Top Related Projects
A Rust port of shadowsocks
A platform for building proxies to bypass network restrictions.
An unidentifiable mechanism that helps you bypass GFW.
A Quantum-Safe Secure Tunnel based on QPP, KCP, FEC, and N:M multiplexing.
Go实现的Trojan代理,支持多路复用/路由功能/CDN中转/Shadowsocks混淆插件,多平台,无依赖。A Trojan proxy written in Go. An unidentifiable mechanism that helps you bypass GFW. https://p4gefau1t.github.io/trojan-go/
Xray, Penetrates Everything. Also the best v2ray-core. Where the magic happens. An open platform for various uses.
Quick Overview
GOST is a versatile and powerful proxy solution written in Go. It supports multiple protocols and encryption methods, making it suitable for various network environments and security requirements. GOST can be used as a standalone proxy server or integrated into other applications.
Pros
- Supports multiple protocols (HTTP, SOCKS4, SOCKS5, Shadowsocks, etc.)
- Offers strong encryption and security features
- Highly configurable and customizable
- Cross-platform compatibility (Windows, Linux, macOS)
Cons
- Documentation is primarily in Chinese, which may be challenging for non-Chinese speakers
- Steep learning curve due to its extensive feature set
- May require additional setup for advanced configurations
- Limited community support compared to more mainstream proxy solutions
Getting Started
To get started with GOST, follow these steps:
- Download the latest release from the GitHub releases page.
- Extract the archive and navigate to the extracted directory.
- Run GOST with a basic configuration:
./gost -L=:8080
This command starts a GOST server listening on port 8080 with default settings.
For more advanced configurations, you can use command-line flags or a configuration file. Here's an example of running GOST with multiple listeners and a chain:
./gost -L=http://:8080 -L=socks5://:1080 -F=ss://aes-128-cfb:password@example.com:8338
This command sets up an HTTP proxy on port 8080, a SOCKS5 proxy on port 1080, and forwards traffic through a Shadowsocks server.
For detailed usage instructions and configuration options, refer to the GOST documentation.
Competitor Comparisons
A Rust port of shadowsocks
Pros of shadowsocks-rust
- Written in Rust, offering better performance and memory safety
- More focused on the Shadowsocks protocol, potentially providing better optimization
- Active development with frequent updates and bug fixes
Cons of shadowsocks-rust
- Limited to Shadowsocks protocol, less versatile compared to gost's multi-protocol support
- May have a steeper learning curve for users not familiar with Rust
- Fewer built-in features compared to gost's comprehensive toolset
Code Comparison
shadowsocks-rust:
let server = ShadowsocksServer::new(config)?;
server.run().await?;
gost:
ln, err := gost.TCPListener(node.Addr)
if err != nil {
return err
}
h := gost.NewServer(handler, ln)
Both projects use concise code for server setup, but gost offers more flexibility in protocol selection and handling.
A platform for building proxies to bypass network restrictions.
Pros of v2ray-core
- More comprehensive protocol support, including VMess, VLESS, and Trojan
- Advanced routing capabilities with flexible rule-based traffic routing
- Better documentation and community support
Cons of v2ray-core
- More complex configuration and setup process
- Higher resource consumption due to its extensive feature set
- Steeper learning curve for new users
Code Comparison
v2ray-core configuration example:
{
"inbounds": [{
"port": 1080,
"protocol": "socks",
"settings": {
"auth": "noauth"
}
}],
"outbounds": [{
"protocol": "freedom"
}]
}
gost configuration example:
gost -L=:8080 -F=ss://method:password@host:port
Key Differences
- gost is more lightweight and easier to set up for simple proxy scenarios
- v2ray-core offers more advanced features and customization options
- gost focuses on simplicity and ease of use, while v2ray-core prioritizes flexibility and security
Use Cases
- gost: Quick and simple proxy setup for basic needs
- v2ray-core: Complex network environments requiring advanced routing and protocol support
Community and Development
- v2ray-core has a larger and more active community
- gost has fewer contributors but maintains a focused development approach
An unidentifiable mechanism that helps you bypass GFW.
Pros of Trojan
- Designed specifically for censorship circumvention, offering better obfuscation
- Simpler configuration and setup process
- Lighter resource usage, especially on low-end devices
Cons of Trojan
- Less versatile, primarily focused on proxy functionality
- Smaller community and fewer third-party implementations
- Limited protocol support compared to GOST's multi-protocol approach
Code Comparison
Trojan (server configuration):
{
"run_type": "server",
"local_addr": "0.0.0.0",
"local_port": 443,
"remote_addr": "127.0.0.1",
"remote_port": 80,
"password": ["password1"],
"ssl": {
"cert": "/path/to/certificate.crt",
"key": "/path/to/private.key"
}
}
GOST (server configuration):
gost -L=ss://chacha20:password@:8338
Trojan focuses on a specific proxy implementation with a more detailed configuration, while GOST offers a concise command-line interface for various protocols. Trojan's configuration is JSON-based, providing clear structure, whereas GOST uses a more compact string-based format for quick setup.
Both projects serve as proxy tools, but Trojan is tailored for censorship bypass, while GOST offers a broader range of networking capabilities. The choice between them depends on specific use cases and required features.
A Quantum-Safe Secure Tunnel based on QPP, KCP, FEC, and N:M multiplexing.
Pros of kcptun
- Focuses specifically on KCP protocol optimization, potentially offering better performance for certain use cases
- Simpler setup and configuration for basic KCP tunneling needs
- Lighter weight and more specialized than the broader feature set of gost
Cons of kcptun
- Limited to KCP protocol, while gost supports multiple protocols and transport methods
- Lacks the extensive proxy chaining and routing capabilities provided by gost
- May require additional tools or configurations for more complex networking scenarios
Code Comparison
kcptun (client configuration):
kcptun_client := &KCPClient{
RemoteAddr: "server_ip:port",
Key: "your_encryption_key",
Mode: "fast2",
Conn: 4,
}
gost (similar functionality):
gost.Run(
"kcp://server_ip:port?crypt=aes&key=your_encryption_key&mode=fast2",
"socks5://:1080",
)
Both projects aim to improve network performance and security, but gost offers a more comprehensive solution with support for various protocols and advanced features, while kcptun specializes in optimizing KCP connections.
Go实现的Trojan代理,支持多路复用/路由功能/CDN中转/Shadowsocks混淆插件,多平台,无依赖。A Trojan proxy written in Go. An unidentifiable mechanism that helps you bypass GFW. https://p4gefau1t.github.io/trojan-go/
Pros of trojan-go
- Focuses specifically on the Trojan protocol, offering optimized performance for this use case
- Includes built-in support for WebSocket and other transport layers
- Provides a user-friendly web-based management interface
Cons of trojan-go
- More limited in protocol support compared to gost's multi-protocol capabilities
- May have a steeper learning curve for users not familiar with Trojan protocol
- Less frequent updates and potentially smaller community compared to gost
Code Comparison
trojan-go configuration example:
{
"run_type": "server",
"local_addr": "0.0.0.0",
"local_port": 443,
"remote_addr": "127.0.0.1",
"remote_port": 80,
"password": ["your_password"]
}
gost configuration example:
gost -L=ss://chacha20:your_password@:8338 \
-L=socks5://:1080 \
-F=ss+wss://chacha20:your_password@example.com:443
Both projects aim to provide secure proxy solutions, but they differ in their approach and focus. trojan-go specializes in the Trojan protocol, while gost offers a wider range of protocols and more flexibility in configuration. The choice between them depends on specific use cases and user preferences.
Xray, Penetrates Everything. Also the best v2ray-core. Where the magic happens. An open platform for various uses.
Pros of Xray-core
- More advanced protocol support, including VLESS and XTLS
- Better performance and lower latency due to optimized core
- Active development with frequent updates and improvements
Cons of Xray-core
- Steeper learning curve due to more complex configuration options
- Less versatile in terms of supported proxy types compared to gost
Code Comparison
Xray-core configuration example:
{
"inbounds": [{
"port": 10086,
"protocol": "vmess",
"settings": {
"clients": [{ "id": "b831381d-6324-4d53-ad4f-8cda48b30811" }]
}
}],
"outbounds": [{ "protocol": "freedom" }]
}
gost configuration example:
gost -L=:8080 -F=ss://method:password@1.2.3.4:8338
Summary
Xray-core offers more advanced features and better performance, making it suitable for users who require cutting-edge proxy technologies. However, it may be more challenging to set up and use compared to gost. gost, on the other hand, provides a simpler configuration and a wider range of proxy types, making it more versatile for general use cases. The choice between the two depends on specific requirements and user expertise.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
GO Simple Tunnel
GOè¯è¨å®ç°çå®å ¨é§é
ç¹æ§
- å¤ç«¯å£çå¬
- å¯è®¾ç½®è½¬å代çï¼æ¯æå¤çº§è½¬å(代çé¾)
- æ¯ææ åHTTP/HTTPS/HTTP2/SOCKS4(A)/SOCKS5代çåè®®
- Web代çæ¯ææ¢æµé²å¾¡
- æ¯æå¤ç§é§éç±»å
- SOCKS5代çæ¯æTLSååå å¯
- Tunnel UDP over TCP
- TCP/UDPéæ代ç
- æ¬å°/è¿ç¨TCP/UDP端å£è½¬å
- æ¯æShadowsocks(TCP/UDP)åè®®
- æ¯æSNI代ç
- æéæ§å¶
- è´è½½åè¡¡
- è·¯ç±æ§å¶
- DNS解æå代ç
- TUN/TAP设å¤
Wikiç«ç¹: v2.gost.run
Telegram讨论群: https://t.me/gogost
Google讨论ç»: https://groups.google.com/d/forum/go-gost
GOST v3 https://gost.run
å®è£
äºè¿å¶æ件
https://github.com/ginuerzh/gost/releases
æºç ç¼è¯
git clone https://github.com/ginuerzh/gost.git
cd gost/cmd/gost
go build
Docker
docker run --rm ginuerzh/gost -V
Homebrew
brew install gost
Ubuntuååº
sudo snap install core
sudo snap install gost
å¿«éä¸æ
ä¸è®¾ç½®è½¬å代ç
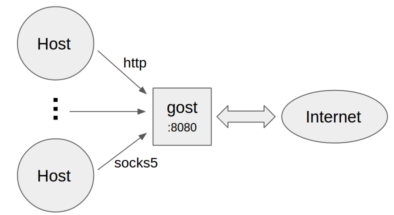
- ä½ä¸ºæ åHTTP/SOCKS5代ç
gost -L=:8080
- 设置代ç认è¯ä¿¡æ¯
gost -L=admin:123456@localhost:8080
- å¤ç«¯å£çå¬
gost -L=http2://:443 -L=socks5://:1080 -L=ss://aes-128-cfb:123456@:8338
设置转å代ç
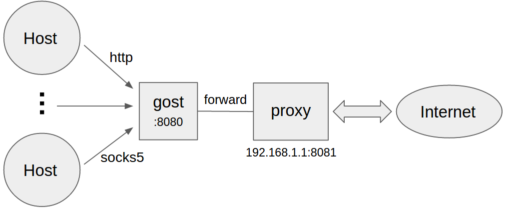
gost -L=:8080 -F=192.168.1.1:8081
- 转å代ç认è¯
gost -L=:8080 -F=http://admin:123456@192.168.1.1:8081
设置å¤çº§è½¬å代ç(代çé¾)
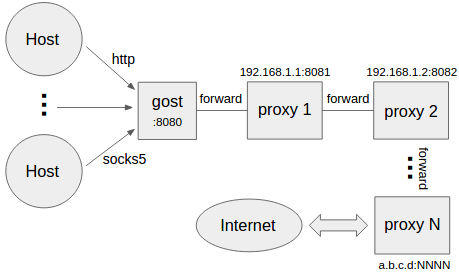
gost -L=:8080 -F=quic://192.168.1.1:6121 -F=socks5+wss://192.168.1.2:1080 -F=http2://192.168.1.3:443 ... -F=a.b.c.d:NNNN
gostæç §-F设置ç顺åºéè¿ä»£çé¾å°è¯·æ±æç»è½¬åç»a.b.c.d:NNNNå¤çï¼æ¯ä¸ä¸ªè½¬å代çå¯ä»¥æ¯ä»»æHTTP/HTTPS/HTTP2/SOCKS4/SOCKS5/Shadowsocksç±»å代çã
æ¬å°ç«¯å£è½¬å(TCP)
gost -L=tcp://:2222/192.168.1.1:22 [-F=...]
å°æ¬å°TCP端å£2222ä¸çæ°æ®(éè¿ä»£çé¾)转åå°192.168.1.1:22ä¸ãå½ä»£çé¾æ«ç«¯(æåä¸ä¸ª-Fåæ°)为SSH转åééç±»åæ¶ï¼gostä¼ç´æ¥ä½¿ç¨SSHçæ¬å°ç«¯å£è½¬ååè½:
gost -L=tcp://:2222/192.168.1.1:22 -F forward+ssh://:2222
æ¬å°ç«¯å£è½¬å(UDP)
gost -L=udp://:5353/192.168.1.1:53?ttl=60 [-F=...]
å°æ¬å°UDP端å£5353ä¸çæ°æ®(éè¿ä»£çé¾)转åå°192.168.1.1:53ä¸ã
æ¯æ¡è½¬åééé½æè¶
æ¶æ¶é´ï¼å½è¶
è¿æ¤æ¶é´ï¼ä¸å¨æ¤æ¶é´æ®µå
æ ä»»ä½æ°æ®äº¤äºï¼åæ¤ééå°å
³éãå¯ä»¥éè¿ttlåæ°æ¥è®¾ç½®è¶
æ¶æ¶é´ï¼é»è®¤å¼ä¸º60ç§ã
注: 转åUDPæ°æ®æ¶ï¼å¦ææ代çé¾ï¼å代çé¾çæ«ç«¯(æåä¸ä¸ª-Fåæ°)å¿ é¡»æ¯gost SOCKS5ç±»å代çï¼gostä¼ä½¿ç¨UDP over TCPæ¹å¼è¿è¡è½¬åã
è¿ç¨ç«¯å£è½¬å(TCP)
gost -L=rtcp://:2222/192.168.1.1:22 [-F=... -F=socks5://172.24.10.1:1080]
å°172.24.10.1:2222ä¸çæ°æ®(éè¿ä»£çé¾)转åå°192.168.1.1:22ä¸ãå½ä»£çé¾æ«ç«¯(æåä¸ä¸ª-Fåæ°)为SSH转åééç±»åæ¶ï¼gostä¼ç´æ¥ä½¿ç¨SSHçè¿ç¨ç«¯å£è½¬ååè½:
gost -L=rtcp://:2222/192.168.1.1:22 -F forward+ssh://:2222
è¿ç¨ç«¯å£è½¬å(UDP)
gost -L=rudp://:5353/192.168.1.1:53?ttl=60 [-F=... -F=socks5://172.24.10.1:1080]
å°172.24.10.1:5353ä¸çæ°æ®(éè¿ä»£çé¾)转åå°192.168.1.1:53ä¸ã
æ¯æ¡è½¬åééé½æè¶
æ¶æ¶é´ï¼å½è¶
è¿æ¤æ¶é´ï¼ä¸å¨æ¤æ¶é´æ®µå
æ ä»»ä½æ°æ®äº¤äºï¼åæ¤ééå°å
³éãå¯ä»¥éè¿ttlåæ°æ¥è®¾ç½®è¶
æ¶æ¶é´ï¼é»è®¤å¼ä¸º60ç§ã
注: 转åUDPæ°æ®æ¶ï¼å¦ææ代çé¾ï¼å代çé¾çæ«ç«¯(æåä¸ä¸ª-Fåæ°)å¿ é¡»æ¯GOST SOCKS5ç±»å代çï¼gostä¼ä½¿ç¨UDP-over-TCPæ¹å¼è¿è¡è½¬åã
HTTP2
gostçHTTP2æ¯æ两ç§æ¨¡å¼ï¼
- ä½ä¸ºæ åçHTTP2代çï¼å¹¶åä¸å ¼å®¹HTTPS代çã
- ä½ä¸ºééä¼ è¾å ¶ä»åè®®ã
代ç模å¼
æå¡ç«¯:
gost -L=http2://:443
客æ·ç«¯:
gost -L=:8080 -F=http2://server_ip:443
éé模å¼
æå¡ç«¯:
gost -L=h2://:443
客æ·ç«¯:
gost -L=:8080 -F=h2://server_ip:443
QUIC
gost对QUICçæ¯ææ¯åºäºquic-goåºã
æå¡ç«¯:
gost -L=quic://:6121
客æ·ç«¯:
gost -L=:8080 -F=quic://server_ip:6121
æ³¨ï¼ QUIC模å¼åªè½ä½ä¸ºä»£çé¾ç第ä¸ä¸ªèç¹ã
KCP
gost对KCPçæ¯ææ¯åºäºkcp-goåkcptunåºã
æå¡ç«¯:
gost -L=kcp://:8388
客æ·ç«¯:
gost -L=:8080 -F=kcp://server_ip:8388
gostä¼èªå¨å è½½å½åå·¥ä½ç®å½ä¸çkcp.json(å¦æåå¨)é ç½®æ件ï¼æè å¯ä»¥æå¨éè¿åæ°æå®é ç½®æ件路å¾ï¼
gost -L=kcp://:8388?c=/path/to/conf/file
æ³¨ï¼ KCP模å¼åªè½ä½ä¸ºä»£çé¾ç第ä¸ä¸ªèç¹ã
SSH
gostçSSHæ¯æ两ç§æ¨¡å¼ï¼
- ä½ä¸ºè½¬åééï¼é åæ¬å°/è¿ç¨TCP端å£è½¬å使ç¨ã
- ä½ä¸ºééä¼ è¾å ¶ä»åè®®ã
转å模å¼
æå¡ç«¯:
gost -L=forward+ssh://:2222
客æ·ç«¯:
gost -L=rtcp://:1222/:22 -F=forward+ssh://server_ip:2222
éé模å¼
æå¡ç«¯:
gost -L=ssh://:2222
客æ·ç«¯:
gost -L=:8080 -F=ssh://server_ip:2222?ping=60
å¯ä»¥éè¿pingåæ°è®¾ç½®å¿è·³å
åéå¨æï¼åä½ä¸ºç§ãé»è®¤ä¸åéå¿è·³å
ã
éæ代ç
åºäºiptablesçéæ代çã
gost -L=redirect://:12345 -F=http2://server_ip:443
obfs4
æ¤åè½ç±@isofewè´¡ç®ã
æå¡ç«¯:
gost -L=obfs4://:443
å½æå¡ç«¯è¿è¡åä¼å¨æ§å¶å°æå°åºè¿æ¥å°åä¾å®¢æ·ç«¯ä½¿ç¨:
obfs4://:443/?cert=4UbQjIfjJEQHPOs8vs5sagrSXx1gfrDCGdVh2hpIPSKH0nklv1e4f29r7jb91VIrq4q5Jw&iat-mode=0
客æ·ç«¯:
gost -L=:8888 -F='obfs4://server_ip:443?cert=4UbQjIfjJEQHPOs8vs5sagrSXx1gfrDCGdVh2hpIPSKH0nklv1e4f29r7jb91VIrq4q5Jw&iat-mode=0'
å å¯æºå¶
HTTP
对äºHTTPå¯ä»¥ä½¿ç¨TLSå å¯æ´ä¸ªé讯è¿ç¨ï¼å³HTTPS代çï¼
æå¡ç«¯:
gost -L=https://:443
客æ·ç«¯:
gost -L=:8080 -F=http+tls://server_ip:443
HTTP2
gostçHTTP2代ç模å¼ä» æ¯æ使ç¨TLSå å¯çHTTP2åè®®ï¼ä¸æ¯æææHTTP2ä¼ è¾ã
gostçHTTP2éé模å¼æ¯æå å¯(h2)åææ(h2c)两ç§æ¨¡å¼ã
SOCKS5
gostæ¯ææ åSOCKS5åè®®çno-auth(0x00)åuser/pass(0x02)æ¹æ³ï¼å¹¶å¨æ¤åºç¡ä¸æ©å±äºä¸¤ä¸ªï¼tls(0x80)åtls-auth(0x82)ï¼ç¨äºæ°æ®å å¯ã
æå¡ç«¯:
gost -L=socks5://:1080
客æ·ç«¯:
gost -L=:8080 -F=socks5://server_ip:1080
å¦æ两端é½æ¯gost(å¦ä¸)åæ°æ®ä¼ è¾ä¼è¢«å å¯(åå使ç¨tlsætls-authæ¹æ³)ï¼å¦å使ç¨æ åSOCKS5è¿è¡é讯(no-authæuser/passæ¹æ³)ã
Shadowsocks
gost对shadowsocksçæ¯ææ¯åºäºshadowsocks-goåºã
æå¡ç«¯:
gost -L=ss://chacha20:123456@:8338
客æ·ç«¯:
gost -L=:8080 -F=ss://chacha20:123456@server_ip:8338
Shadowsocks UDP relay
ç®åä» æå¡ç«¯æ¯æUDP Relayã
æå¡ç«¯:
gost -L=ssu://chacha20:123456@:8338
TLS
gostå ç½®äºTLSè¯ä¹¦ï¼å¦æéè¦ä½¿ç¨å ¶ä»TLSè¯ä¹¦ï¼æ两ç§æ¹æ³ï¼
- å¨gostè¿è¡ç®å½æ¾ç½®cert.pem(å ¬é¥)åkey.pem(ç§é¥)两个æ件å³å¯ï¼gostä¼èªå¨å è½½è¿è¡ç®å½ä¸çcert.pemåkey.pemæ件ã
- 使ç¨åæ°æå®è¯ä¹¦æ件路å¾ï¼
gost -L="http2://:443?cert=/path/to/my/cert/file&key=/path/to/my/key/file"
对äºå®¢æ·ç«¯å¯ä»¥éè¿secureåæ°å¼å¯æå¡å¨è¯ä¹¦åååæ ¡éª:
gost -L=:8080 -F="http2://server_domain_name:443?secure=true"
对äºå®¢æ·ç«¯å¯ä»¥æå®CAè¯ä¹¦è¿è¡è¯ä¹¦éå®(Certificate Pinning):
gost -L=:8080 -F="http2://:443?ca=ca.pem"
è¯ä¹¦éå®åè½ç±@sheerunè´¡ç®
Top Related Projects
A Rust port of shadowsocks
A platform for building proxies to bypass network restrictions.
An unidentifiable mechanism that helps you bypass GFW.
A Quantum-Safe Secure Tunnel based on QPP, KCP, FEC, and N:M multiplexing.
Go实现的Trojan代理,支持多路复用/路由功能/CDN中转/Shadowsocks混淆插件,多平台,无依赖。A Trojan proxy written in Go. An unidentifiable mechanism that helps you bypass GFW. https://p4gefau1t.github.io/trojan-go/
Xray, Penetrates Everything. Also the best v2ray-core. Where the magic happens. An open platform for various uses.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot
