Top Related Projects
The Rogue Access Point Framework
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Open-Source Phishing Toolkit
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
An automated phishing tool with 30+ templates. This Tool is made for educational purpose only ! Author will not be responsible for any misuse of this toolkit !
Quick Overview
King Phisher is an open-source phishing campaign toolkit. It provides a platform for creating and managing phishing campaigns, including email sending, website cloning, and result tracking. The tool is designed for use by cybersecurity professionals for penetration testing and security awareness training.
Pros
- Comprehensive phishing campaign management
- User-friendly graphical interface
- Customizable templates and landing pages
- Detailed reporting and analytics
Cons
- Steep learning curve for beginners
- Requires careful setup and configuration
- Potential for misuse if not used responsibly
- Limited documentation for advanced features
Code Examples
# Create a new campaign
campaign = king_phisher.server.server.build_king_phisher_campaign(
name="Test Campaign",
description="A sample phishing campaign",
user_id=1
)
# Send a phishing email
mailer = king_phisher.client.mailer.MailSenderThread(
target_file="targets.csv",
campaign_id=campaign.id,
server="smtp.example.com"
)
mailer.start()
# Generate a phishing website
site_template = king_phisher.client.web_cloner.WebPageCloner(
"https://example.com",
"cloned_site"
)
site_template.clone()
Getting Started
-
Install King Phisher:
git clone https://github.com/rsmusllp/king-phisher.git cd king-phisher sudo tools/install.sh -
Start the King Phisher server:
king-phisher server start -
Launch the King Phisher client:
king-phisher -
Create a new campaign in the client interface and follow the wizard to set up your phishing campaign.
Competitor Comparisons
The Rogue Access Point Framework
Pros of Wifiphisher
- Specialized for Wi-Fi attacks, making it more focused and efficient for wireless network penetration testing
- Includes a variety of pre-built phishing scenarios, reducing setup time for common attack vectors
- Supports Evil Twin attacks, allowing for more sophisticated wireless-based social engineering
Cons of Wifiphisher
- Limited to Wi-Fi-based attacks, whereas King-Phisher offers a broader range of phishing campaign options
- Less customizable than King-Phisher for creating tailored phishing scenarios
- Lacks some of the advanced reporting and analytics features found in King-Phisher
Code Comparison
Wifiphisher (Python):
def start(self):
"""
Start the engine.
"""
self.network_manager.start()
self.template_manager.start()
self.phishinghttp.start()
King-Phisher (Python):
def start_campaign(self, campaign_id, campaign_name):
campaign = self.db_manager.get_campaign(campaign_id)
if campaign is None:
raise KingPhisherAPIError('invalid campaign id')
self.current_campaign = campaign
self.logger.info("starting campaign: {0}".format(campaign_name))
Both projects use Python and have similar high-level structures for starting their respective operations. However, Wifiphisher's code is more focused on network and template management, while King-Phisher's code emphasizes campaign management and database interactions.
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Pros of Social-Engineer-Toolkit
- More comprehensive toolset for various social engineering attacks
- Includes additional features like website cloning and mass mailer
- Longer development history and larger community support
Cons of Social-Engineer-Toolkit
- Command-line interface may be less user-friendly for some users
- Less focus on phishing campaign management and reporting
- Requires more manual configuration for some attack scenarios
Code Comparison
King-Phisher (Python):
def send_message(self, target, message):
self.smtp_connection.sendmail(self.config.sender, target, message)
self.logger.info(f"Sent phishing email to {target}")
Social-Engineer-Toolkit (Python):
def mass_mailer(to, subject, body):
msg = MIMEMultipart()
msg['From'] = sender
msg['Subject'] = subject
msg.attach(MIMEText(body, 'plain'))
server.sendmail(sender, to, msg.as_string())
Both projects use Python for email sending functionality, but Social-Engineer-Toolkit offers more flexibility in message composition, while King-Phisher focuses on simplified campaign management.
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Pros of evilginx2
- More focused on advanced phishing attacks and credential harvesting
- Supports multiple target websites and custom phishlets
- Actively maintained with frequent updates
Cons of evilginx2
- Steeper learning curve and more complex setup
- Limited reporting and campaign management features
- Narrower scope, primarily focused on credential theft
Code Comparison
King-phisher (Python):
def send_message(self, message_id, campaign_id, target_email, first_name, last_name):
message = self.get_template(message_id, campaign_id)
message = message.format(first_name=first_name, last_name=last_name)
self.smtp_send(target_email, message)
evilginx2 (Go):
func (p *Phishlet) GenerateTokenSet(tokens map[string]string) map[string]string {
ret := make(map[string]string)
for k, v := range p.tokens {
ret[k] = v.generateTokenValue(tokens)
}
return ret
}
King-phisher is more focused on email phishing campaigns, while evilginx2 specializes in creating sophisticated phishing proxies. King-phisher offers broader campaign management features, while evilginx2 excels in real-time credential interception and session hijacking.
Open-Source Phishing Toolkit
Pros of Gophish
- Simpler setup and easier to use, especially for beginners
- Written in Go, which offers better performance and easier deployment
- More active community and frequent updates
Cons of Gophish
- Less customizable than King Phisher
- Fewer advanced features and reporting options
- Limited integration capabilities compared to King Phisher
Code Comparison
King Phisher (Python):
def send_message(self, target_email, campaign_name):
message = self.create_message(target_email, campaign_name)
self.smtp_connection.send(message)
self.db.add_sent_message(target_email, campaign_name)
Gophish (Go):
func (s *SMTPWorker) SendEmail(e *Email) error {
msg := gomail.NewMessage()
msg.SetHeader("From", e.From)
msg.SetHeader("To", e.To)
msg.SetHeader("Subject", e.Subject)
msg.SetBody("text/html", e.HTML)
return s.mailer.DialAndSend(msg)
}
Both projects aim to provide phishing campaign simulation tools, but they differ in their approach and implementation. King Phisher offers more advanced features and customization options, while Gophish focuses on simplicity and ease of use. The code comparison shows that King Phisher uses Python and includes database operations, while Gophish utilizes Go and focuses on email sending functionality.
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
Pros of Responder
- Lightweight and easy to deploy
- Focuses on specific network attacks (LLMNR, NBT-NS, MDNS poisoning)
- Active development and frequent updates
Cons of Responder
- Limited scope compared to King Phisher's comprehensive phishing campaign features
- Less user-friendly interface for non-technical users
- Requires more manual configuration and analysis
Code Comparison
Responder (Python):
def start():
global OURIP
if options.Interface is None:
OURIP = FindLocalIP()
elif options.Interface == 'ALL':
OURIP = '0.0.0.0'
else:
OURIP = FindLocalIP(options.Interface)
King Phisher (Python):
def start_server(self, *args, **kwargs):
if self.server_running:
return
self.server = servers.KingPhisherServer(self.config, self.job_manager)
self.server.start()
self.server_running = True
Both projects use Python, but Responder focuses on network-level operations, while King Phisher emphasizes higher-level phishing campaign management. Responder's code deals with IP configuration, while King Phisher's example shows server management for phishing campaigns.
An automated phishing tool with 30+ templates. This Tool is made for educational purpose only ! Author will not be responsible for any misuse of this toolkit !
Pros of zphisher
- Simpler setup and usage, making it more accessible for beginners
- Includes a wider variety of pre-built phishing templates
- Lighter weight and requires fewer system resources
Cons of zphisher
- Less comprehensive features compared to King Phisher's advanced capabilities
- Limited customization options for phishing campaigns
- Lacks the robust reporting and analytics features of King Phisher
Code Comparison
King Phisher (Python):
def send_message(self, message_id, campaign_id, target_email, first_name, last_name):
message = self.get_template(message_id)
campaign = self.get_campaign(campaign_id)
return self.mailer.send(message, campaign, target_email, first_name, last_name)
zphisher (Bash):
tunnel_menu() {
if [[ -e ".server/ngrok" ]]; then
echo -e "\n${GREEN}[${WHITE}1${GREEN}]${CYAN} Ngrok"
fi
echo -e "\n${GREEN}[${WHITE}2${GREEN}]${CYAN} Localhost"
read -p "${GREEN}[${WHITE}-${GREEN}]${CYAN} Select a port forwarding service: ${WHITE}"
}
The code snippets highlight the difference in complexity and approach between the two projects. King Phisher uses Python for more advanced functionality, while zphisher relies on Bash scripting for simpler operations.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

King Phisher 



Phishing Campaign Toolkit
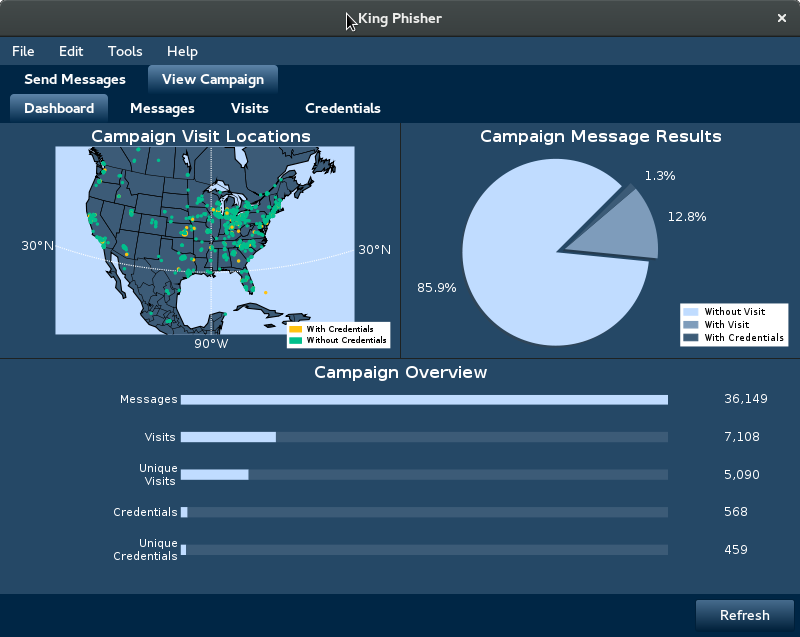
King Phishger is no longer being maintained.
Installation
For instructions on how to install, please see the INSTALL.md file. After installing, for instructions on how to get started please see the wiki.
Overview
King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. It features an easy to use, yet very flexible architecture allowing full control over both emails and server content. King Phisher can be used to run campaigns ranging from simple awareness training to more complicated scenarios in which user aware content is served for harvesting credentials.
King Phisher is only to be used for legal applications when the explicit permission of the targeted organization has been obtained.
Get the latest stable version from the GitHub Releases Page or use git to checkout the project from source.
Feature Overview
- Run multiple phishing campaigns simultaneously
- Send email with embedded images for a more legitimate appearance
- Optional Two-Factor authentication
- Credential harvesting from landing pages
- SMS alerts regarding campaign status
- Web page cloning capabilities
- Integrated Sender Policy Framework (SPF) checks
- Geo location of phishing visitors
- Send email with calendar invitations
Plugins
Both the client and server can be extended with functionality provided by plugins. A small number of plugins are packaged with King Phisher and additional ones are available in the Plugins repository.
Template Files
Template files for both messages and server pages can be found in the separate King Phisher Templates repository. Any contributions regarding templates should also be submitted via a pull request to the templates repository.
Documentation
Documentation for users of the application is provided on the project's wiki page. This includes steps to help new users get started with their first campaigns. Additional technical documentation intended for developers is kept separate as outlined in section below.
Code Documentation
King Phisher uses Sphinx for internal technical documentation. This
documentation can be generated from source with the command
sphinx-build -b html docs/source docs/html. The latest documentation is
kindly hosted on ReadTheDocs at
king-phisher.readthedocs.io.
Message Template Variables
The client message templates are formatted using the Jinja2 templating engine and support a number of variables. These are included here as a reference, check the templates wiki page for comprehensive documentation.
| Variable Name | Variable Value |
|---|---|
| client.company_name | The target's company name |
| client.email_address | The target's email address |
| client.first_name | The target's first name |
| client.last_name | The target's last name |
| client.message_id | The unique tracking identifier (this is the same as uid) |
| sender.email | The email address in the "Source Email (MIME)" field |
| sender.friendly_alias | The value of the "Friendly Alias" field |
| sender.reply_to | The value of the "Reply To" field |
| url.tracking_dot | URL of an image used for message tracking |
| url.webserver | Phishing server URL with the uid parameter |
| url.webserver_raw | Phishing server URL without any parameters |
| tracking_dot_image_tag | The tracking image in a preformatted <img /> tag |
| uid | The unique tracking identifier (this is the same as client.message_id) |
The uid is the most important, and must be present in links that the messages contain.
License
King Phisher is released under the BSD 3-clause license, for more details see the LICENSE file.
Credits
Special Thanks (QA / Beta Testing):
- Jake Garlie - jagar
- Jeremy Schoeneman - Shad0wman
- Bryan Sfara
- Ken Smith - p4tchw0rk
- Brianna Whittaker
King Phisher Development Team:
- Erik Daguerre - wolfthefallen (@wolf_thefallen)
- Brandan Geise - coldfusion (@coldfusion39)
- Jeff McCutchan - jamcut (@jamcut)
- Spencer McIntyre - zeroSteiner (@zeroSteiner)
Top Related Projects
The Rogue Access Point Framework
The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
Open-Source Phishing Toolkit
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
An automated phishing tool with 30+ templates. This Tool is made for educational purpose only ! Author will not be responsible for any misuse of this toolkit !
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot