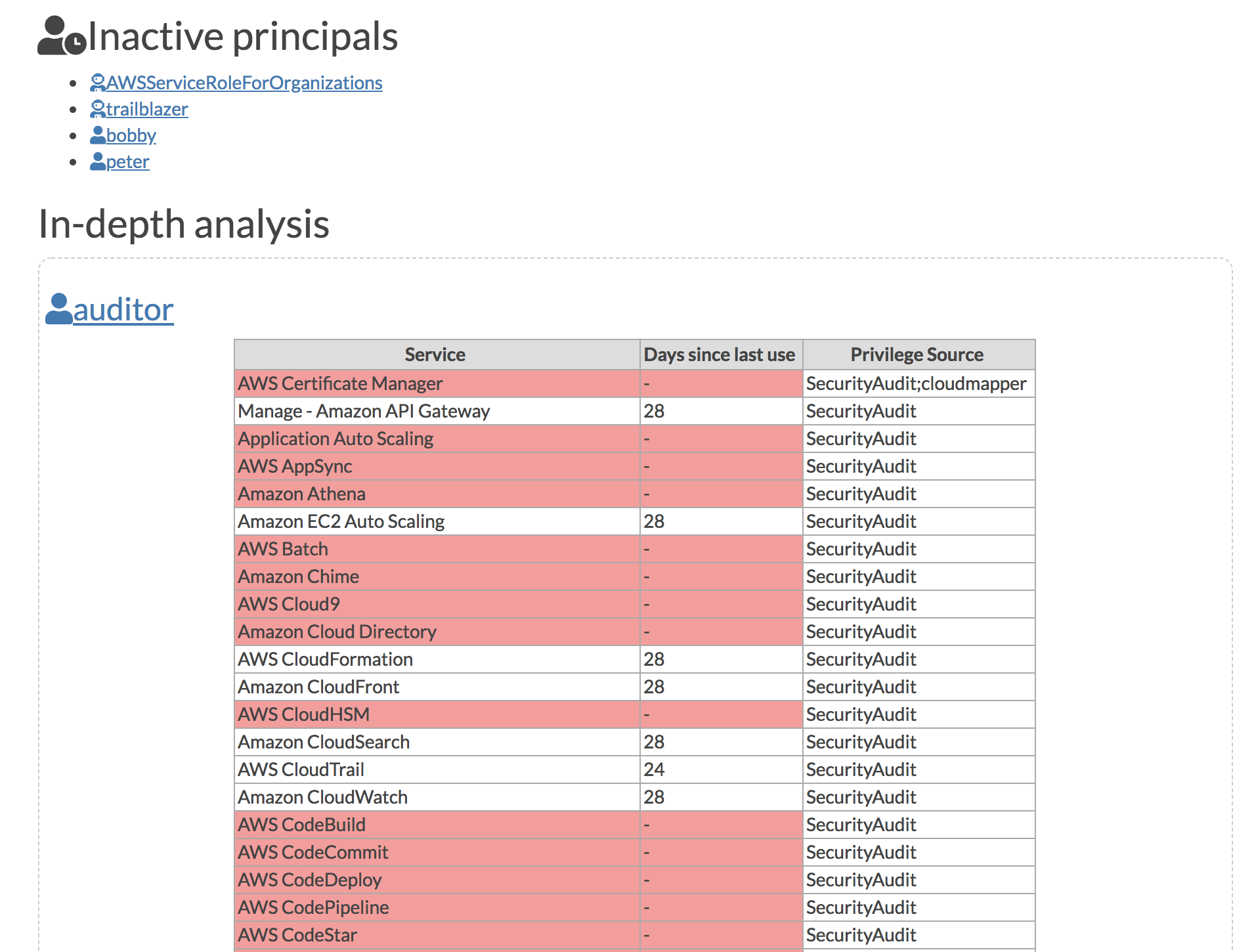
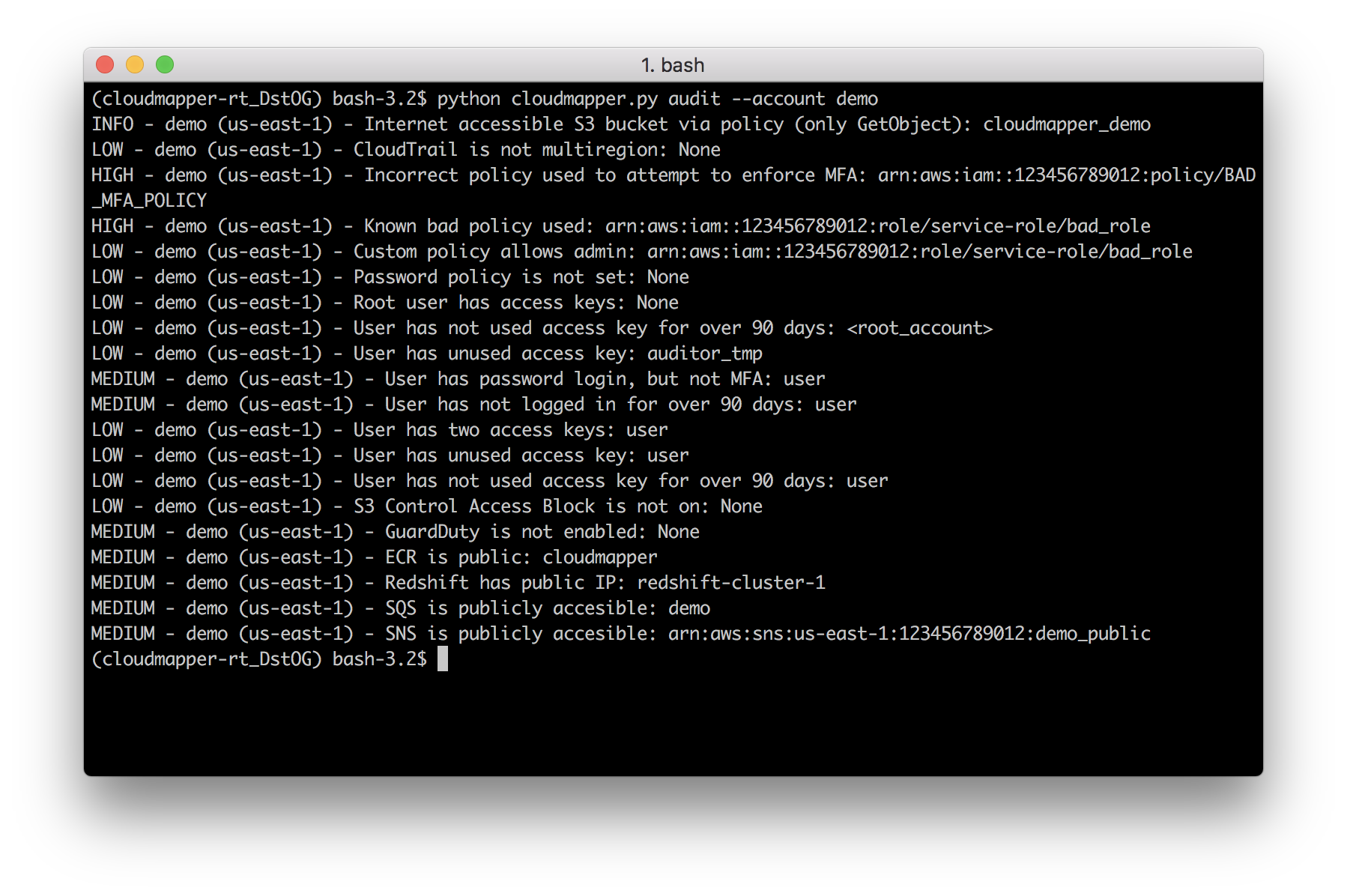
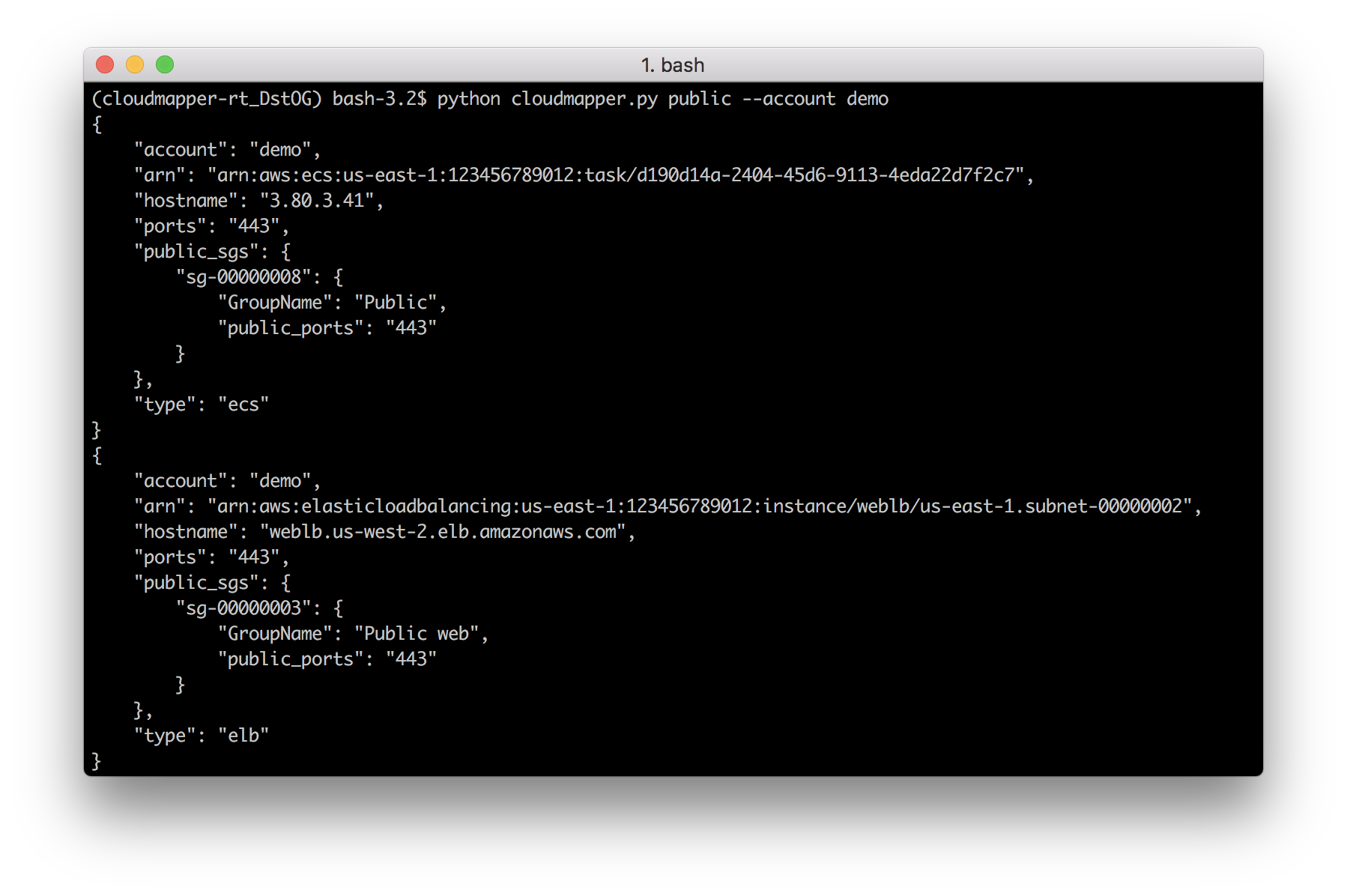
audit: Check for potential misconfigurations.collect: Collect metadata about an account. More details here.find_admins: Look at IAM policies to identify admin users and roles, or principals with specific privileges. More details here.find_unused: Look for unused resources in the account. Finds unused Security Groups, Elastic IPs, network interfaces, volumes and elastic load balancers.prepare/webserver: See Network Visualizationspublic: Find public hosts and port ranges. More details here.sg_ips: Get geoip info on CIDRs trusted in Security Groups. More details here.stats: Show counts of resources for accounts. More details here.weboftrust: Show Web Of Trust. More details here.report: Generate HTML report. Includes summary of the accounts and audit findings. More details here.iam_report: Generate HTML report for the IAM information of an account. More details here.
If you want to add your own private commands, you can create a private_commands directory and add them there.
Screenshots
| 
|
| 
|
| 
|
Installation
Requirements:
- python 3 (3.7.0rc1 is known to work),
pip, andvirtualenv - You will also need
jq(https://stedolan.github.io/jq/) and the librarypyjq(https://github.com/doloopwhile/pyjq), which require some additional tools installed that will be shown.
On macOS:
# clone the repo
git clone https://github.com/duo-labs/cloudmapper.git
# Install pre-reqs for pyjq
brew install autoconf automake awscli freetype jq libtool python3
cd cloudmapper/
python3 -m venv ./venv && source venv/bin/activate
pip install --prefer-binary -r requirements.txt
On Linux:
# clone the repo
git clone https://github.com/duo-labs/cloudmapper.git
# (AWS Linux, Centos, Fedora, RedHat etc.):
# sudo yum install autoconf automake libtool python3-devel.x86_64 python3-tkinter python-pip jq awscli
# (Debian, Ubuntu etc.):
# You may additionally need "build-essential"
sudo apt-get install autoconf automake libtool python3.7-dev python3-tk jq awscli
cd cloudmapper/
python3 -m venv ./venv && source venv/bin/activate
pip install -r requirements.txt
Run with demo data
A small set of demo data is provided. This will display the same environment as the demo site https://duo-labs.github.io/cloudmapper/
# Generate the data for the network map
python cloudmapper.py prepare --config config.json.demo --account demo
# Generate a report
python cloudmapper.py report --config config.json.demo --account demo
python cloudmapper.py webserver
This will run a local webserver at http://127.0.0.1:8000/ View the network map from that link, or view the report at http://127.0.0.1:8000/account-data/report.html
Setup
- Configure information about your account.
- Collect information about an AWS account.
1. Configure your account
Copy the config.json.demo to config.json and edit it to include your account ID and name (ex. "prod"), along with any external CIDR names. A CIDR is an IP range such as 1.2.3.4/32 which means only the IP 1.2.3.4.
2. Collect data about the account
This step uses the CLI to make describe and list calls and records the json in the folder specified by the account name under account-data.
AWS Privileges required
You must have AWS credentials configured that can be used by the CLI with read permissions for the different metadata to collect. I recommend using aws-vault. CloudMapper will collect IAM information, which means you MUST use MFA. Only the collect step requires AWS access.
You must have the following privileges (these grant various read access of metadata):
arn:aws:iam::aws:policy/SecurityAuditarn:aws:iam::aws:policy/job-function/ViewOnlyAccess
Collect the data
Collecting the data is done as follows:
python cloudmapper.py collect --account my_account
Analyze the data
From here, try running the different commands, such as:
python cloudmapper.py report --account my_account
python cloudmapper.py webserver
Then view the report in your browser at 127.0.0.1:8000/account-data/report.html
Further configuration
Generating a config file
Instead of modifying config.json directly, there is a command to configure the data there, in case that is needed:
python cloudmapper.py configure {add-account|remove-account} --config-file CONFIG_FILE --name NAME --id ID [--default DEFAULT]
python cloudmapper.py configure {add-cidr|remove-cidr} --config-file CONFIG_FILE --cidr CIDR --name NAME
This will allow you to define the different AWS accounts you use in your environment and the known CIDR IPs.
If you use AWS Organizations, you can also automatically add organization member accounts to config.json using:
python cloudmapper.py configure discover-organization-accounts
You need to be authenticated to the AWS CLI and have the permission organization:ListAccounts prior to running this command.
Using audit config overrides
You may find that you don't care about some of audit items. You may want to ignore the check entirely, or just specific resources. Copy config/audit_config_override.yaml.example to config/audit_config_override.yaml and edit the file based on the comments in there.
Using a Docker container
The docker container that is created is meant to be used interactively.
docker build -t cloudmapper .
Cloudmapper needs to make IAM calls and cannot use session credentials for collection, so you cannot use the aws-vault server if you want to collect data, and must pass role credentials in directly or configure aws credentials manually inside the container. The following code exposes your raw credentials inside the container.
(
export $(aws-vault exec YOUR_PROFILE --no-session -- env | grep ^AWS | xargs) && \
docker run -ti \
-e AWS_ACCESS_KEY_ID=$AWS_ACCESS_KEY_ID \
-e AWS_SECRET_ACCESS_KEY=$AWS_SECRET_ACCESS_KEY \
-p 8000:8000 \
cloudmapper /bin/bash
)
This will drop you into the container. Run aws sts get-caller-identity to confirm this was setup correctly. Cloudmapper demo data is not copied into the docker container so you will need to collect live data from your system. Note docker defaults may limit the memory available to your container. For example on Mac OS the default is 2GB which may not be enough to generate the report on a medium sized account.
python cloudmapper.py configure add-account --config-file config.json --name YOUR_ACCOUNT --id YOUR_ACCOUNT_NUMBER
python cloudmapper.py collect --account YOUR_ACCOUNT
python cloudmapper.py report --account YOUR_ACCOUNT
python cloudmapper.py prepare --account YOUR_ACCOUNT
python cloudmapper.py webserver --public
You should then be able to view the report by visiting http://127.0.0.1:8000/account-data/report.html
Running CloudMapper regularly to audit your environment
A CDK app for deploying CloudMapper via Fargate so that it runs nightly, sends audit findings as alerts to a Slack channel, and generating a report that is saved on S3, is described here.
Alternatives
For network diagrams, you may want to try https://github.com/lyft/cartography or https://github.com/anaynayak/aws-security-viz
For auditing and other AWS security tools see https://github.com/toniblyx/my-arsenal-of-aws-security-tools
Licenses
- cytoscape.js: MIT https://github.com/cytoscape/cytoscape.js/blob/master/LICENSE
- cytoscape.js-qtip: MIT https://github.com/cytoscape/cytoscape.js-qtip/blob/master/LICENSE
- cytoscape.js-grid-guide: MIT https://github.com/iVis-at-Bilkent/cytoscape.js-grid-guide
- cytoscape.js-panzoom: MIT https://github.com/cytoscape/cytoscape.js-panzoom/blob/master/LICENSE
- jquery: JS Foundation https://github.com/jquery/jquery/blob/master/LICENSE.txt
- jquery.qtip: MIT https://github.com/qTip2/qTip2/blob/master/LICENSE
- cytoscape-navigator: MIT https://github.com/cytoscape/cytoscape.js-navigator/blob/c249bd1551c8948613573b470b30a471def401c5/bower.json#L24
- cytoscape.js-autopan-on-drag: MIT https://github.com/iVis-at-Bilkent/cytoscape.js-autopan-on-drag
- font-awesome: MIT http://fontawesome.io/
- FileSave.js: MIT https://github.com/eligrey/FileSaver.js/blob/master/LICENSE.md
- circular-json: MIT https://github.com/WebReflection/circular-json/blob/master/LICENSE.txt
- rstacruz/nprogress: MIT https://github.com/rstacruz/nprogress/blob/master/License.md
- mousetrap: Apache https://github.com/ccampbell/mousetrap/blob/master/LICENSE
- akkordion MIT https://github.com/TrySound/akkordion/blob/master/LICENSE
Top Related Projects
Cartography is a Python tool that consolidates infrastructure assets and the relationships between them in an intuitive graph view powered by a Neo4j database.
Multi-Cloud Security Auditing Tool
Cloud Security Posture Management (CSPM)
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized report.
Prowler is the Open Cloud Security platform for AWS, Azure, GCP, Kubernetes, M365 and more. It helps for continuous monitoring, security assessments & audits, incident response, compliance, hardening and forensics readiness. Includes CIS, NIST 800, NIST CSF, CISA, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, ENS and more
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot