 linux-smart-enumeration
linux-smart-enumeration
Linux enumeration tool for pentesting and CTFs with verbosity levels
Top Related Projects
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Scripted Local Linux Enumeration & Privilege Escalation Checks
Linux privilege escalation auditing tool
Privilege Escalation Project - Windows / Linux / Mac
Quick Overview
Linux Smart Enumeration (LSE) is a powerful reconnaissance tool designed for Linux systems. It helps penetration testers and system administrators gather detailed information about the target system, including user privileges, running services, network configurations, and potential security vulnerabilities.
Pros
- Comprehensive system enumeration with minimal dependencies
- Color-coded output for easy interpretation of results
- Customizable verbosity levels for different levels of detail
- Actively maintained and regularly updated
Cons
- May trigger antivirus or intrusion detection systems
- Requires root privileges for full functionality
- Can be resource-intensive on older systems
- Output may be overwhelming for inexperienced users
Getting Started
To use Linux Smart Enumeration:
-
Download the script:
wget https://raw.githubusercontent.com/diego-treitos/linux-smart-enumeration/master/lse.sh -
Make it executable:
chmod +x lse.sh -
Run the script:
./lse.sh
For more detailed output, use the -l2 flag:
./lse.sh -l2
To focus on specific areas, use the appropriate flags:
./lse.sh -s sys,usr,net
Remember to run with sudo or as root for full functionality:
sudo ./lse.sh
Competitor Comparisons
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Pros of PEASS-ng
- More comprehensive suite of tools for privilege escalation and system enumeration
- Supports multiple operating systems (Linux, Windows, macOS)
- Actively maintained with frequent updates and contributions
Cons of PEASS-ng
- Larger codebase, potentially more complex to use and understand
- May have a steeper learning curve for beginners
- Could be overkill for simpler enumeration tasks
Code Comparison
PEASS-ng (linpeas.sh):
if [ "$MACPEAS" ]; then
print_title "MacPEAS"
printf "%s" "$MACPEAS"
elif [ "$LINPEAS" ]; then
print_title "LinPEAS"
printf "%s" "$LINPEAS"
linux-smart-enumeration (lse.sh):
lse_header() {
echo "LSE Version: $VERSION"
echo "User: $lse_user"
echo "OS: $lse_distro"
echo "Architecture: $lse_arch"
echo "Hostname: $lse_hostname"
}
Both tools use shell scripting for their core functionality, but PEASS-ng appears to have a more modular approach with separate scripts for different operating systems. linux-smart-enumeration focuses solely on Linux systems with a more straightforward structure.
Scripted Local Linux Enumeration & Privilege Escalation Checks
Pros of LinEnum
- More comprehensive and detailed output, covering a wider range of system information
- Includes additional checks for potential privilege escalation vectors
- Actively maintained with regular updates and contributions from the community
Cons of LinEnum
- Slower execution time due to more extensive checks
- May produce verbose output that can be overwhelming for beginners
- Less focus on SMART prioritization of results
Code Comparison
LinEnum:
#!/bin/bash
version="0.982"
#A script to enumerate local information from a Linux host
linux-smart-enumeration:
#!/bin/sh
#A smart Linux enumeration tool
export LSE_VERSION="4.9"
Both scripts are written in shell scripting languages, with LinEnum using Bash and linux-smart-enumeration using POSIX sh. The main difference in the initial code is that linux-smart-enumeration sets an environment variable for its version, while LinEnum declares it as a regular variable.
LinEnum tends to have more extensive and detailed checks throughout its codebase, while linux-smart-enumeration focuses on prioritizing and categorizing results based on their potential impact.
Linux privilege escalation auditing tool
Pros of linux-exploit-suggester
- Focuses specifically on identifying potential kernel exploits
- Provides detailed information about each suggested exploit
- Regularly updated with new exploit information
Cons of linux-exploit-suggester
- Limited scope compared to linux-smart-enumeration's broader system analysis
- May require more manual interpretation of results
- Less emphasis on general system information gathering
Code Comparison
linux-exploit-suggester:
#!/bin/bash
# Example of exploit suggestion
if [[ "$kernel" == "2.6.22" ]]; then
echo "Potential exploit: CVE-2009-2692 (sock_sendpage)"
fi
linux-smart-enumeration:
#!/bin/bash
# Example of system enumeration
echo "=== System Information ==="
uname -a
echo "=== User Information ==="
id
The code snippets illustrate the different focus areas of each tool. linux-exploit-suggester concentrates on identifying specific kernel vulnerabilities, while linux-smart-enumeration provides a broader overview of system information.
Both tools are valuable for security assessments, with linux-exploit-suggester being more specialized for kernel exploit identification and linux-smart-enumeration offering a comprehensive system enumeration approach.
Privilege Escalation Project - Windows / Linux / Mac
Pros of BeRoot
- Cross-platform support (Windows, Linux, macOS)
- More comprehensive privilege escalation checks
- Active development and regular updates
Cons of BeRoot
- Requires Python to be installed on the target system
- Larger codebase, potentially slower execution
- May be more easily detected by security software
Code Comparison
BeRoot (Python):
def check_suid_bin():
suid = []
for path in os.environ['PATH'].split(':'):
for file in os.listdir(path):
try:
if os.stat(os.path.join(path, file)).st_mode & stat.S_ISUID:
suid.append(os.path.join(path, file))
except:
pass
return suid
linux-smart-enumeration (Shell):
lse_get_suid() {
lse_test "$1" "suid_binaries" "ls -l \$(find / -perm -4000 -type f 2>/dev/null) 2>/dev/null"
}
The BeRoot code is more verbose and uses Python's os module for file operations, while linux-smart-enumeration uses a concise shell command to find SUID binaries. BeRoot's approach may be more flexible and easier to extend, but linux-smart-enumeration's method is simpler and doesn't require Python.
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual CopilotREADME
First, a couple of useful oneliners ;)
wget "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -O lse.sh;chmod 700 lse.sh
curl "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -Lo lse.sh;chmod 700 lse.sh
Note that since version 2.10 you can serve the script to other hosts with the -S flag!
linux-smart-enumeration
Linux enumeration tools for pentesting and CTFs
This project was inspired by https://github.com/rebootuser/LinEnum and uses many of its tests.
Unlike LinEnum, lse tries to gradualy expose the information depending on its importance from a privesc point of view.
What is it?
This shell script will show relevant information about the security of the local Linux system, helping to escalate privileges.
From version 2.0 it is mostly POSIX compliant and tested with shellcheck and posh.
It can also monitor processes to discover recurrent program executions. It monitors while it is executing all the other tests so you save some time. By default it monitors during 1 minute but you can choose the watch time with the -p parameter.
It has 3 levels of verbosity so you can control how much information you see.
In the default level you should see the highly important security flaws in the system. The level 1 (./lse.sh -l1) shows
interesting information that should help you to privesc. The level 2 (./lse.sh -l2) will just dump all the information it
gathers about the system.
By default it will ask you some questions: mainly the current user password (if you know it ;) so it can do some additional tests.
How to use it?
The idea is to get the information gradually.
First you should execute it just like ./lse.sh. If you see some green yes!, you probably have already some good stuff to work with.
If not, you should try the level 1 verbosity with ./lse.sh -l1 and you will see some more information that can be interesting.
If that does not help, level 2 will just dump everything you can gather about the service using ./lse.sh -l2. In this case you might find useful to use ./lse.sh -l2 | less -r.
You can also select what tests to execute by passing the -s parameter. With it you can select specific tests or sections to be executed. For example ./lse.sh -l2 -s usr010,net,pro will execute the test usr010 and all the tests in the sections net and pro.
Use: ./lse.sh [options]
OPTIONS
-c Disable color
-i Non interactive mode
-h This help
-l LEVEL Output verbosity level
0: Show highly important results. (default)
1: Show interesting results.
2: Show all gathered information.
-s SELECTION Comma separated list of sections or tests to run. Available
sections:
usr: User related tests.
sud: Sudo related tests.
fst: File system related tests.
sys: System related tests.
sec: Security measures related tests.
ret: Recurren tasks (cron, timers) related tests.
net: Network related tests.
srv: Services related tests.
pro: Processes related tests.
sof: Software related tests.
ctn: Container (docker, lxc) related tests.
cve: CVE related tests.
Specific tests can be used with their IDs (i.e.: usr020,sud)
-e PATHS Comma separated list of paths to exclude. This allows you
to do faster scans at the cost of completeness
-p SECONDS Time that the process monitor will spend watching for
processes. A value of 0 will disable any watch (default: 60)
-S Serve the lse.sh script in this host so it can be retrieved
from a remote host.
Is it pretty?
Usage demo
Also available in webm video

Level 0 (default) output sample
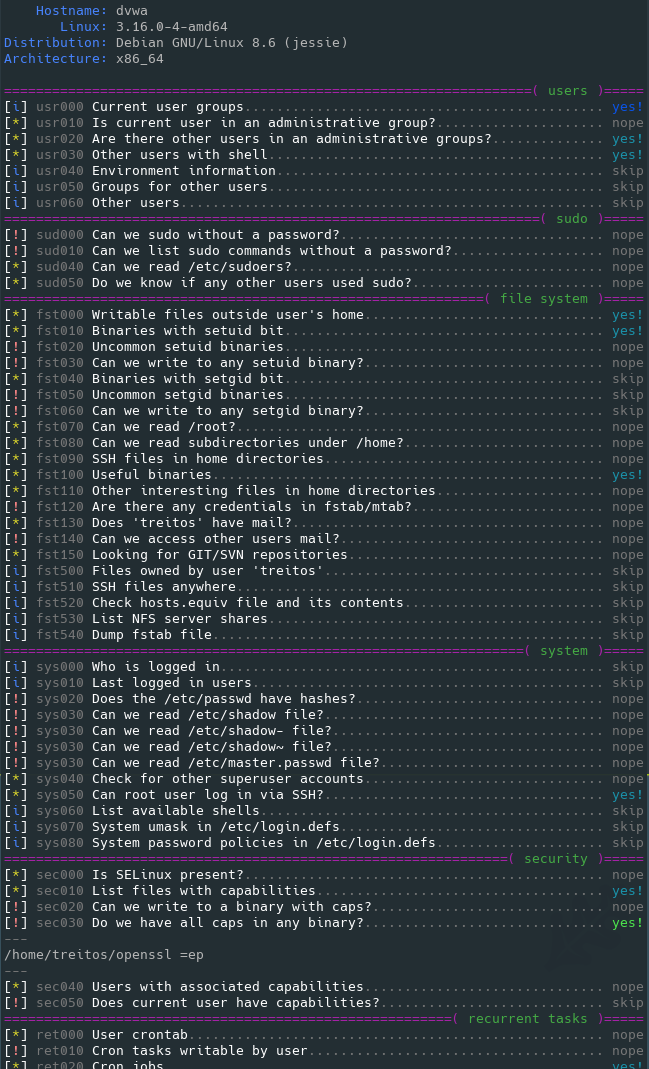
Level 1 verbosity output sample
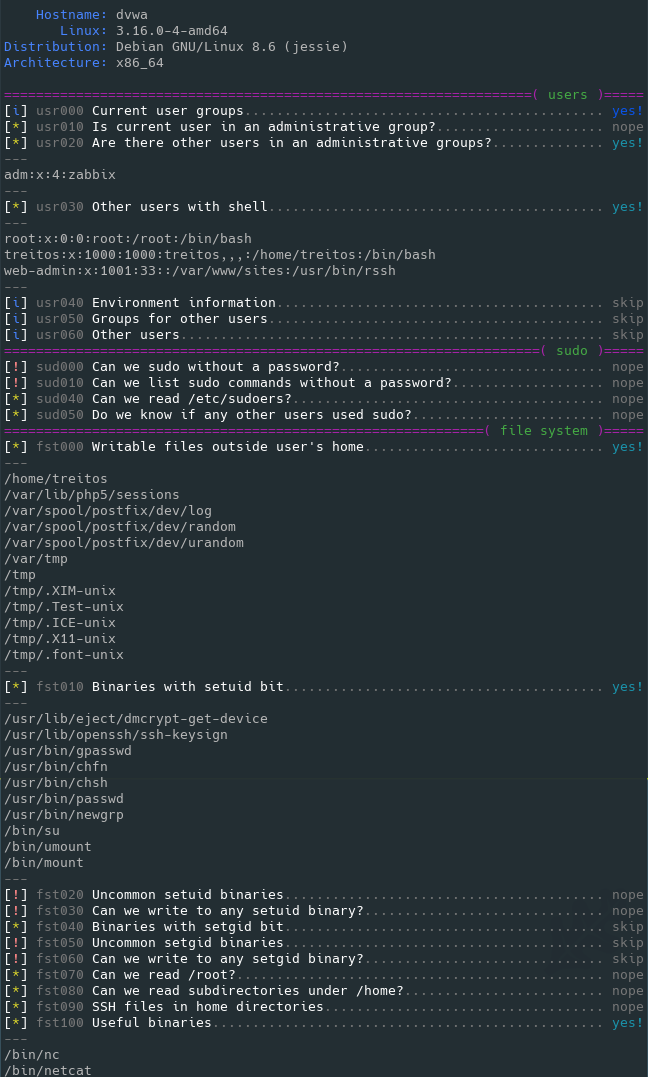
Level 2 verbosity output sample
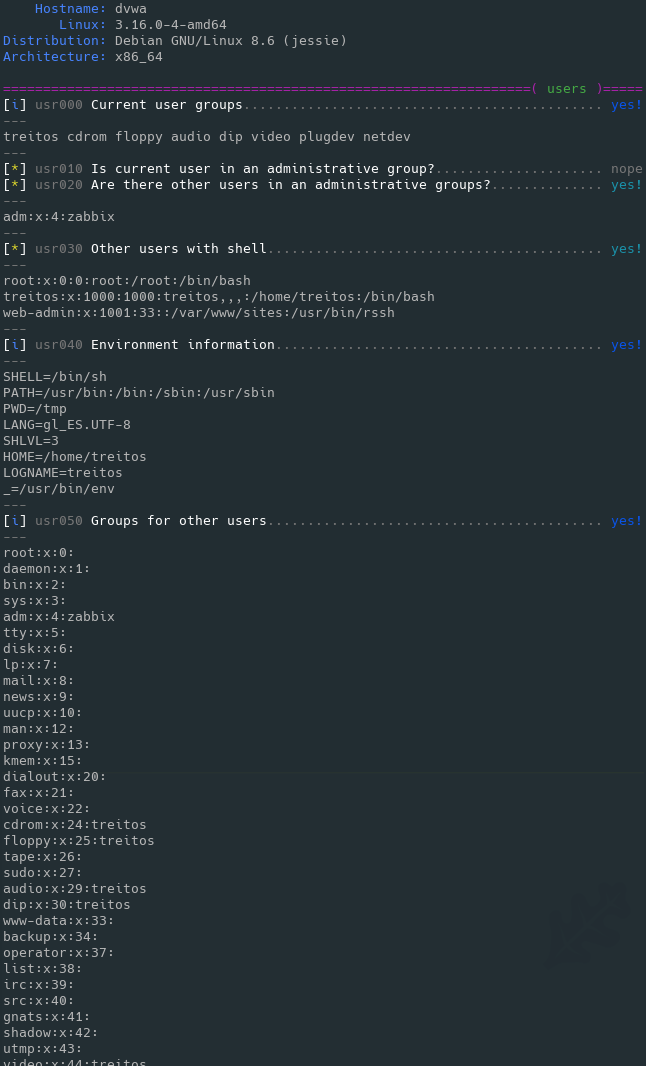
Examples
Direct execution oneliners
bash <(wget -q -O - "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh") -l2 -i
bash <(curl -s "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh") -l1 -i
Buy me a beer
Feel free to buy me a beer if this script was useful :)
â¿: 1DNBZRAzP6WVnTeBPoYvnDtjxnS1S8Gnxk
Top Related Projects
PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
Scripted Local Linux Enumeration & Privilege Escalation Checks
Linux privilege escalation auditing tool
Privilege Escalation Project - Windows / Linux / Mac
Convert  designs to code with AI
designs to code with AI

Introducing Visual Copilot: A new AI model to turn Figma designs to high quality code using your components.
Try Visual Copilot