Top Related Projects
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Tfsec is now part of Trivy
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Quick Overview
terraform-compliance is a lightweight, security and compliance focused test framework against Terraform. It enables users to write human-readable tests that can be executed against Terraform plan files, ensuring infrastructure-as-code adheres to company policies, security practices, and compliance requirements.
Pros
- Easy to learn and use with its BDD-style (Behavior Driven Development) syntax
- Integrates well with CI/CD pipelines for automated compliance checks
- Customizable and extensible for specific organizational needs
- Helps catch potential security and compliance issues early in the development process
Cons
- Limited to Terraform-specific checks and cannot be used for other IaC tools
- Requires separate execution after Terraform plan, which may add time to CI/CD processes
- May require additional effort to maintain and update compliance rules as infrastructure evolves
- Learning curve for writing effective and comprehensive compliance rules
Code Examples
- Basic compliance rule:
Scenario: Ensure all S3 buckets have encryption enabled
Given I have AWS S3 Bucket defined
Then it must have encryption enabled
- Checking for specific tags:
Scenario: Ensure all EC2 instances have required tags
Given I have AWS EC2 Instance defined
When it has tags
Then it must contain tags: ["Environment", "Owner", "Project"]
- Verifying security group rules:
Scenario: Ensure no security group allows unrestricted inbound access
Given I have AWS Security Group defined
When it has ingress
Then it must not have ingress with cidr block 0.0.0.0/0
Getting Started
-
Install terraform-compliance:
pip install terraform-compliance -
Create a feature file (e.g.,
s3_encryption.feature) with your compliance rules:Feature: S3 Bucket Compliance Scenario: Ensure all S3 buckets have encryption enabled Given I have AWS S3 Bucket defined Then it must have encryption enabled -
Run terraform-compliance against your Terraform plan:
terraform plan -out=plan.out terraform show -json plan.out > plan.json terraform-compliance -f s3_encryption.feature -p plan.json
Competitor Comparisons
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Pros of Checkov
- Supports multiple IaC languages (Terraform, CloudFormation, Kubernetes, etc.)
- Extensive built-in policy library with 1000+ pre-defined checks
- Integrates with CI/CD pipelines and provides machine-readable output formats
Cons of Checkov
- May require more setup and configuration for custom policies
- Can be slower for large codebases due to its comprehensive scanning approach
Code Comparison
terraform-compliance/cli example:
Scenario: Ensure all EC2 instances have tags
Given I have AWS EC2 instance defined
Then it must contain tags
And its value must not be null
Checkov example:
check = Check(check_id="CKV_AWS_1")
check.name = "Ensure all EC2 instances have tags"
check.supported_resources = ['aws_instance']
check.missing_attribute_result = CheckResult.FAILED
def check_resource(resource_conf):
if 'tags' in resource_conf and resource_conf['tags']:
return CheckResult.PASSED
return CheckResult.FAILED
check.scan_resource_conf = check_resource
Both tools aim to ensure infrastructure compliance, but Checkov offers a more comprehensive approach with support for multiple IaC languages and a larger policy library. terraform-compliance focuses specifically on Terraform and uses a more human-readable, BDD-style syntax for defining checks.
Tfsec is now part of Trivy
Pros of tfsec
- Faster scanning speed, especially for large codebases
- Built-in support for custom rules using Rego language
- Integrates well with CI/CD pipelines and provides machine-readable output formats
Cons of tfsec
- Less flexible in terms of rule customization compared to terraform-compliance
- May produce more false positives in certain scenarios
- Lacks the ability to use Gherkin syntax for writing human-readable tests
Code Comparison
tfsec example:
resource "aws_s3_bucket" "my_bucket" {
bucket = "my-bucket"
acl = "private"
}
terraform-compliance example:
Scenario: Ensure S3 buckets are private
Given I have AWS S3 Bucket defined
Then it must contain acl
And its value must be private
Both tools aim to improve Terraform code security, but they approach the task differently. tfsec focuses on static analysis and predefined rules, while terraform-compliance offers more flexibility with its BDD-style syntax. The choice between them depends on specific project requirements and team preferences.
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Pros of Terrascan
- Supports multiple IaC tools (Terraform, Kubernetes, Helm, Kustomize, Dockerfiles)
- Offers a wider range of built-in policies and security checks
- Provides a web UI for easier visualization and management of scan results
Cons of Terrascan
- May have a steeper learning curve due to its broader scope
- Can be more resource-intensive, especially for large-scale projects
- Less focused on Terraform-specific compliance checks
Code Comparison
Terrascan:
terrascan scan -i terraform -d /path/to/terraform/files
terraform-compliance:
terraform-compliance -p /path/to/terraform/plan.out -f /path/to/features
Key Differences
- Scope: Terrascan is a multi-IaC tool, while terraform-compliance focuses solely on Terraform.
- Policy Definition: Terrascan uses Rego language for policies, terraform-compliance uses Gherkin syntax.
- Integration: terraform-compliance integrates more tightly with Terraform workflow, while Terrascan offers broader CI/CD integrations.
- Community: terraform-compliance has a more active community specifically for Terraform users.
- Customization: terraform-compliance allows for easier custom rule creation using natural language, while Terrascan requires more technical expertise for custom policies.
Both tools are valuable for ensuring IaC security and compliance, with the choice depending on specific project needs and team expertise.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME

terraform-compliance
terraform-compliance is a lightweight, security and compliance focused test framework against terraform to enable negative testing capability for your infrastructure-as-code.
- compliance: Ensure the implemented code is following security standards, your own custom standards
- behaviour driven development: We have BDD for nearly everything, why not for IaC ?
- portable: just install it from
pipor run it viadocker. See Installation - pre-deploy: it validates your code before it is deployed
- easy to integrate: it can run in your pipeline (or in git hooks) to ensure all deployments are validated.
- segregation of duty: you can keep your tests in a different repository where a separate team is responsible.
- why ?: why not ?
Performance
If terraform-compliance is not running quickly enough make sure to check the optional faster_parsing pip install flag in the Installation Guide
Idea
terraform-compliance mainly focuses on negative testing instead
of having fully-fledged functional tests that are mostly used for
proving a component of code is performing properly.
Fortunately, terraform is a marvellous abstraction layer for any API
that creates/updates/destroys entities. terraform also provides the
capability
to ensure everything is up-to-date between the local configuration and the remote API(s) responses.
Given the fact, terraform is used mostly against Cloud APIs, what was missing is to ensure
your code against your infrastructure must follow specific policies. Currently HashiCorp provides
Sentinel for Enterprise Products. terraform-compliance is providing a
similar functionality only for terraform while it is free-to-use and it is Open Source.
E.g. a sample policy could be, if you are working with AWS, you should not create an S3 bucket,
without having any encryption. Of course, this is just an example which may or not be applicable
for your case.
terraform-compliance provides a test framework to create these policies that will be executed against
your terraform plan in a context where both
developers and security teams can understand easily while reading it, by applying Behaviour Driven
Development Principles.
As returning back to the example, our example defined above will be translated into a BDD Feature and Scenario, as also seen in below ;
if you are working with AWS, you should not create an S3 bucket, without having any encryption
translates into ;
Given I have AWS S3 Bucket defined
Then it must contain server_side_encryption_configuration
server_side_encryption_configuration is coming from the terraform code, as shown below ;
resource "aws_s3_bucket" "b" {
bucket = "my-bucket"
acl = "private"
server_side_encryption_configuration {
rule {
apply_server_side_encryption_by_default {
kms_master_key_id = "${aws_kms_key.mykey.arn}"
sse_algorithm = "aws:kms"
}
}
}
}
This policy ( Scenario ) will allow all S3 buckets newly created or updated must have encryption configuration set within the code. In an ideal way, this Scenario (among with all other Scenarios) will run on a CI/CD pipeline that will ensure that nothing is deployed by violating your policies.
See Examples for more sample use cases.
Regarding the feature file format - radish is used to parse files with extension .feature - https://radish.readthedocs.io/en/stable/tutorial.html
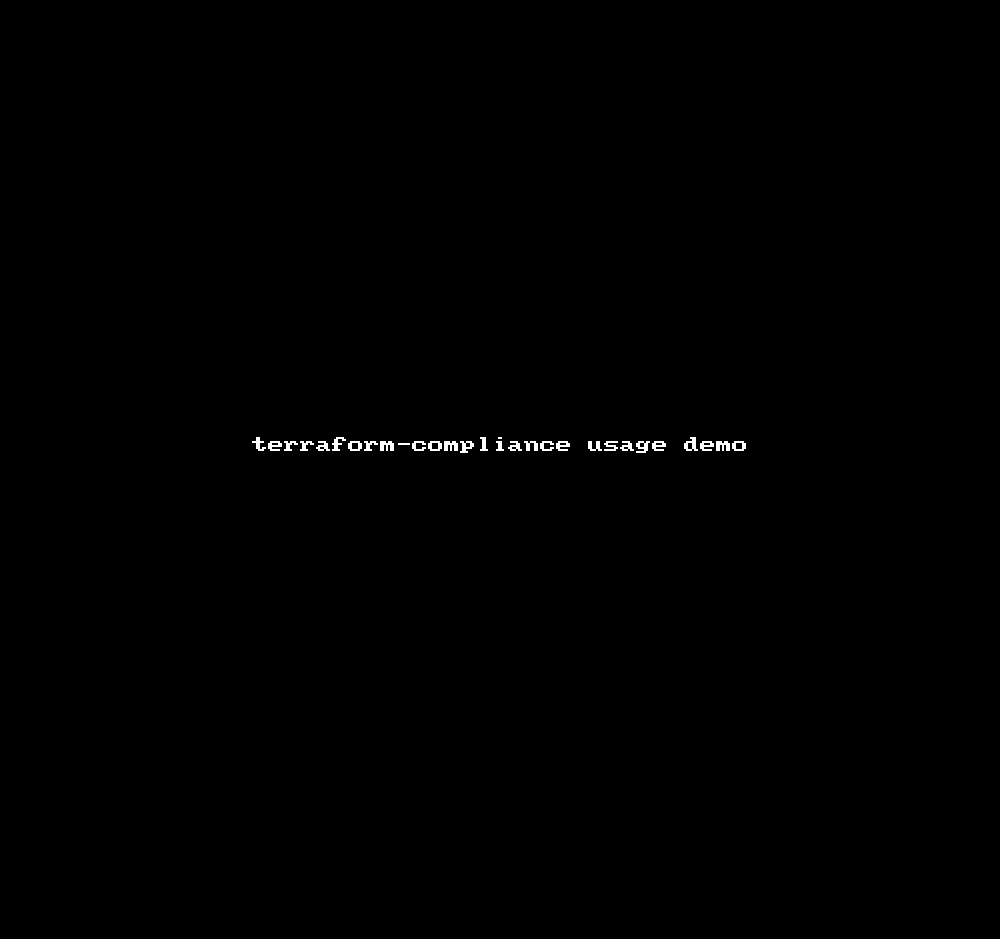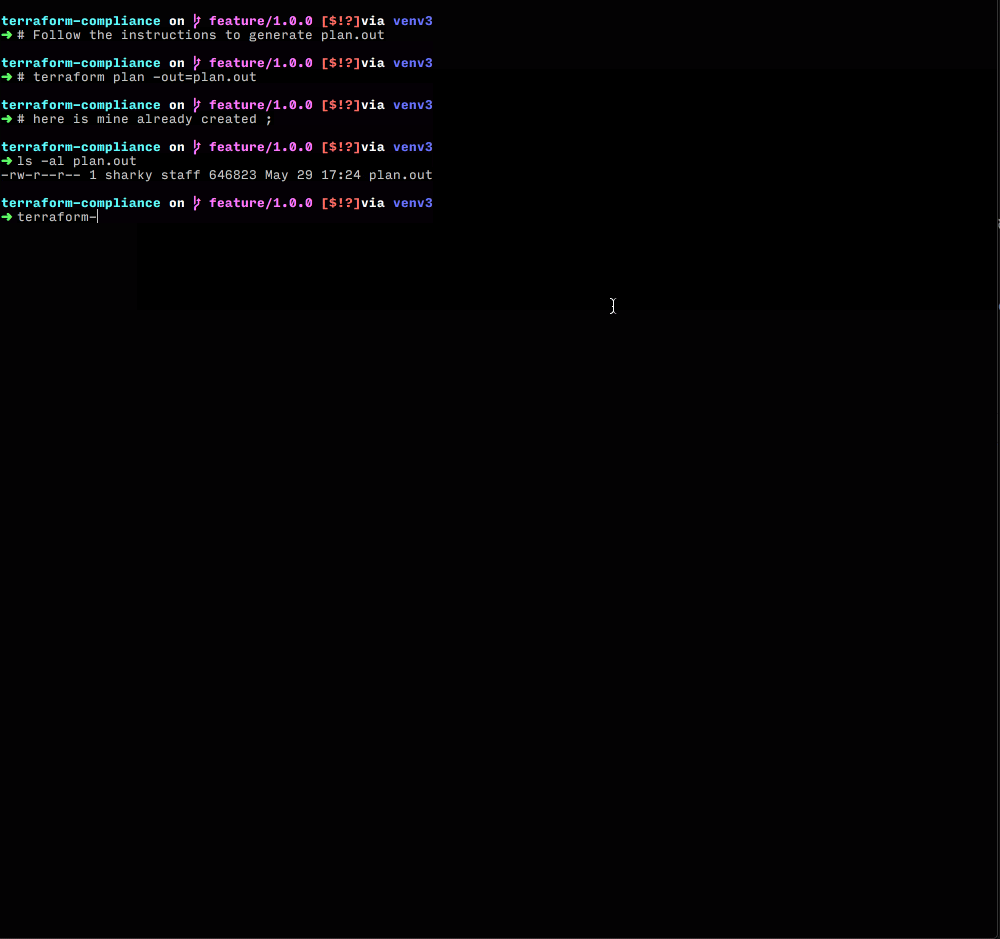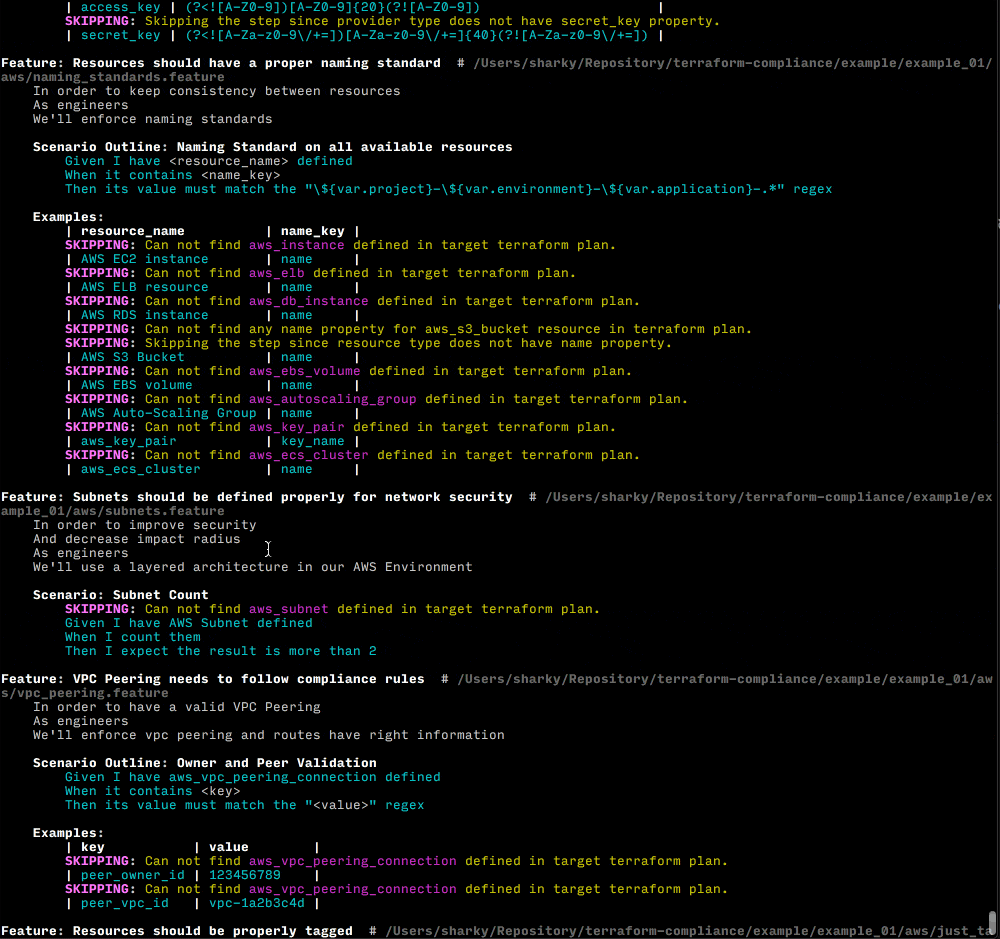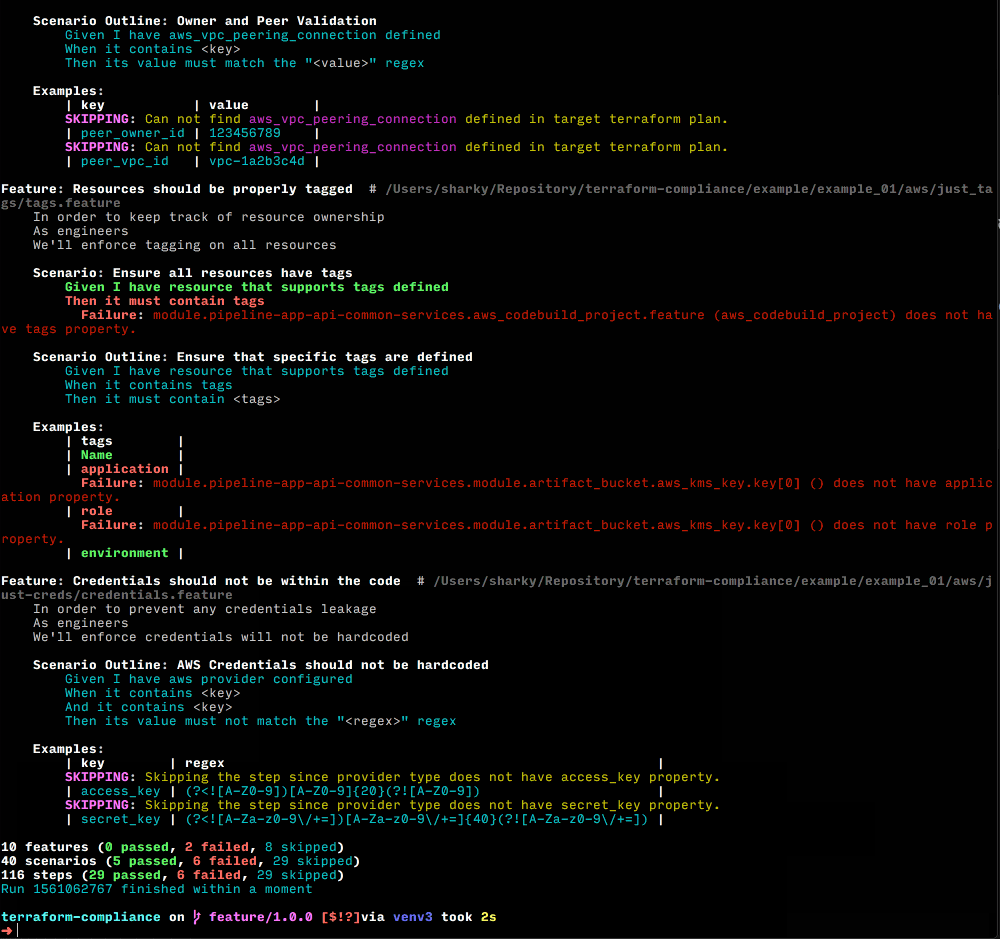
Sponsors
- resmo.com: Discover unmatched insights for Cloud and SaaS assets. Use SQL to ask questions and get real-time notifications for security and compliance violations.
License
Top Related Projects
Prevent cloud misconfigurations and find vulnerabilities during build-time in infrastructure as code, container images and open source packages with Checkov by Bridgecrew.
Tfsec is now part of Trivy
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot


