Top Related Projects
Resources for Windows exploit development
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Privilege Escalation Project - Windows / Linux / Mac
Automation for internal Windows Penetrationtest / AD-Security
PowerSploit - A PowerShell Post-Exploitation Framework
Quick Overview
The sagishahar/lpeworkshop repository is a comprehensive resource for learning about and practicing Linux Privilege Escalation techniques. It provides a collection of vulnerable Linux machines, scripts, and documentation to help security professionals and enthusiasts understand and exploit various privilege escalation vulnerabilities in Linux systems.
Pros
- Offers hands-on experience with real-world privilege escalation scenarios
- Includes a wide range of vulnerabilities and techniques
- Provides detailed documentation and explanations for each vulnerability
- Regularly updated with new content and improvements
Cons
- May require significant system resources to run multiple virtual machines
- Some scenarios might be complex for beginners
- Potential security risks if not used in a controlled environment
- Limited to Linux-specific vulnerabilities
Getting Started
To get started with the lpeworkshop:
-
Clone the repository:
git clone https://github.com/sagishahar/lpeworkshop.git -
Navigate to the project directory:
cd lpeworkshop -
Read the README.md file for detailed instructions on setting up the vulnerable machines and exploring the various scenarios.
-
Use virtualization software like VirtualBox to import and run the provided vulnerable machine images.
-
Follow the documentation for each scenario to practice different privilege escalation techniques.
Note: Ensure you have sufficient system resources and a secure, isolated environment before running any vulnerable machines or executing potentially malicious code.
Competitor Comparisons
Resources for Windows exploit development
Pros of WindowsExploitationResources
- More comprehensive coverage of Windows exploitation techniques
- Includes resources for both local and remote exploitation
- Regularly updated with new content and techniques
Cons of WindowsExploitationResources
- Less focused on Local Privilege Escalation (LPE) specifically
- May be overwhelming for beginners due to its broad scope
- Lacks hands-on lab exercises found in lpeworkshop
Code Comparison
While both repositories primarily contain documentation and resources rather than code, lpeworkshop includes some PowerShell scripts for enumeration. For example:
lpeworkshop:
Get-WmiObject win32_service | select Name,State,PathName | Where-Object {$_.State -like 'Running'}
WindowsExploitationResources doesn't contain direct code examples but links to external resources with code snippets.
Summary
WindowsExploitationResources offers a broader range of Windows exploitation topics, making it suitable for those interested in various attack vectors. However, lpeworkshop provides a more focused approach to LPE with practical exercises, which may be more beneficial for those specifically targeting privilege escalation techniques. Both repositories serve as valuable resources for Windows security researchers and penetration testers, with their strengths lying in different areas of focus and presentation.
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
Pros of PayloadsAllTheThings
- Broader scope covering various security topics beyond privilege escalation
- More frequently updated with recent contributions
- Larger community with more stars and forks on GitHub
Cons of PayloadsAllTheThings
- Less focused on specific privilege escalation techniques
- May be overwhelming for beginners due to the vast amount of information
- Lacks structured learning path or workshop format
Code Comparison
PayloadsAllTheThings (Linux Privilege Escalation):
find / -perm -u=s -type f 2>/dev/null
getcap -r / 2>/dev/null
sudo -l
LPEWorkshop (Windows Privilege Escalation):
whoami /priv
Get-WmiObject -Class Win32_Service | Select-Object Name, StartName, PathName
Get-ItemProperty HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | Select-Object DisplayName, InstallLocation
Both repositories provide valuable resources for privilege escalation techniques, but they differ in their approach and scope. PayloadsAllTheThings offers a comprehensive collection of security-related payloads and techniques, while LPEWorkshop focuses specifically on privilege escalation with a structured workshop format. The code examples demonstrate the different focus areas, with PayloadsAllTheThings showing Linux commands and LPEWorkshop emphasizing Windows PowerShell commands for privilege escalation.
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Pros of PEASS-ng
- More comprehensive and actively maintained, with regular updates
- Supports multiple operating systems (Windows, Linux, macOS)
- Includes automated privilege escalation tools and scripts
Cons of PEASS-ng
- Larger codebase, potentially more complex to navigate
- May require more setup and configuration for specific use cases
Code Comparison
PEASS-ng (linpeas.sh):
if [ "$MACPEAS" ]; then
print_title "MacPEAS"
macpeas_banner
else
print_title "LinPEAS"
linpeas_banner
fi
lpeworkshop (linux/lpe.sh):
echo "Linux Privilege Escalation Workshop"
echo "-----------------------------------"
echo
echo "Running checks..."
echo
Summary
PEASS-ng is a more comprehensive and actively maintained project, offering support for multiple operating systems and automated privilege escalation tools. However, it may be more complex to navigate due to its larger codebase. lpeworkshop, on the other hand, appears to be a simpler, workshop-focused project with a more straightforward approach to Linux privilege escalation. The code comparison shows that PEASS-ng includes more sophisticated logic for different operating systems, while lpeworkshop has a simpler, more focused structure.
Privilege Escalation Project - Windows / Linux / Mac
Pros of BeRoot
- Focused specifically on Windows privilege escalation techniques
- Includes automated checks for common misconfigurations
- Actively maintained with recent updates
Cons of BeRoot
- Limited to Windows environments
- Less comprehensive coverage of Linux privilege escalation techniques
- Smaller community and fewer contributors
Code Comparison
BeRoot (Python):
def check_msv1_0():
try:
key = OpenKey(HKEY_LOCAL_MACHINE, r"SYSTEM\CurrentControlSet\Control\Lsa")
value = QueryValueEx(key, "RunAsPPL")[0]
if value == 0:
print_debug("MSV1_0 authentication package is vulnerable")
except:
pass
LPEWorkshop (Bash):
function check_sudo_version {
sudo_version=$(sudo -V | grep "Sudo version" | cut -d' ' -f3)
if [[ $(echo "${sudo_version} < 1.8.28" | bc) -eq 1 ]]; then
echo "[+] Sudo version < 1.8.28, potential CVE-2019-14287 vulnerability"
fi
}
Both repositories focus on privilege escalation techniques, but BeRoot is more Windows-centric, while LPEWorkshop covers a broader range of systems. BeRoot offers automated checks and is actively maintained, while LPEWorkshop provides a more comprehensive workshop-style approach to learning privilege escalation techniques across multiple platforms.
Automation for internal Windows Penetrationtest / AD-Security
Pros of WinPwn
- More comprehensive toolset for Windows privilege escalation and post-exploitation
- Actively maintained with regular updates and contributions
- Includes PowerShell-based modules for easier integration with Windows environments
Cons of WinPwn
- Larger codebase may be more complex to navigate for beginners
- Primarily focused on Windows systems, limiting its use in multi-platform environments
- Requires more setup and dependencies compared to lpeworkshop
Code Comparison
WinPwn (PowerShell):
function Invoke-WindowsEnum{
[CmdletBinding()]
Param (
[Switch]
$noninteractive,
[Switch]
$consoleoutput
)
...
}
lpeworkshop (Bash):
#!/bin/bash
# Local Privilege Escalation Workshop - Main Script
# https://github.com/sagishahar/lpeworkshop
clear
echo "Starting Linux Local Privilege Escalation Workshop..."
...
Summary
WinPwn offers a more extensive and actively maintained toolkit specifically for Windows systems, with PowerShell integration. However, it may be more complex for beginners and less versatile across platforms. lpeworkshop provides a simpler, bash-based approach that's easier to understand but less comprehensive and primarily focused on Linux systems. The choice between the two depends on the target environment and the user's familiarity with Windows or Linux privilege escalation techniques.
PowerSploit - A PowerShell Post-Exploitation Framework
Pros of PowerSploit
- More comprehensive toolkit with a wider range of post-exploitation modules
- Actively maintained with regular updates and contributions
- Extensive documentation and usage examples
Cons of PowerSploit
- Larger codebase, potentially more complex to navigate
- May trigger antivirus software more easily due to its popularity
- Requires more PowerShell knowledge to utilize effectively
Code Comparison
PowerSploit (Get-GPPPassword function):
function Get-GPPPassword {
[CmdletBinding()]
Param (
[Parameter(Mandatory=$false,
HelpMessage="Credentials to use when connecting to a Domain Controller.")]
[System.Management.Automation.PSCredential]
[System.Management.Automation.Credential()]$Credential = [System.Management.Automation.PSCredential]::Empty
)
lpeworkshop (Windows Kernel Exploit):
#include <windows.h>
#include <stdio.h>
#define DEVICE_NAME "\\\\.\\HackSysExtremeVulnerableDriver"
int main() {
HANDLE hDevice = CreateFile(DEVICE_NAME, GENERIC_READ | GENERIC_WRITE, 0, NULL, OPEN_EXISTING, FILE_ATTRIBUTE_NORMAL, NULL);
The code snippets demonstrate the different focus areas of the two repositories. PowerSploit emphasizes PowerShell-based post-exploitation techniques, while lpeworkshop provides examples of low-level Windows kernel exploitation.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
Windows / Linux Local Privilege Escalation Workshop
My give back to the community initiative that was presented for free at several private and public events across Australia:
- Sydney - PlatypusCon (2017)
- Perth - BsidesPerth (2017)
- Brisbane - CrikeyCon (2018)
The workshop is based on the attack tree below, which covers all known (at the time) attack vectors of local user privilege escalation on both Linux and Windows operating systems.
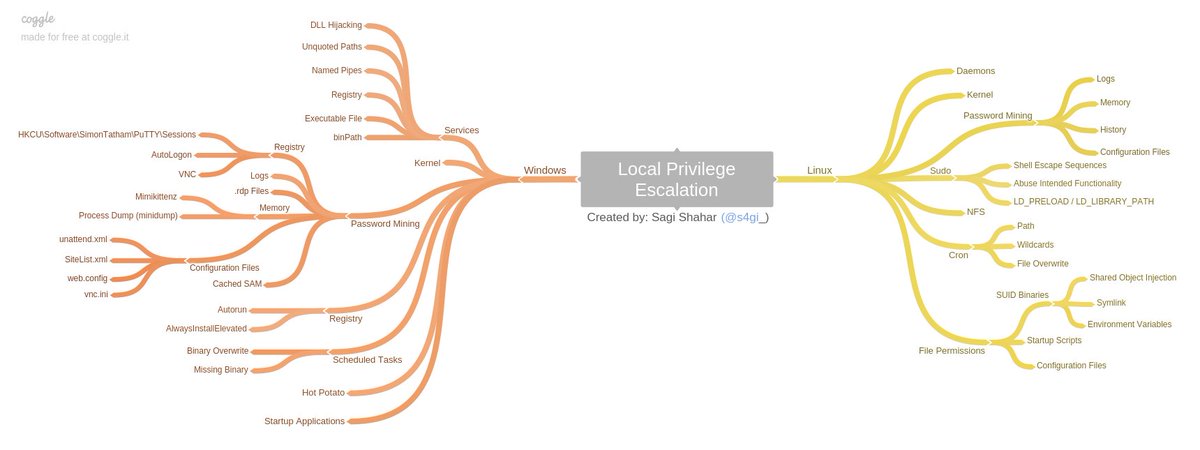
Material
- Workshop Slide Deck
- Exercise Worksheets (Linux, Windows)
- Lab VM for Linux Exercises (username: user / password: password321, username: root / password: password123)
- Kali VM for Linux/Windows Exercises (root:toor)
- Videos for Windows Exercises
- Tools for Windows Exercises (7z archive password: lpeworkshop)
- Windows exercises setup script
Setup Instructions for Windows
- Start a Windows VM that you legitimately own
- Login to the Windows VM using a user account that has administrator privileges
- Ensure the Windows VM does not have a user account named 'user'. If it exists, delete it
- Copy the setup script (lpe_windows_setup.bat) to a writeable location on a Windows VM (the Desktop directory is fine)
- Right click on the copied setup file and ensure to select from the pop-up menu 'run as Administrator'
- Read carefully the output of the script
- Restart the Windows VM
- Copy the Tools 7z archive to the Desktop and extract it
- Setup is now complete, enjoy
The script was developed and tested on a Windows 7 (SP1) x64 Build 7601 English-US host. It might work on other OS instances, but it is not guaranteed. Pay attention to the script's output. Some exercises are skipped (e.g. Kernel, etc.) as it depends on the patchlevel of the VM.
NOTE: As with any intentionally vulnerable hosts, ensure the Windows VM is not connected to an externally facing network.
Top Related Projects
Resources for Windows exploit development
A list of useful payloads and bypass for Web Application Security and Pentest/CTF
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Privilege Escalation Project - Windows / Linux / Mac
Automation for internal Windows Penetrationtest / AD-Security
PowerSploit - A PowerShell Post-Exploitation Framework
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot